In March during TROOPERS’18, I discovered a very nice tiny device developed by Luca Bongiorni (see my wrap-up here): The WiFi HID Injector. Just to resume what’s behind this name, we have a small USB evil device which offers: a Wireless access point for the configuration and exfiltration of data, an HID device simulating a keyboard (like a Teensy or Rubberducky) and a serial port. This is perfect for the Evil Mouse Project!
Just after the conference, I bought my first device and started to play with it. The idea is to be able to control an air-gapped computer and ex-filtrate data. The modus-operandi is the following:
- Connect the evil USB device to the victim’s computer or ask him/her to do it (with some social engineering tricks)
- Once inserted, the USB device adds a new serial port and fires up the wireless network
- The attacker, located close enough to get the wireless signal, takes control of the device, loads his payload
- The HID (keyboard) injects the payload by simulating keystrokes (like a Teensy) and executes it
- The payload sends data to the newly created serial port. Data will be saved to a flat file on the USB device storage
- The attack can download those files
By using the serial port, no suspicious traffic is generated by the host but the feature is, of course, available if more speed is required to exfiltrate data. Note that everything is configurable and the WHID can also automatically connect to another wireless network.
During his presentation, Luca explained how he weaponized another USB device to hide the WHID. For the fun, he chose to use a USB fridge because people like this kind of goodies. IMHO, a USB fridge will not fit on all types of desks, especially for C-levels… Why not use a device that everybody needs: a mouse.
