 And here is the second day wrap-up. The day started with a sunny sky over Amsterdam. After a breakfast and a chat with the Help Net Security team, we moved to the rooms. Like yesterday, the main stage is dedicated to women for two keynotes. The first one should be Pamelo Fusco with her keynote title: “Behind the Crosswire†but she never arrived… No news from the speaker, maybe lost in the Amsterdam night life?
And here is the second day wrap-up. The day started with a sunny sky over Amsterdam. After a breakfast and a chat with the Help Net Security team, we moved to the rooms. Like yesterday, the main stage is dedicated to women for two keynotes. The first one should be Pamelo Fusco with her keynote title: “Behind the Crosswire†but she never arrived… No news from the speaker, maybe lost in the Amsterdam night life?
Then, Jennifer Steffens (CEO of IOActive) talked about “Hack It Forward†or “Making the world a better place, one great hack at a timeâ€. There are tons of Hollywood movies in which hackers see themselves. For years technology has been used in many scenarios. And hacker like this, some movies give also inspiration to people. But today, what we can see in movies is not science-fiction anymore. Things are real! And hackers are present in all media, they even have they own strips. Jennifer’s keynote started with the following quote by Confucius:
“Choose the job your love and you will never have to work a day in your lifeâ€
Jennifer broadcasted positive messages toward the InfoSec community in her keynote. Our job landscape changes daily, we have to face new attacks, our life is spied and technologies evolve. Jennifer don’t thing that we are lost. For her, it’s not chocking to see eBay (or any bit player on the Internet) in the news. This is only a consequence of how our world changes. We passed the following messages to the audience. Think outside the box and do things differently. But in reality, if it wasn’t hard, we were getting bored. We like challenges. This industry has limitless possibilities:
- Do great thing
- Make money
- have fun
- Rinse, repeat
We need to change the game and think differently. Security is an infinite game. It’s our job to make sure that there is always new stuff to do. Some examples of amazing researches:
- Car hacking
- ATMs
- Medical devices
- Satellites
- Nuclear bombs
- …
Another Jennifer’s quote:
“If you wan’t to change the InfoSec scene, get involved in InfoSecâ€
Hacking stuff must be seen as positive (it’s not always the case) and people must understand that it can improve our lives. A common problem with many researchers: they only speak in a closed environment and share their findings between them. Don’t be afraid to share your research with a broader audience: Show what you’ve done but don’t forget to adapt your communication.We need to get more attention from the consumers.
Other important points for Jennifer: Excuses are “bleeeeepâ€. Why say “It’s too hardâ€, “I don’t have moneyâ€, “I’m too oldâ€. There is no excuses in InfoSec. Just do it! Don’t forget to teach others. Nodoby paid attention to ATM’s before Barnaby Jack. You failed? Don’t worry, learn from your mistakes and try again. Keep in mind:
- “Hack with heart†– technology may affect “peopleâ€.
- Think differently.
- Speak the right language.Think about the impact and leave the technical details at the beginning. Come back with them later.
- Have fun.
- Start breaking things
- Got to know the community / ask questions
- Disclose responsibly (very important!)
- Be inspired!
You have a crazy idea? Start your project lile building a nuclear bomb?
The goal is make the world safer! Communicate with vendors, manufacturers. The last message from Jennifer: “I hope that you’ll leave HITB with many great ideasâ€. Very nice keynote!
The slides are available here.
For the regular talks, my first choice was “Alice’s Adventures in Smart Building Land – Novel Adventures in a Cyber Physical Environment†presented by Steffen Wendzel and Sebastian Szlosarczyk. The talk started with some definitions and concepts. What is a smart building? It integrates a BAS (“Building Automation Systemâ€) for the control, monitoring and management of facilities (most common are HVAC).
And what’s the status today in this specific field? It’s a huge business which will keep growing with the integration into the “Internet of Thingsâ€. What are the goals of BAS?
