Sometimes, a security incident starts with an email. A suspicious email can be provided to a security analyst for further investigation. Most of the time, the mail is provided in EML or “Electronic Mail Format“. EML files store the complete message in a single file: SMTP headers, mail body and all MIME content. Opening such file in a mail client can be dangerous if dynamic content is loaded (remember the EFAIL vulnerability disclosed a few days ago?) and reading a big file in a text editor is not easy to quickly have an overview of the mail content. To help in this task, I wrote a Python script that parses an EML file and generates a PNG image based on its content. In a few seconds, an analyst will be able to “see” what’s in the mail and can decide if further investigation is useful. Here is an example of generated image:
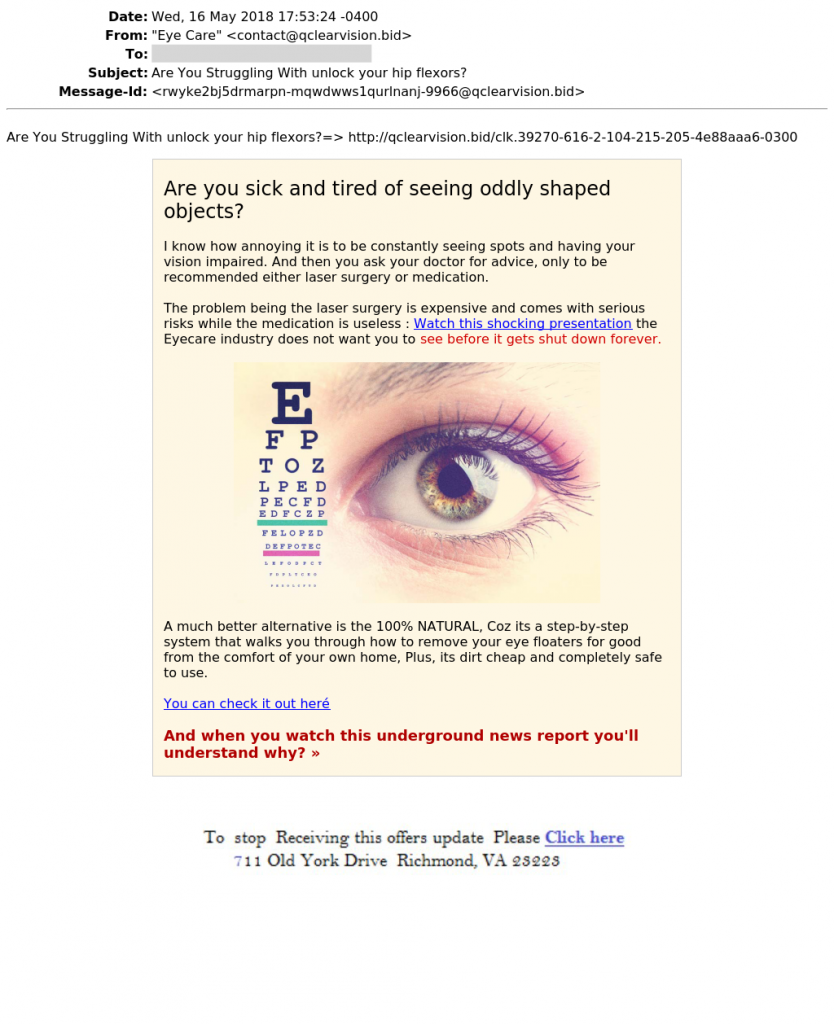 The script reads SMTP headers and extracts the most important ones. It extracts the body and MIME part “text/plain”, “text/html”. Attached images are decoded and displayed. If other MIME parts are found, they are just listed below the email. The image is generated using wkhtmltoimage and requires some dependencies. For an easier development, I build a Docker container ready to use:
The script reads SMTP headers and extracts the most important ones. It extracts the body and MIME part “text/plain”, “text/html”. Attached images are decoded and displayed. If other MIME parts are found, they are just listed below the email. The image is generated using wkhtmltoimage and requires some dependencies. For an easier development, I build a Docker container ready to use:
$ git pull rootshell/emlrender $ git run emlrender/rootshell
The container runs a web service via HTTPS (with a self-signed certificate at the moment). It provides a classic web interface and a REST API. Once deployed, the first step is to configure users to access the rendering engine. Initialize the users’ database with an ‘admin’ user and create additional users if required:
$ curl -k -X POST -d '{"password":"strongpw"}' https://127.0.0.1/init
[{"message": "Users database successfully initialized"}, {"password": "strongpw"}]
$ curl -k -u admin:secretpw -X POST -d '{"username":"john", "password":"strongpw"}' https://127.0.0.1/users/add
[{"message": "Account successfully created", "username": "john", "password": "strongpw"}]
Note: if you don’t provide a password, a random one will be generated for you.
