
Here we go for the wrap-up of the second day! After a short night and some 0xC0FFEE, the schedule started with a keynote by Sharon Conheady about the “future of social engineering“. Sharon is a specialist in social extreme engineering (read: with physical access to facilities).
Did you know: The term “social engineering” was introduced in an essay in 1984! Why is social engineering important: Sport clubs, sauna, restaurant are many places where people talk about… business and can disclose confidential information!

Sharon started her keynote with some famous cases from the past. Social engineering is not new. She gave examples starting from 100 years ago. Victor Lustig was a first social engineer. He successfully sold the Eiffel tower a number of times because victims were too embarrassed to report to the police! To February 2012, when  a fake pilot was arrested in a cockpit. Did you know you can buy airline uniforms on eBay? You can even select the airline! And today, many attacks are successfully performed with the help of social engineering. What about the future? According to Sharon, we will remain with same tricks but with new technologies. The problem of scam and phishing was covered. Main difference with yesterday and today scams? They don’t come from Nigeria anymore but from your friends! Social networking is a step to social networking, it’s so easy to gather interesting data from your future victims. Technology can also be used to automate tasks! (Maltego, Metasploit to fake documents, SET, etc). Pwnphones are dedicated hardware to perform social engineering attacks. SEaaS (“Social Engineering as a Service“) is a reality. Outsource to professional callers with fake caller-ID and calling your victims during the business hours (Cost: $7-15 per call). Sharon’s keynote was awesome. So much interesting information. A must for security awareness!
The first regular talk was about IPv6: “The Layer-2 Insecurities of IPv6 and the mitigation techniques” by Eric Vyncke. Eric is a regular speaker about IPv6 in many conferences. He started with a situation of the IPv4 address space: We are out of IPv4 addresses. If you are not yet convinced, the message is clear: It’s time to take care of IPv6! Eric’s introduction can be resumed in one picture: “Networks are sand castles“

I attended Eric’s talk about IPv6 during RSA Europe two weeks ago. This time, he changed the slides to address a technical audience and went deeper in the explanations (ex: the rogue RA). Rogue RAs are really a big issue today. Eric gave a good example: Â One day when bored at the Brussels Airport (22h30), he played a bit and got 64 hosts sending traffic to his fake IPv6 router! Could you imagine how many hosts would be captured when people are waiting for their flights in the morning? After the fun, Eric explained how to mitigate this attack. Have a look at SEND (“Secure Neighbor Discovery Protocol“). Summary: Without a layer-2 security, there is no upper security. Rogue RA remains the major threat but they are mitigation techniques. Eric’s slides are available here.
After IPv6, back to malicious activity detection with Fyodor Yarochkin & Vladimir Kropotov who presented “Real-time malicious domain detection and malicious activity analysis“. They started with a review of current  trends in cyber-crime. Drive by download is still popular, email campaigns get bigger, social engineering and mobile play more and more an active role. Example of massive drive-by-download: rzd.ru (200K visitors/day). To conduct malicious campaigns, attackers register domain names (a lot of). By checking in whois databases, it’s possible to reveal interesting data. The speakers reviewed real examples. They showed many screenshots. Not only attackers stole your credentials, but when you contact the bank support, you use a high-rate phone number displayed in a fake banner! What about the evasion techniques? Drive by download is performed by “good” IP addresses (like subnets assigned to banks) then redirected to the real machine hosting the malicious code. Some domains are stolen. document.onmousemove = function() with JavaScript obfuscation. This is a method to avoid analyse in sandboxes. Typo-squatting domains is also a classic evasive method. Also detected: attacks via FTP. ftp://1572572686/Main.class.  They performed several demonstrations with some videos.