- Energy saver
- Reduce operating costs
- Reduce costs of churn
- Enhances security and safety
- Fast and effective services
- Environment friendly
Of course, this is deployed to enhance the security of buildings but with a clear lack of proper security. The speakers gave some examples of disclosure in the press. Wlll we gonna die? What’s the reality today?  There is no “smart buildingâ€! We can find different types of BAS implementations:
- Smart homes have private owners and a limited features (no elevators).
- Commercial buildings are owned by janitors with limited skills. They are operated by 3rd party (contractors).
- Large compexs with professional operators, constant monitoring and immediate response to problems.
The important question is : how many systems are available on the internet? Nobody knows exactly. They suggested 15K found (mostly US) and 9% were linked to known vulnerabilities. And what about the security? Some facts:
- First issues arose in the 90’s
- Internet of Things will make things worse
- TCP/IP helps to attack (ex: spoofing)
- Vendors!!
- Lack of awareness
- Legacy software & hardware
- No patching
- Insecure management (remote access / web GUI)
An interesting point of view: Some data leakage from BAS can be a valuable source of data (when the building is used, open, closed, …). BAS can also be part of botnets!
Example 1 – mass surveillance via remote access to sensor data. “Who’s going to the bathroom every night and is probably sick?â€
Example 2 – Oil/gas producer. Slightly increase heating levels … to sell more oil / gas.
The first part of the presentation was a review of the landscape. The second one focused on network protocols. Various exists: Closed / open protocols, EIB/KNX, TCP/IP. BACnet (“Building Automation Control networkâ€) is defined by ISO 16-484-5 and is used word wide by 730 vendors! Compared to TCP/IP, BACnet has only four layers: Physical, data link,  network and application.The speakers reviewed the basic of the protocol which has vulnerabilities… of course! What are the security flaws? Authentication and encryption means are specified by the standard but they are rarely implemented.. Large attack surface: Smurf-like attack, traffic redirection, DoS re-routing, malformed messages, inconsistent retransmissions. Several attack example were reviewed. How to solve this? By implementing traffic normalisation. It eliminates ambiguities and prevent devices of proposed attacks, limits address spoofing, has the ability to secure legacy systems which are not upgradable. and can be integrated in any protocol. How to do this? Using Snort with an extension for its own BACnet stack. By collecting samples and logging, it’s also possible to perform anomaly detection. Example with a heating system: During winter, it must be turned on and off during the summer. A temperature of 35°C during the summer is suspicious.
The talk conclusion was that many attacks are available: network attacks as well as  devices attacks (at physical or software levels). Sad that the last slide was more a product placement (IMHO).
The slides are available here.
The next presentation was about scanners: “Scalable Network Recon: Why Port Scans are for Pussies†presented by Fred Raynal and Adrien Guinet. Why scanning is important? Port scanning is not always performed by bad purposes. In researches, we may need some powerful scanner to scan “the whole Internetâ€.
Nmap is probably the most known port scanner but not the best choice when you need to scan a huge number of IP addresses. What are the speakers’ motivations to build their own solution?
- For attackers, information is as valuable as a 0-day.
- For defenders, to learn about themselves. To learn about their own attack surface and guide them to the most exposed and sensitive data.
The first part focused on how to design an Internet wide scanner. There are plenty of tools that can be used (nmap, zmap, masscan) but also at upper layers (snmpwalk, sslscanner, nikto) or OS fingerprinting (nmap, p0f, sinFP). The goal is how to get the right information as quickly as possible? For Fred & Adrien, the main problems were:
- Distribution
- Scalability
- No searchable web interface
- A SYN engine efficient as mass can
- Scripting easy as nmap
- And running as a daemon to stream targets as they come.
They wrote some building block to design their solution: libleeloo and nodescan. Both have Python interface and can be controlled from your own scripts! Amazing! Even complex actions can be scheduled (based on results. Want an example? Add a zone transfer probe to a detected name server. The next challenge was to acquire targets. How? Via GeoIP? BGP AS? They gave a practical example: how to convert a domain like *.gouv.fr into IP addresses?
Finally, once you have a powerful scanner, what are the usage? What can we find on Internet?