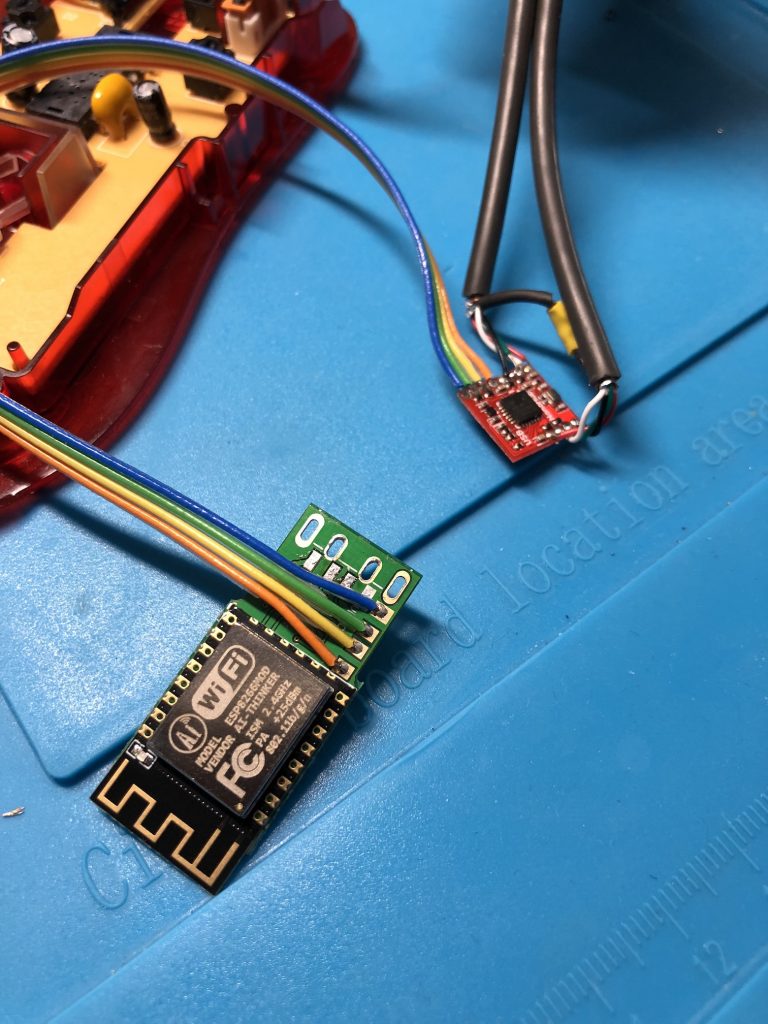
Hopefully, most USB mouses have enough inside space to hide extra cables and the WHID. To connect both USB devices on the same cable, I found a nano-USB hub with two ports:
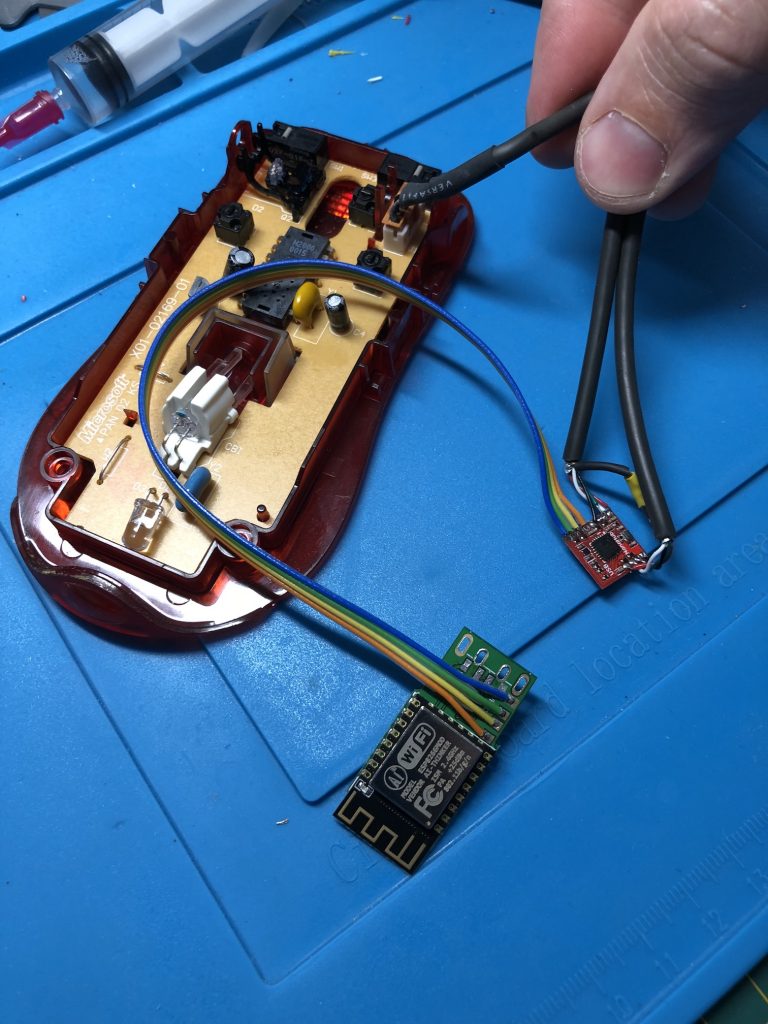
This device does a perfect job only on a 12x12mm circuit! I bought a second WHID device and found an old USB mouse ready to be weaponized to start a new life. The idea is the following: cut the original USB cable and solder it to the nano hub then reconnect the mouse and the WHID to the available ports (to gain some space, the USB connector was unsoldered.
My soldering-Fu is not good enough to assemble such small components by myself so my friend @doegox made a wonderful job as you can see from the pictures below. Thanks to him!
Once all the cables re-organized properly inside the mouse, it looks completely safe (ok, it is an old Microsoft mouse used for this proof-of-concept) and 100% ready to use. Just plug it in the victim’s computer and have fun:

If you need to build one for a real pentest or red-team exercise, here is a list of the components:
- A new mouse labelled with a nice brand – it will be even more trusted (9.69€) on Amazon
- A WHID USB device (13.79€) on AliExpress
- A nano-USB hub (8.38€) on Tindie
With this low price, you can leave the device on site, no need to recover it after the engagement. Offer it to the victim.
Conclusion: Never trust USB devices (and not only storage devices…)


Awesome Xavier!
WiFi allows the attacker to remain away from his/her target. Easy to detect but who cares in a city center when you have plenty of public hotspots? Is one extra suspicious?
WiFi is relatively easy to detect. How about hacking a bluetooth or infrared mouse and passing the data to exfiltrate over the device’s original channel?