
Last week, I was in Luxembourg for my day-to-day job and this week, I’m back for more fun (and some business too :-). It’s time for a new edition of hack.lu. This is already myfourth edition, time flies!
Like during the previous ones, the format remains the same: workshops during the first day (most of them are scheduled outside the normal tracks schedule) then a single track conference with international speakers. That’s a format I really like: You are able to attend good workshops and talks without conflicts. The benefit of one talk at a time: You don’t care about the risk to miss something interesting. And sometimes, you have very good surprises!
Let’s start with the workshops, I attended the one of Eireann Leverett (IOActive): “Global log file of (in)security“. Eireann presented the ShodanHQ search engine. How to explain what is Shodan? Imagine a Google but with only “technical” results about devices and applications directly facing the Internet. As resumed by Eireann, it’s “filtering the ocean of data“, I like this definition! Based on multiple filters (free text, host, net, city, country, port, os, before/after, geo, hostname, asn, title, isp (assigned/peered), html), you can search for interesting stuff about your potential victims. This is the perfect tool to start a reconnaissance phase prior to a pen test. Here is a perfect example of information returned by Shodan;
Then, the Shodan API was presented and how to integrate it with Python (the Python API is available here). It was very interesting and Eireann provided lot of tips to get the most of your requests. Shodan is a website that must be saved in your bookmarks.
After the lunch (and lot of discussions about multiple topics), the first talk was presented by Patrice Auffret about SinFP3. This is a Perl script developed to perform finger printing of operating systems.

But what is OS fingerprinting? Patrice’s definition is: “The art of remotely identify the nature of an OS by analysing how its TC/IP stack is crafting the network packets“. This task can be achieved in passive or active mode. But, wait a second, Nmap is also capable of detecting OS. Â Patrice explained what are its limitations. For Nmap, one target IP has only one OS and the set of probes is limited. There are potential problems like: spoofing, stateful inspection and normalisation, easy detection by IDS/IPS. According to Patrice, Nmap is only efficient in a LAN environment (speaking of OS finger printing of course – it remains the best network scanner ever). So, what is the SynFP3 approach? It was deeply described across multiple slides. If you are interesting, please have a look at the presentation when it will be published. It’s too long to report the methodology here. With SinFP3, during tests, only one TCP SYN could be enough to guess a target OS! Not bad. The tools is written in Perl with an architecture based on modules. It woks on IPv4/IPv6 and writes TCP packets at layer 4. Finally, a replay feature can read PCAP files generated from a previous network capture. Message from the speaker:Â To improve the passive scanning, more signatures are needed! Feel free to submit yours! The tools is available here.
The next speaker was Ivan Medvedev (from Microsoft). He presented “Security Tools for the SDL“. SDL is the “Security Development Lifecycle“. The goal is to write more secure pieces of code. SDL exists for years and his widely promoted by Microsoft. The current version is 5.2. The goal is this talk was to explain how to improve the SDL process with appropriate tools. What are those tools and how to implement them (guidance) and… use them! (that’s the most important afteral). Ivan demonstrated several tools provided by Microsoft to help developers to detect and fix vulnerabilities in their code.

Some tools execute the application, visit the website to get interesting information, others are pieces of code added to the source code at compilation time. Ivan presented and made demos of some interesting (well-known) tools like:
Nothing brand new but always interesting to have in your toolbox!
Victor Julien and Eric Leblond came to talk about  “The menace from below“. Victor started with a brief introduction of Suricata. Most important features are performance improvement (read: compared to Snort) with the help of multi-threading, protocol identification, file identification, extraction and on the fly MD5 calculation(!), TLS handshake analysis (to detect/prevent  issues like Diginotar) and support hardware acceleration support! I was not aware of the experimental support of Lua scripting to automate detection! That’s really a cool feature.