- Vulnerably research (ex: 443 & Heartbleed), Â looking for backdoors (some SOHO routers)
- Scan a country  (ex: Spain, 30M IPs, 100 probes, 30 ports) then you can go deeper, search for cams, for specific web servers. For the fun parts, they reviewed some findings in Spain
- Diffing networks (how they evolve in time).
- Usage monitoring
Fred and Adrien’s conclusions were that port scanning is not only sending dump packets. Grabbing info is one thing but their analysis need more resources (that’s why scalability in the key). People are complaining about port scans in 2014? They are more critical issues. You’re late. During a Q&A session, two topics came on the table: Is it legal or not? (IMHO it depends on Countries) and what about scanning IPv6 networks. This one a very interesting talk!
The slides are available here.
After the lunch break, we spoke about spy agencies with Stephen Kho and Rob Kuiters. The title of their presentation was “On Her Majesty’s Secret Service: GRX and a Spy Agencyâ€. The introduction was “why this talk?†Last year, Belgacom (the national Belgian operator) disclosed they were hack and probably by an intelligence service. Why do they hack the carrier? What are the interests? In mobile networks, one key is to know where are the devices. The problem with telecom operators is that they use a lot of abbreviations like CI, RAC, MCC, MNC, APN, IMSI, UICC, etc. Stop! Rob explained how a phone connects to a network and which kind of information are valuable for an attacker:
- APN (some are private and could be more valuable)
- IMSI
- End User Address
- User Location Information
- IMEI
When you travel to another country, you use GPRS Roaming eXchange (GRX). It’s a global network which ties all operators together. They are many GRX providers worldwide and, surprise, BICS (Belgacom) was one of them. By default the GRX traffic cannot be analysed out-of-the-box by Wireshark or any packet capture tool. So, the first step was to remove the GTP headers. With the help of another guy who write the gtpstrip.c tool, they were able to read the packets details like any normal capture. Based on this, it’s possible to know who you are (mobile IMEI), your location (provider, cell) and what you did (who, where, what).
The next question is: how to have access to this information? The speakers explained how they applied the first steps of a pentest project (without really exploiting the target). The GRX BGP routing table has 4.8K subnets (320K IP’s). They did a port scan with limited ports and GTP ping using masscan. The results was impressive: 42K live hosts. What about the GTP ports? (UDP/2152 & UDP/2123). For this, they used zmap and OpenGGSN. The next step was to extract the DNS version used: most BIND and some Microsoft. Bind versions had vulnerabilities. Other services: Cisco PIX, Exim, Microsoft ESMTP, Postfix, Sendmail, qmail. Some of them were outdate and vulnerable too. Lot of FTP servers, HTTP servers and telnet daemon (some running on Windows XP!) Looks like some operators mixed their GRX and office networks. SNMP with default communities (public / private) Out of the 42K GRX hosts, 5.5K hosts from 15 operators were reachable from the Internet!
Conclusions: GRX is really valuable, not closed off from other network as expected. 15 operators distribute BGP routes prefixes to both GRX and Internet. 5.5K hosts are reachable via Internet. Operators must be more security aware!
The slides are available here.
Do you know Passbook (the IOS app) and do you use it? This talk was interesting: “Exploiting Passbook to Fly for Free†by Anthony Hariton. Last year, there was already a talk about security in airports. This year, the target is the electronic boarding pass handed by the Passbook application. What is Passbook? It keep tickets all in one place (movies, flights) in your iDevices. Flights? That’s iinteresting. Anthony’s research was to try to forge a valid Passbook boarding pass.
What you’ll need? an iPhone, a decent web browser, a photo editor and a pair of balls! 🙂
- Step 1 – find a picture of a boarding pass
- Step 2 – Use a WYSIWIG online service (example: passkit.com)
- Step 3 – Have fun (at your own risk!)
Anthony explained how to create a rogue boarding pass. Not very complicated.Then I explained what can be done at the airport. Normally, with your rogue ticket, your should be able to go up to the gate (in the security area). But, you’ll be rejected because your name is not on the passengers list. Is it a problem? Well, go back to the company desk and ask to the ladies to fix your ticket “because there was a problemâ€. Using social engineering, you have chances to force them to add your name to the passengers list. Win! An entertaining talk perfect for a second day afternoon.
