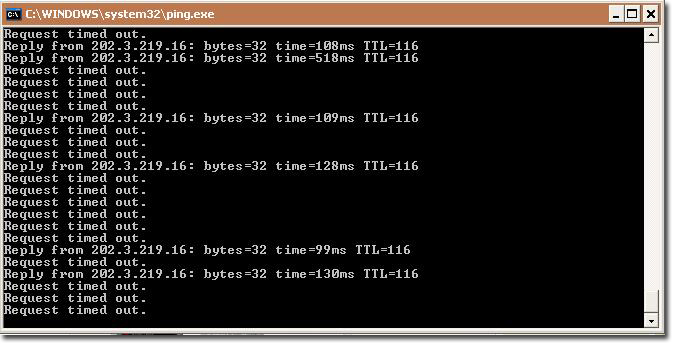
I published the following diary on isc.sans.edu: “Very Large Sample as Evasion Technique?“: Security controls have a major requirement: they can’t (or at least they try to not) interfere with normal operations of the protected system. It is known that antivirus products do not scan very large files (or just