Finally, they explained how their tool work to gather interesting data from DNS. Do not check only DNS resolution in your logs but check also for errors! Based on the return code (2: non existent domain or 3: Â domain name server failed), you can generate interesting stats. Have a look at Fyodor’s tool dnslyzer available on github.
After a good lunch, it was the first lightning talks session. A friend of mine wrote our names on the list of speakers. Being an hostage ;-), I was forced to present my tool “pastemon” together with Christophe who started a fork of my tool in Python “pystemon“. We will for sure merge our two projects and work together in a near future…

The next talk was “Cypherpunks write code” (Hacking on Tor related projects) by Arturo Filasto & Aaron Gibson. After a small reminder about what is the Tor project (do we still have to present this tool?), they jumped to more technical details about the Tor infrastructure.

They explained deeply how this network “inside the network” works. The most interesting part was the review of many projects linked to Tor:
- Tor Button is a Firefox extension that “torifies” your connections.
- Vidalia is the default Tor GUI
- TorBirdy is used to forify Thunderbird (Thunderbird extension)
- Orbot is an Android Tor controller to torify applications on your phone
- Arm is a nurse interface for Tor
- txtorcon provides interaction with the Tor Control port, start and stop Tor clients, services.
- Atlas is used to search and view details on Tor relays
- Onionoo is the backend HTTP API to Atlas
- Metrics Portal generate all the statistics available on metrics.torproject.org
- TorFlow: Bandwifth authority
The next part of the presentation focussed on Tor Hidden Services? The goal is to hide service-side TCP services on Tor using the .onion TLD. In 2011, I wrote a blog post about this very interesting Tor feature. But things are evolving. Today,  APAF (“Anonymous Python Application Framework”) helps you  to create desktop oriented Tor Hidden Service driven & python based server side applications. Tor2web makes HTTP based Tor Hidden Services accessible from the “common” web. Shadow simulates the Tor network (very useful to test your applications on Tor).
Bad news, Will Allsop’s talk (“My life as an international arms dealer“) was cancelled. I really expected this one. Maybe the topic was too touchy? The schedule was updated. With the next talk, we came back to the first topic covered today: Social Engineering. Walter Belgers explained his vision on social engineering. His definition is “Persuading people to give sensitive information“. Best example ever: http://www.youtube.com/watch?v=oNW85BEmsCU or this other one reported on Twitter: http://www.youtube.com/watch?v=vJG698U2Mvo. How to perform social engineering? In three steps:
- Become an insider
- Preparation, collecting information about your target
- Talking the talk (learn the jargon!)
Today, forget dumpster diving, Internet is the new trash bin! (Read: social networks, search engines, etc). Classic examples of social engineering: “I lost my password and I need to finish an urgent job!” or “Here is the technical support,  could you please change your password to xxx?“. Walter reviewed multiple scenarios and how to handle your victims with shortcuts to automated responses:
- “It’s expensive, therefore it’s good“
- “He’s an expert, therefore he’s right“
Authorities can be faked using clothing or accessories.Commitment is important: “Will you make me a favour because I need it?” If the victim answers “Yes“, you win! Start by asking for a little, then for some more, and more, …
After a coffee break, Dropbox security was reviewed from a security point of view by Nicolas Ruff & Florian Ledoux. Dropbox faced lot of security incidents / configuration errors like not using SSL encryption on Smartphones (2011), a software upgrade issue provided free access to all user accounts for one day (2011). Stolen password of a Dropbox employee lead to massive spam (2012).