The slides are available here.
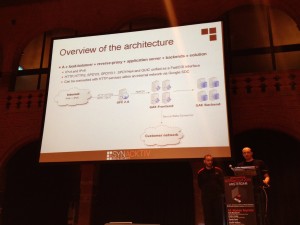
The last talk was “G-Jacking AppEngine-based Applications†by Nicolas Collignon and Samir Megueddem, two pentesters who played with the “Google Apps Engine” service (GAE). What is GAE? It’s a PaaS (“Platform as a Service“) for web applications. A SDK is provided to build web apps into the Google datacenters. They support common modern languages and the architecture is based on the following components: load-balancers – reverse-proxy – application-servers – backend-solutions.
What king of vulnerabilities can be found in a GAE environment? Developers still:
- manipulate raw SQL queries (SQLi)
- control raw HTTP responses (XSS)
- need to implement security features or use correctly use frameworks (CSRL are still possible)
Google provides interesting API’s like urlfetch. It is used to request external web services and many features but some are not enabled by default like SSL certificates verification. Is it possible to get Python remote code execution? The speakers explained how to get persistent shell. How? By installing or injecting a XMPP end-point and register an URL route. Then a regular XMPP client (like Gtalk) can be used to interact. A GSOD (“Google Screen Of Death”) is possible by calling most API’swhich are billed on a share-basis (CPU, memory, etc). Google may respond with an “over quota” error message. To protect against this, IP blacklists are supported but GAE is available over IPv6 which remains difficult to block.
How to build a “Google” at home in a lab to test GAE? All developement cannot be done off-line for multiple technical reasons and some tests must be performed from an application deployed in Google datacenters (ex: urlfetch or quota handling). Then, other use cases were reviewed like getting access to the source code.Isolation between versions is possible but often not implemented. Most apps trust data stored in the memcache back-end. Another one, the provisioning API. It is used by big organizations to automate users management tasks. This API requires a secret domain key. But often, this key is stored in unsafe places. Developers should not have access to this key. Then, the speakers explained how to evade the Python sandbox.
Conclusions: Google performed a good job at protecting his environment, it was not possible to fully escape the sandbox. But one of the threats remains developers who need to code securely (hosting your bad code at Google will not make it safer “as is”).
The slides are available here.
And to close the event, the last keynote speaker was Jaya Baloo with “A Clear and Present Danger, Security vs Net Neutrality: Tales from a Telcoâ€. The keynote focused on the point of view from a telco (Jaya is working at KPN) perspective about all the danger we are facing today like DPI, traffic shaping and their implication with security. How is it to be a telco today in Holland? Operators have obligations and rights but they must comply with local legal frameworks. A first interesting comment from Jaya:
“Pedophiles and terrorist suxx but should not be accepted as the basis to expand surveillance powers by he states“
It’s not allowed to inspect traffic to apply traffic shapping (ex: Pirate Bay). If technical solutions exist to protect users, operators are not allowed to implement them. A good example is attacks which send malicious SMS messages. Operators are not allowed to read the content of SMS sent to their customers to drop them. Botnets are another example. Operators cannot bring down botnets by themselve. Only upon a complain or request, compromized hosts can be shut down. Worse, if they know that somebody is infected, they can’t help them. What about lawful interception VS. mass surveillance. The first case can only happen upon a valid court request. Mass surveillance is bad and telco must stay outside of this said Jaya. She also mentioned the crazy “Hack back” project in NL where the authorities could be hack hackers using the same techniques.The EU Cyber Security strategy is a good point but software and hardware vendors are currently excluded from the scope of this directive. You said “lobby“? Threat intelligence sharing (IOC’s) is a key across the telco sector.
We already reached the end of the conference. Thank you to the organizers for providing me a press pass again. The move to the new location was a good choice (IMHO) and the mix with haxpo.nl interesting. See you next year! I’m off to Belgium now…








RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #2 http://t.co/h3FRSnrc5e #HITB2014Ams