Still today, we have problems to filter some applications which use dynamic ports. The FTP protocol is maybe one of the best example. For the olders of us, the IRC file transfer using “DCC” is also a good one. For years, it has been difficult to handle properly such protocols on firewalls. To do this in an efficient way, you can use an “Application Level Gateway” (Example: PF in OpenBSD provides a ftp-proxy).  An ALG searches the traffic for command messages and extract information on the expected connections (ex: PORT command in the FTP prortocol). In Linux, ALGs are called Helpers and are implemented as kernel modules. There are several helpers, one for each protocol (FTP, SIP, H323, Amanda (backup), etc). Several demonstrations were presented (not live, via recorded sessions – always safer). One of them was a successful connection from an host on the Internet to the port 6000 of a NATed host behind a firewall. Amazing! How to protect against this? By implementing anti-spoofing. And, in 2012, this is not yet a standard configuration for some firewall vendors (Hello CheckPoint!). Then the speakers presented a tool called “opensvp“. Based on Python and Scapy (to manipulate IP packets), it has been developed to perform firewall attacks. The speakers again showed a proof-of-concept of a CheckPoint firewall configured “out-of-the-box“. They successfully accessed an internal host over port 22!  After the demos, they explained how Suricata can help to prevent such attacks with a set of interesting rules which perform DPI (“Deep Packet Inspection“). Simple example:
alert tcp ant any -> 192.168.1.0/24 21 (content: "USER root"; msg "Blah Blah Blah");
Conclusion of this talk? Today, the port is not important, check the content! Use DPI! Take care: Protocol analysis is not an easy task: High performance systems are required to implement the two-steps algorithm: classification then decoding. How to achieve this? Here are some tools: nDPI, l7-filter, NG firewalls. Some decoded protocols via Suricata. Decoding: Qosmos. nDPI looks a good start! Low layer attacks are still working: rp_filter does no support IPv6 and CheckPoint default setup is non secure. TTL’s can’t be followed easily. Conclusion: carefully select your contractors! They skills are top priority!
After a coffee break, a set of five talks was scheduled in one pass. Igor Skochinsky presented his research about the “Sony Reader Hacking Story“. Igor reviewed the different models manufactured by the giant vendor and how devices was successfully 0wn3d to run 3rd party (brewed) software, firmware reversed, etc. What I learned from this presentation:Â Sony used same private keys to decrypt and sign firm updates in some readers. The presentation was not very attractive (I mean no funny demos, screen shots) but the content of the slides was very interesting. It’s not easy to present the results of such research. When slides look easy, think about the days/weeks/months spent to perform the research! Respect! I talked with Ivan in the evening and asked him if Sony tried to get in touch with him about his work, I had one contact with the Sony PR but nothing else!
Next talk: “Android Security Buster” by Alex Atul. He started with a review of the security model used on the mobile phones (nothing new).
I wrote down an interesting stat: Current malware trends: 70% of them are sending premium SMS. Others are backdoors, trackers etc. They are very easy to develop.AV’s on Android? Based on the following news, yes it is! Â Most of them still rely on pattern matching. Creating multiple copies of the same malware takes seconds. Alex tried to make a demo of the FUD tool against multiple AV installed on his Android emulator. All of them were detected as malware and blocked. Strange…
Moti Jospeh spoke about “Memory Corruption Exploitation in Internet Explorer“. After booting his Macbook and the virtual machines, Moti started his presentation with a fact: Stack based overflow are impossible today in the last edition of Internet Explorer! If you read security notifications: They are all based on corrupted memory, dereference memory or “unspecified error“. Memory is the new attack vector. They are caused by bugs (like in any software).
Why hunting for bugs? They are multiple reasons: For fun, hack ,money or just the challenge! Why for the money? Because 0-day vulnerabilities have a real value: Adobe JBIG2 was sold for $75K by a Chinese guy. That’s “easy” money. Â How to hunt for memory corruption? Nothing new, fuzzing, binary auditing or surfing the web (yes!). To perform this, you need tools (debuggers & fuzzers). I like the quotation: “Programmer’s bug is hacker’s gold” Use Google Alert and search for “ie9 crash” 😉 Exploit is usable after free in 3 steps:
- What is the size of the freed obj?
- Spray the heap and fill the freed object
- Trigger the object, Code execution
An interesting tool showed by Moti: Microsoft Application Verifier. By reading the abstract, I was afraid to face lot of slides with assembler code but the presentation was really attractive. One of the best today! (IMHO)
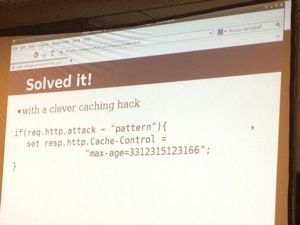
The next presentation was called “High Voltage Protection for Your Web Apps” by Edward Fjellskal and Kacper Wysocki and more precisely about “Varnish“. The idea of Varnish came from a business need: accelerating pages download from big web farms. It adds also flexible controls and transparency and some extra protections like: simple hackable rules, webscanners blocking. A good example is easily blocking a bot using IE with the “max-age” flag.
Why not simply use mod_security which is the well-know WAF for Apache (and IIS for a few months)? According to the speakers, it needs monitoring, support, integration, is sometimes overkill and will not protect against DDoS! And what about other WAFs? Not impressed, expensive, not flexible enough and no custom app rules. Â Instead: write rules! Small rulesets and custom rules for apps! The Varnish approach? A security rule framework in VCL with GET & POST rules, common malicious access, SQLi, XSS, cloaking. What are the differences between VCL & mod_security: Writeing VFW rules is like programming, easy to read, compared to mod_sec. Handlers are available: reject, alert, redirect, offensive script, honeypot, block. What are the weaknesses? WAF evasion, WAD fingerprinting, WAF spray. If you are dealing with WAFs (fighting?) , you definitively must have a look at this project.
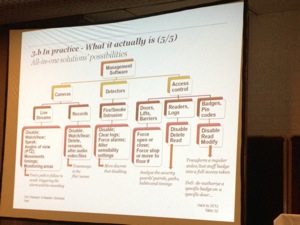
Last talk for today: “Insecurity of security equipments” by Eric Chassard & Maxime Clementz (PWC). Why this topic? During pen tests, speakers detected lot of physical security devices available on the network (not physical pen tests!). Those devices use technologies not common so they managed to write some exploits and attract attention on this issue. Hollywood movies have plenty of funny examples where doors are opened just by using a computer. But in the real life? Is it so easy? First, access control systems. Doors are (un)locked using RFID cards/readers. Behind the readers, there is a real IT infrastructure. Usually, the operator manages the DB via a web server. IP cameras and video recorders. Today, everything runs on IP and you’re forced to do so by vendors. Windows computers are often Windows XP and are connected to the domain with a layer of open source software (Tomcat, Apache, MySQL, etc). Controllers are closed-source specific electronic and firmware. Digital video recorders also runs on Windows OS. Often, without any control: “no access for support reasons” say Vendors. Why loose time to reverse the firmware? Read the licences details ;-). They are huge gaps between the “how it should be” and “how it is in reality” (no segmentation, IPcams are working on wireless networks, etc… No firewall, no AV, no password policy, no patches,… Such devices must be treated as any IT device. After the theory, some vendor solutions were reviewed with some (not all) details how to abuse them. It’s scaring to see how security is implemented… like 3DES password encryption with a key in clear text in the code (read: the same for all customers).
Some presentations are already available online. Check regularly for updates! The first day ended with the HAL party and open bar! It was a good opportunity to have very cool discussions with old as well as new friends! See you tomorrow for the second wrap-up!