Why studying Dropbox? They have a leader position, no previous work was performed on this topic. Some “LAN sync” protocol routinely observed during pen tests and… because we are Dropbox users and would like to know how our data are protected! What about the clients? They are mostly written on Python (The Windows client is generated using py2exe). Source quest? Nicolas and Florian decompiled the Python binary using their uncompyle2 tool. So they had the source code and were able to inject Python code in the client. What about the configuration database? For Dropbox < 1.2, no encryption. Starting from 1.2, it was encrypted. What about the network protocols? Over HTTPS, OpenSSL + nCrypt wrapper and proper certificate checklist. OpenSSL is old and vulnerable to known CVE. nCrypr is buggy and unsupported since 2007. Synchronization is performed via Rsync to the Amazon S3 cloud. Details of the implementation: 4MB blocks size, SHA-256 of each blocksn. encryption is provided by SSL/TLS only. Different servers: block server, authserver, metaserver, metaexcservr / blockexcserver and stat server, notify server. Note that it’s possible to change the way communication is performed with those servers. What about the LAN sync protocol? Local sync of two Dropbox clients over UDP/17500 broadcasts. Data exchange occurs over TCP/17500. Each instance can act as a client or as a server. Authentication is performed over SSL/TLS. How to attack a client in server mode? The key pair is in the configuration DB! But, there is no certificate checks when attacking in client mode. Spoofing is possible!
The next presentation was about Android malware & forensics analysis by Kevin Allix & Quentin Jerome (University of Luxembourg). According to AV vendors, we must be scary and it could be better for us to buy their products! Good introduction… I was happily surprise of the approach the speakers used to analyse malwares on the Android platform. Instead of jumping into long pages of code, they analysed the patterns in metadata and certificates.  An interesting statistic: There are 1258 malwares known in the Genome project database. How to find malwares? It’s easy, just visit app stores! Common places are: Google Play, AppChina, Slideme, FreewareLovers, ProAndroid, Torrents(!) or Genome. The top-1 is AppChina with >63K apps available. Google comes in second place with >51K apps.
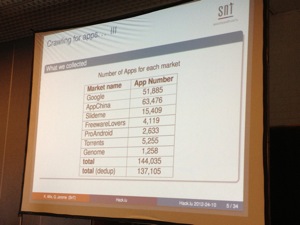
Applications are distributed as single .apk file. It’s a zip file that contains: Compiled code, manifest file, Resources (images, sounds). First questions: are they interesting patterns in metadata? And can we find different patterns for malware? (focus on packaging timestamps ad certificate). Â Based on the statistics, it seems logical that malware writes have tools to automate the packaging process. They also prefer to work on week-days (less malwares are packages on Saturday & Sunday). They also reuse certificates. (0.4% apps are using the same certificate in the Genome database). Upon 31K certificates used, only 31 were signed! Next step was how to use metadata to detect malwares? Multiple statistics were reviewed to try to categorise the origin of malwares. Interesting talk.
Cosmin Ciobanu from ENISA came to talk about “Honeypots, early warning systems”. What do CERTs to detect suspicious activity? They are two approaches: “reactive” and “proactive“.

Honeypots are part of the second one.They don’t have impact on the production environment. Honeypots might be different: low interaction, how interaction or hybrid. They can be classified in two other categories: opportunistic t(“low hanging fruit”) to targeted. If you want to play with your own honeypot, have a look at Dionaea. Very easy to deploy in the Amazon cloud. The CERT Polska had a nice project which had multiple benefits: early warning detection, detection of new exploits in the wild, vulnerabilities and malware behaviour, attackers vectors, etc… A paper is available here. Once you collected data, how to perform threat intelligence? You need tools to perform correlation. But honeypots have also issues: they are not easy to maintain, some tools are difficult to install on modern system, attackers are becoming smarter, they are easily identifiable using fingerprinting.
Finally, Jonathan Dechaux spoke about Microsoft documents (“The Office Demon; Minos“). Most Office applications can be used to conduct attacks today (Microsoft, Libre, Open). The purpose of Minos is to have a unique interface for all applications, cross-platform (developed using Qt) for statics and dynamic infection. How to exploit Office documents? The Macro security level can be set to different values. The behaviour is the same for all Office suites, just the location and flles/registry change. Once security level in place, how to infect a document? (static or dynamic). Collect documents from an USB device and add a Word or Excel macro. Documents were copied using the USB Dumper.
That’s all for today! Now, let’s have a dinner with Belgian friends…
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #2 http://t.co/Rq7N34Gg #hacklu