 When my friend Didier Stevens contacted me last year to help him with a BruCON 5×5 project, I simply could not decline! Didier developed a framework to perform forensic investigations on Cisco routers. His framework is called NAFT (“Network Appliance Forensic Toolkitâ€). It is written in Python and provides a good toolbox to extract juicy information from routers memory. From a development point of view, the framework was ready but Didier has the great idea to prepare a workshop to train student to analyze router memory images. The 5×5 project was accepted and thanks to the support of BruCON, it was possible to buy a bunch of Cisco routers to let students play with them. Why hardware routers and not simply a virtual lab (after all we are living in the virtualisation era)? For two main reasons: To avoid licensing issues and a virtual lab does not offer the ROMMON feature which is very useful to take a memory image of the router. The very first workshop was given last week during BruCON as a first premiere. With a fully booked room of people (40), it was a success and we already got good feedbacks. But not all people are able to attend security conferences and workshops, that’s why Didier had the idea to implement an online lab where registered people could perform the same investigations as in the live workshop. That’s where I was involved in the project!
When my friend Didier Stevens contacted me last year to help him with a BruCON 5×5 project, I simply could not decline! Didier developed a framework to perform forensic investigations on Cisco routers. His framework is called NAFT (“Network Appliance Forensic Toolkitâ€). It is written in Python and provides a good toolbox to extract juicy information from routers memory. From a development point of view, the framework was ready but Didier has the great idea to prepare a workshop to train student to analyze router memory images. The 5×5 project was accepted and thanks to the support of BruCON, it was possible to buy a bunch of Cisco routers to let students play with them. Why hardware routers and not simply a virtual lab (after all we are living in the virtualisation era)? For two main reasons: To avoid licensing issues and a virtual lab does not offer the ROMMON feature which is very useful to take a memory image of the router. The very first workshop was given last week during BruCON as a first premiere. With a fully booked room of people (40), it was a success and we already got good feedbacks. But not all people are able to attend security conferences and workshops, that’s why Didier had the idea to implement an online lab where registered people could perform the same investigations as in the live workshop. That’s where I was involved in the project!
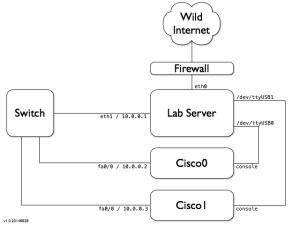
Here are a few words about the lab that has been deployed. It is based on a hardened Linux server and two Cisco 2610 routers connected together. The private network is available to generate some IP traffic. The routers serial consoles are also connected. Here is a small schema of the lab:
The Cisco routers can be managed via a telnet connection or via their console port. All tools are pre-installed to perform the memory dump analysis:
- The NAFT framework
- tcpdump
- tftp server/client
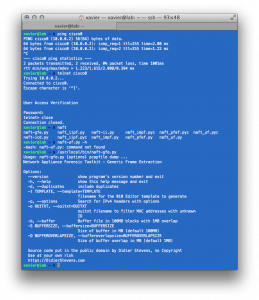
To access the lab, you just need a SSH client:
The lab is available to anybody who would like to test Didier’s framework. We also opened a website with information about the project and a booking system. You just have to select the day(s) and fill a small form. Once approved, a temporary account will be created and credentials will be sent.
Presented as an exclusivity during BruCON, Didier and myself are happy to announce that the lab is publicly available right now via router-forensics.net. If you’re interested in a workshop for your school, your event, feel free to contact us! We have routers ready on the road 😉 The next workshop has been scheduled during Hack.lu in Luxembourg.

One comment