 I’m in Amsterdam for the next two days to attend the new edition of Hack In The Box. This is a special edition with many improvements. First, it’s the fifth edition (already!) and the location changed to “De Beurs van Berlageâ€, a very nice place in the center of the city. Second, the normal conference is also held alongside with HITB Haxpo, a technology and security expo for hackers and geeks. This expo is open to everyone for free. Due to a holiday in Belgium and Holland, I joined Amsterdam smoothly without any traffic jam and was in time to grab my badge, some coffee and some 802.11x packets before the talks.
I’m in Amsterdam for the next two days to attend the new edition of Hack In The Box. This is a special edition with many improvements. First, it’s the fifth edition (already!) and the location changed to “De Beurs van Berlageâ€, a very nice place in the center of the city. Second, the normal conference is also held alongside with HITB Haxpo, a technology and security expo for hackers and geeks. This expo is open to everyone for free. Due to a holiday in Belgium and Holland, I joined Amsterdam smoothly without any traffic jam and was in time to grab my badge, some coffee and some 802.11x packets before the talks.
The day started with two keynotes. This edition is dedicated to women! Only women are doing keynotes. The first one by Katie Moussouris about “Security at the End of the Universeâ€. Katie’s daily job is to try to protect as many people as possible. She is the initiator of the Microsoft bug-bounty program. Today, we are carrying all day long millions of data in our packets thanks to our smartphones. On those, apps are running. More and more apps… A fact is that there is a huge gap between developers and security researchers. The first ones have dead line to respect to deliver the code. And security researchers also do they job by breaking the apps. We have to accept that flows will be present in code forever. Katie’s idea was to make researchers work closer to developers and it’s not easy.
Today most vendors are still working in reactive mode: a found vulnerability is patched. A best approach is to work in proactive mode. But to make vulnerabilities in software understandable by all parties (vendors – developers – researchers – users), it’s is mandatory to speak the same language. That’s were standardisation can help us. Some ISO standards are available to better handle vulnerabilities. That’s important because more and more technologies are interconnected (insulin pumps, pacemakers, eBanking websites, etc). In the future, everything will be smaller, smarter and interconnected. Another approach describe by Katie is fuzzing the global chain of influence. This most occur at all layers of the eco-system also lawmakers and deciders. A global awareness approach is mandatory and already growing: How many of you have been asked by non-tech family members about the Heartbleed attack? Other advices provided by Katie: Do not copy lines from a book without understanding them. If you build software, learn also how to break them. If you’re a defender, break also (your) networks. Vendors must have an proactive approach of security and not only reactive. Katie did her keynote without slides but here are the link to the interesting ISO standards: ISO/IEC 29147:2014 (vulnerability disclosure) and ISO/IEC 30111:2013 (vulnerability handling process).
The second keynote was the one of Kristin Lovejoy from IBM Security Services about “Building a Strategic Defense Against the Global Threat Landscapeâ€. Kristin started her keynote with the definition of “ironyâ€. She explained that she became unpopular amongst her colleagues when she decided to prohibit the use of USB ports. But later on, her computer was infected when she exchanged a USB stick… Nice example to demonstrate that everybody can fail or will fail in a time.
She had the opportunity to learn information security and did several job before working for IBM. That’s a first lesson: to better protect your stuff, you must learn and understand how they work. An interesting opinion from Kristin: why are women better CSO (“Chief Security Officerâ€) then men? Because women can talk to babies and explain things with simple words. How’s the information security landscape? Mobility has changed the business forever and the security world is shaped by a few key dynamics:
- The globalisation
- Internet enabled mobiles / apps
- The Internet of things
- Analytics
- Cloud computing
In many companies, the CSO’s best friend today is… the CMO (“Chief Marketing Officerâ€) because he owns the biggest IT budget! Take the example of mobile apps. Every business has specific apps. But how are they developed? Internally or outsourced to a student who has a zero-knowledge of security? Other Kristin’s lesson: “Like any biological system, we are all infectedâ€. Anything that is connected to the Internet can be hacked but everything is connected to the Internet today. Guess what? Another fact, based on IBM statistics, 95% of incidents has a human contributing factor like:
- Failure to delete dormant user accounts
- Poor system hygiene
- Malwares
- Stolen devices
Today, insiders remain the cause of many attacks and guess who they’re? Privileged users in most case. Then others lessons were explained by Kristin:
Lesson 3: “The bad guys rely on our stupidity, ignorance and dump mistakesâ€. Most security incident can be easily avoided by using simple controls.
Lesson 4: “Getting ahead of the threat requires you to know how to disrupt the attack chainâ€. Not every person have the same level. People have different profiles. People can be classified like data. Apply profiles to them. A good quote: “When you implement good security controls, you won’t see the number of incidents going down but growing up!
Lesson 5 : “Know how to communicate with executivesâ€. She made a comparison between information security and a house. To build a house, some common steps are required. Then, you will make your own customisation. The same can apply in information security Build a risk aware culture and management system.
Slides are available here.
