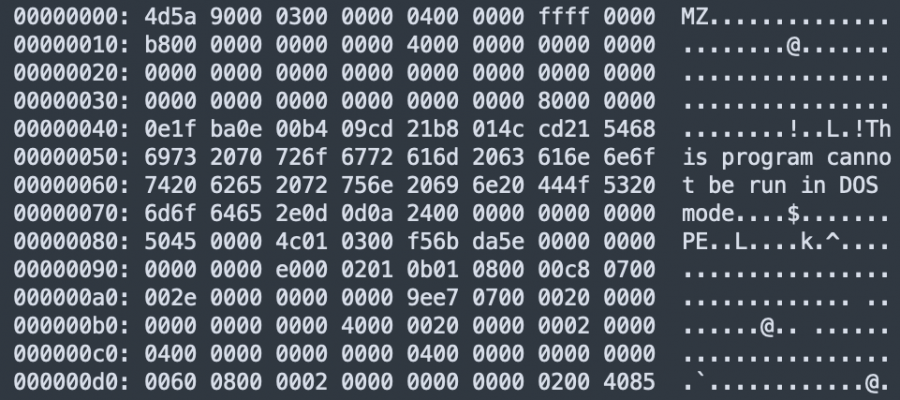
I published the following diary on isc.sans.edu: “Simple but Undetected PowerShell Backdoor“: For a while, most security people agree on the fact that antivirus products are not enough for effective protection against malicious code. If they can block many threats, some of them remain undetected by classic technologies. Here is