The popular web conference platform Zoom has been in the storm for a few weeks. With the COVID19 pandemic, more and more people are working from home and the demand for web conference tools has been growing. Vulnerabilities have been discovered in the Zoom client and, based on the fact that meetings were not properly secured, a new type of attack was also detected: Zoom Bombing.
Keep also in mind that Zoom, by design, allows attendees to exchange information via a chat session. Another vulnerability discovered was the leak of Windows credentials via UNC links. Recently, it appeared that 500K Zoom users‘ credentials were for sale on the dark web. Bad days for Zoom!
To protect against these issues, many sites started to explain how to harden your Zoom meetings. By example, by defining a password to join all meetings:
Good, you changed your default settings and you’re now safe. Are you sure? When you schedule a Zoom meeting, there are chances that you will send invites to attendees. Meeting requests are sent via a standard format “ICS” compatible with most of the calendar applications. These files attached to the invitation or can be downloaded via URLs. Consider them as regular files and, today, files are made to be processed, scanned, indexed, etc…
I created a YARA rule on VT to search for such files. Calendar invitations have not only a common extension but a common name: ‘invite.ics’. Here is the simple rule:
rule calendar_zoom
{
strings:
$s1 = "Join Zoom Meeting"
condition:
any of ($s*) and new_file and file_name == "invite.ics"
}
I added the rule yesterday and already collected 92 invitations. Detecting files in real-time is very nice because of the increased chances that the meeting will be organized in the future or be recurring! And all details are available in ICS files:
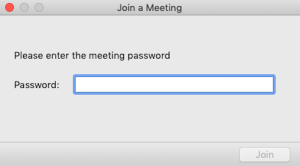
DESCRIPTION:xxx is inviting you to a scheduled Zoom meeting.\n\n\n\n Join Zoom Meeting\n\nhttps://zoom.us/j/xxxxxxxxxxx?pwd=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx\n\n\n\n Meeting ID: xxx xxx xxxx\n\nPassword: xxxxxx\n\n\n\n
We have the meeting URL, ID and… the password! We also have more interesting details like the organizer’s details:
ORGANIZER;CN=xxx xxx:mailto:xxx@xxx
When the meeting is scheduled:
BEGIN:VEVENT
DTSTART:20200417T183000Z
DTEND:20200417T200000Z
DTSTAMP:20200416T195346Z
But also attendees:
ATTENDEE
CUTYPE=INDIVIDUAL
ROLE=REQ-PARTICIPANT
PARTSTAT=NEEDS-ACTION
CN=xxx xxx
X-NUM-GUESTS=0:mailto:xxx@xxx
CN=xxx xxx
X-NUM-GUESTS=0:mailto:xxx@xxx
...
I found email addresses with very very interesting domain names from big companies or international organizations! This information is perfect to perform a social engineering attack. If an attendee receives an email from a Zoom event organizer with, by example, a malicious attachment, guess what he/she will do?
I also performed a retro hunt on VirusTotal and found 6000+ invite.ics files with Zoom meeting details! There are less relevant because most of them are outdated.
What about Google? Can we also find invitations indexed by the search engine? I tried some Google searches:
“Join Zoom Meeting” filetype:txt’ : 137 results
“Join Zoom Meeting” inurl:ics: 74 results
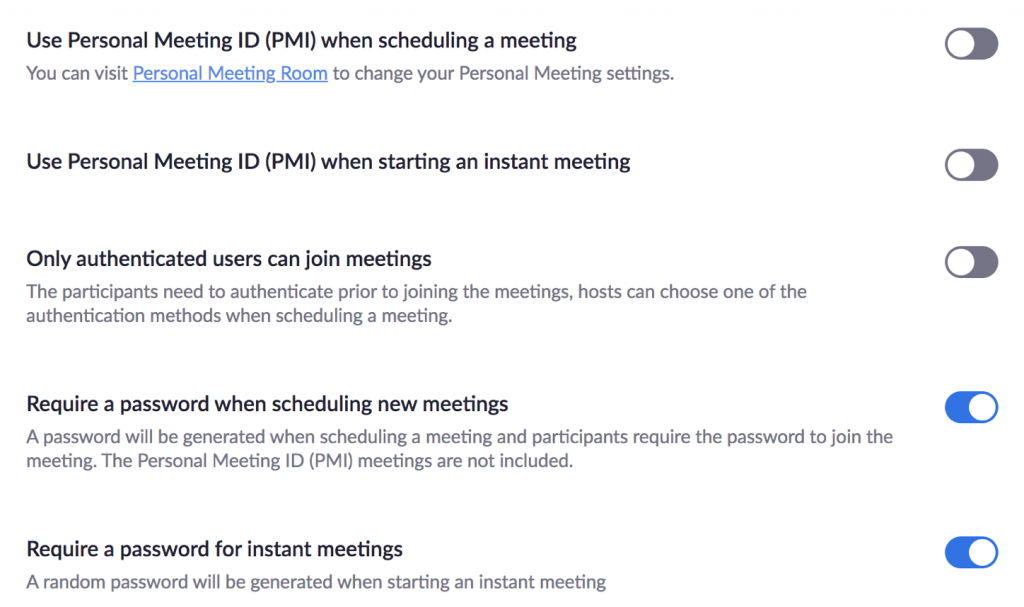
I found in my Zoom account settings that it’s possible to disable the generation of passwords for a single-click meeting:

The generated URL will be: ‘https://zoom.us/j/xxxxxxxxx’ with just the meeting ID. But the password is still sent in the invitation. It could be interesting to have an option to *NOT* send the password via this channel but via an alternative one…
Based on the files that I checked, 50% of the meetings do not have a password set…
One comment