After a first coffee break, the first regular talk was “AIS Exposed: New Vulnerabilities and Attacks† by Dr. Marco Balduzzi and Alessandro Pasta. AIS (“Automatic Identification Systemâ€) is a protocol used between ships and from/to port authorities to provide the following applications:
- Maritime security (privacy)
- Collision avoidance
- Search & rescue
- Accident investigation
- Data (ex: weather forecasts)
Since 2002, AIS devices are installed on most ships (it is mandatory). You can compare it like a flight transponder. AIS messages are exchanged via VHF or online providers (read: “the Internetâ€). Those providers collect and visualise information via mobile applicationss, emails, API’s or RF gateways. This brings nice apps and websites online:
Thus, if devices are implemented to exchange “messages†for sure, there are many threats. That was the purpose of Marco & Alessandro’s research. Basically, they are two types of threats:
- Implementation specific – related to online providers
- Protocol specific – AIS transponders
They wrote some Python code to generate AIS messages with specific payloads. The hardware used to set up the lab is freely accessible for sale on Internet.
The first attack scenario was to fake ship information (spoofing). Imagine a US ship close to the North Korea? Fake ship route or hijacking (rogue gateway) can also be performed. What about moving a ship from the Mississipi river to a lake close to Dallas? Done! What is the main issue of AIS? It was developed when hardware hacking was not easy (10y ago – not so long but very old in IT). It suffers of a lack of integrity and authentication. But today, tools are accessible to anybody and such protocols are easier to attack. Let’s do it via software!  (SDR – Software Designed Radio). The first demo was to display a fake boat called “Trend Microâ€. Then, to generate a fake “man-in-the-water†distress beacon! Rescue jackets have devices to send this type of alarm. Lure a victim vessel into navigating to a hostile and attacker controller space. Nearby Ships must change their route! Mandaroty by legislation. The next attack was a DoS (Frequency hopping). Example: pirates can render a ship invisible upon entering Somalia. How: disable AIS transponders, switch to non-default frequency. Another one? Fake a CPA alert (Closer Point of Approach) or spool malicious weather forecasts! But if the protocol is able to exchange messages containing a payload, why not going back to the roots? The messages are exchanged and processed at application layer. Messages are stored in databases. Hmmm… They is a huge potential here for buffer overflows, SQLi, code execution, etc. As example, generating a message with a single quote generated a nice SQL error in an application. The last attack example was against D-GPS (“Differential GPSâ€). D-GPS helps to have a more precise position (meters -> centimetres). The attack is based on spoofing D-GPS beacons to force the ship into computing a wrong GPS position! After the research, the speakers contacted the appropriate providers and authorities to report the findings (in the scope of a responsible disclosure). What could be the available countermeasures? Nothing new: to add authentication, to implement a time check (to avoid replay attacks) and to add integrity and validity check on data (ex: position). A very nice talk with a good balance between theory and demos!
Slides are available here.
My next choice was the talk: “XSSing Your Way to Shell†by Hans-Michael Varbaek. I arrived late in a crowded room and found a seat in the hook. Not the best place to attend the talk but it looked very interesting. Today XSS attacks are still very common. In most cases, they are use to hijack users or admins sessions but they could also be used to… get a shell! Hans-Michael explained (with lot of demos) how to achieve this. The demos looked really impressive. A reviewed some common CMS like WordPress and how exploit were written for them.
The slides are available here.
After the lunch break, I followed Michael Ossmann’s talk about “The NSA Playsetâ€. Michael is the founder of greatscottgadgets.com (open source hardware solutions). Everybody remember the NSA catalog pages. Michael had the crazy idea to review the described gadgets and to investigate how to build them “in the real lifeâ€.
Why? Because it’s fun! Who never dreamed to act as James Bond and have all those toys available? Today, there are plenty of low-cost hardware solutions like Arduino or Ubertooth that, coupled with open source software, can propose the feature of the NSA gadgets. This is not science-fiction! Michael reviewed some NSA toys and explained how to build their matching peace with open source components and software. See the website nsaplayset.org for examples.
The slides are available here.
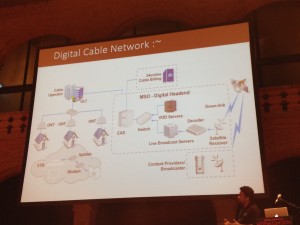
Then, “Hacking Your Cable TV Network: Die Hard Style†by Rahul Sasi. TV remains a major media, televisions are in every houses and people trust what is broadcasted on TV. Rahul started his presentation with a sample video of Die Hard 4 when the hackers broadcast their message across all the channels. Could you imagine the impact on people if this happens in real life? That’s the purpose of Rahul’s research: how to break cable TV networks. Some providers remain on analog infrastructure but most are switching to digital TV. For digital TV, it’s quite easy. After a brief review of how TV signals are processed, Rahul explained that the most efficient attack is the classic MitM. Via a physical connection (direct link), it is easy to replaced one channel by another one using the same frequency.
