A few weeks ago I wrote an ISC diary about a piece of malicious code that used ngrok.io to communicate with the C2 server. Just a quick reminder about this service: it provides a kind of reverse-proxy for servers or applications that people need to publish on the Internet. I knew the service for a while but how popular is it these days? What are people publishing? So, I wrote some Python code to have a look at *.tcp.ngrok.io. I focussed on HTTP traffic and, for each live service found, I took a screenshot.
ngrok.io is a good alternative to the classic NAT feature present in all residential routers because your IP address is hidden and you don’t have to play to dynamic DNS services to keep access to the published service when your IP address is renewed. But, like NAT, it is NOT a security feature and the service you publish must be hardened or restricted to authorized users.
I checked all ports (1-65535) for *.tcp.ngrok.io, collected screenshots and data returned by the discovered services. Here is a very small set of services found:
Most classic services:
- Plex servers
- Home automation
- Game servers
- Many types of “IoT” related stuff
- Proxies
- Development tools / services
- Miners
- Unconfigured services (Apache, Tomcat default pages)
- Administration pages
Most exotic ones:
- A BurpSuite instance
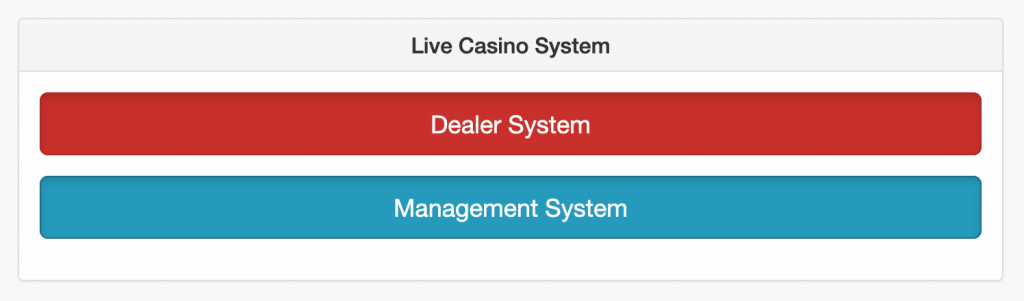
- A Casino interface system?
Note that I found also plenty of MongoDB databases!
