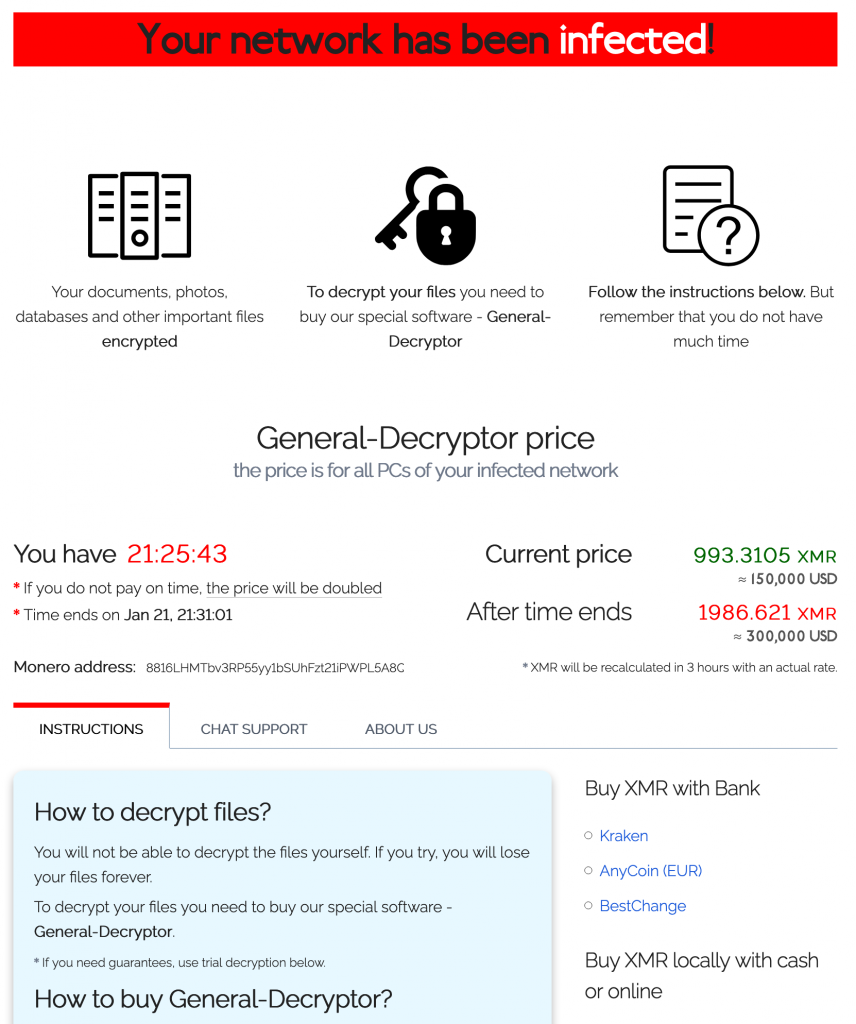
I published the following diary on isc.sans.edu: “Powershell Dropping a REvil Ransomware“:
I spotted a piece of Powershell code that deserved some investigations because it makes use of RunSpaces. The file (SHA256:e1e19d637e6744fedb76a9008952e01ee6dabaecbc6ad2701dfac6aab149cecf) has a very low VT score: only 1/59!.
The technique behind RunSpaces is helpful to create new threads on the existing Powershell process, and you can simply add what you need to it and send it off running. Here is an example of Runspace created by the malicious script… [Read more]