The REST API provides the following commands and names are explicit:
- POST /init
- GET /users/list
- POST /users/add
- POST /users/delete
- POST /users/resetpw
To render EML files, use the REST API or a browser. Via the REST API:
$ curl -k -u john:strongpw -F file=@"spam.eml" -o spam.png https://127.0.0.1/upload $ curl -k -u john:strongpw -F file=@"malicious.zip" -F password=infected \ -o malicious.png https://127.0.0.1/upload
You can see that EML files can be submitted as is or in a ZIP archive protected by a password (which is common when security analysts exchange samples)
Alternatively, point your browser to https://127.0.0.1/upload/. A small help page is available at https://127.0.0.1/help/: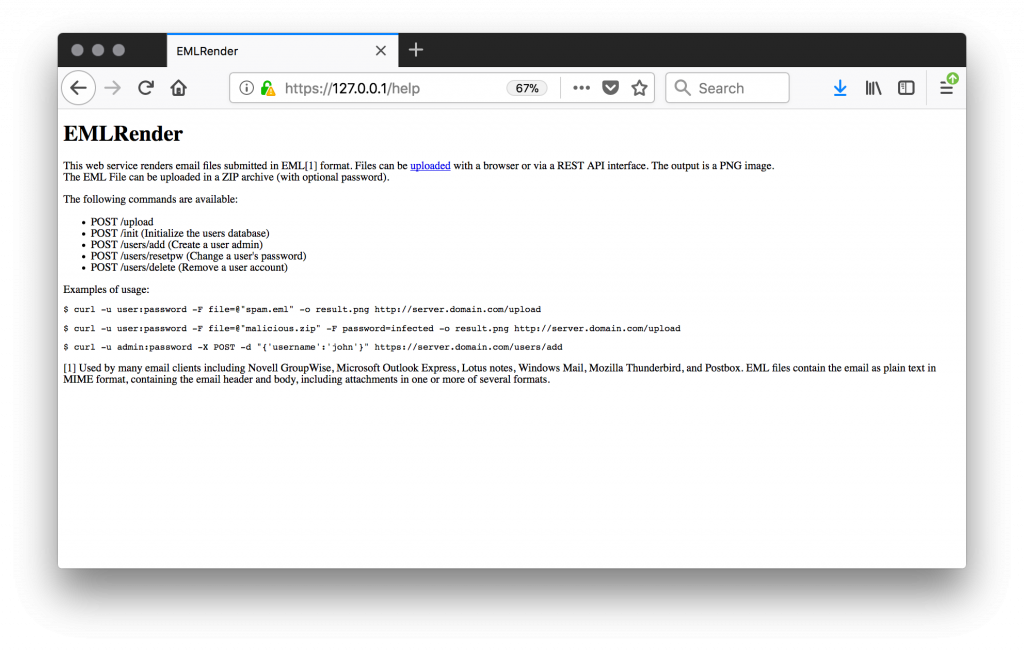
EMLRender is not a sandbox. If links are present in the HTML code, they will be visited. It is recommended to deploy the container on a “wild” Internet connection and not your corporate network.
The code is available on my GitHub repository and a ready-to-use Docker image is available on Docker hub. Feel free to post improvement ideas!

What’s the point with EFAIL? If you pass an encrypted email to the tool, it will list the encrypted MIME part at the bottom of the output.
So now the EFAIL attacker gets the unencrypted content as rendered PNG files?
Ok well. I guess having to do OCR* is more difficult than launching notepad.exe to read the secret contents of the encrypted e-mail.
* https://github.com/tesseract-ocr/