First, analog tv broadcasting. Rahul started with some explanation how analog TV signals are processed. To attack this type of network , MITM is the most easy (there is no encryption). Via physical access (direct link connection). Note that optic fiber is difficult to tap. Focus is to local orator which use coax cables. Attach: broadcast using a used frequency. And what about Digital TV? The big difference is that signals are encrypted. DVBC is an access control mechanism, used over TCP/IP or DVB-C and customers need a Set-Top box to receive (decrypt) the channels. Where to attack such networks? The management network or the end-user Set-Top Box. The billing server can be attacked.Where are they located? Network fingerprinting – some are facing the wild Internet. Like SCADA they are not supposed to be there. First bug: a PHP bug (array) permuted to hijack all STB from an operator. Or shutting down some channels… Then Rahul demonstrated how the Set-Top box could be abused by exploiting vulnerabilities in the MPEG flow. The topic looked interesting but the focus was given on India TV providers. I’m not sure that the same could apply in Europe. Just one last remark to Rahul: your videos were almost unviewable! (too dark)
The slides are available here.
The afternoon coffee break was followed by “Exploiting NoSQL Like Never Before†by Francis Alexander. The presentation started classically with a presentation of NoSQL features: schema less, no relational model, ACID (“Atomicity, Consistency, Isolation and Durabilityâ€). There are different implementations of NoSQL: MongoDB, CouchDB, Redis. What about the default security they implement?
And why developers need to worry? Basically:
- Low on security
- Emphasises on trusted environment
- Weak authentication
- MitM possible
- API’s exposed (API for PHP is buggy!)
Then, Enno Rey, Felix Wilhelm & Matthias Luft came to speak about “Compromise-as-a-Service: Our pleasureâ€. After playing with VMware, today the speakers presented their research about the Microsoft Hyper-V. Why? Because it’s not a common target and it is used in many corporate environments like Azure and… it’s marketed by Microsoft 😉
Which methodology was used? For an hypervisor, the most critical is feature is the isolation of the different systems. An hypervisors comes with the same basic features: devices management, CPU virtualization, memory & isolation and API’s. A very interesting quote from the presentation:
“Any hypervisor is not a new security layer, it’s a new place to find bugsâ€.
The researchers started by searching for useful documentation?
- Hypervisor top-level functional specifications
- Linux integration services
- Patent applications
- Singularity header files
- Common criteria certification documents
- Binaries!
Binaries did not have debugging info available. Some are provided by Microsoft but not for those binaries. Idea: use the one of other binaries which share some code. They explained how to find an interesting surface attack. Then, they went deeper and deeper to explain how they found interesting vulnerabilities. The research results in the security bulletin MS13-092: DoS of complete hypervisor, potentially priv escalation to other virtual machines and Azure was affected. A live demo was performed to crash an Hyper-V. Conclusions: It’s a question of time to find bugs. And it’s not hard. This is just a software with a huge attack surface. On the other side, it’s hard but you’ll learn a lot.
The slides are available here.
The day was closed with another keynote by Mischel Kwon: “Cyber Security: Creation or Evolutionâ€. Mischel reviewed the story of IT and more precisely information security starting from the eighties. I felt old just be remember the good old times she mentioned.
For each period, she reviewed:
- technologiy and society aspect
- Attacks available at this time
- Mechanism to detect / remiediate and prevent
- Government, laws, policies in place
From 1980 to 1985, we had the  mainframes, minis & micros. “Wargames†was a nice movie and attackers were phreakers or phrackers… Do you remember the blue box? From a legal point of view, it was a “security rainbowâ€.
From 1986 to 1990, it was the PC’s era and dialup access… Attacks were some kind of “Know knock let me in…” and  MVS/PAS “Problem Alert System” was deployed. It was the era of computer security acts.
From 1991 to 1995, the public discovered and connected to the Internet. We deploted firewall, IDS, honeypots. From a legal point of view, we moved to information security.
From 1996 – 2000, we saw the e-Commerce emerging, Windows 98 and online updates, polymorphic viruses, websites defacements, “shit I can’t keep up†, too many problem – Information assurance – “it’s all about the data“.
From 2001 to 2005, it was the  mobile explosio and the Chinese were here! Logs, packets, flows were collected and analyzed. Now we call it “cyber securityâ€.
From 2006 to 2010, we faced the mobile era with iPads and many other gadgets, we started to live on those systems and sa complex attacks for different purposes (conficker)
From 2011 to today, our life was brought online. Attacks are  “You wanna be pervasive†(from an attacker perspective) – hacking interesting things. Complexity , insiders (my boss, the admin)
What are the future attacks? According to Mischel, they will be more personal, more violent, attack our reputation or career. And laws? computer or internet specific laws? We created it, we interconnected everything, and we have to take care of us.
The slides are available here.
The first day finished with the Google party (thanks for the free drinks) and a cool dinner with friends. Stay tuned for the second wrap-up tomorrow!








RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
@xme Don’t forget to get a #HITB2014AMS / #Haxpo #projectS Badge 🙂
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams
RT @xme: [/dev/random] HITB Amsterdam 2014 Wrap-up Day #1 http://t.co/qarc330hev #HITB2014Ams