 “Heartbleed“… Probably one of the top queries typed in search engines for a few weeks! Of course, I followed the story but I did not blog (yet) about it until today. Why repeat again and again what has been said? Some bloggers and analysts wrote very good overviews about this modern nightmare.
“Heartbleed“… Probably one of the top queries typed in search engines for a few weeks! Of course, I followed the story but I did not blog (yet) about it until today. Why repeat again and again what has been said? Some bloggers and analysts wrote very good overviews about this modern nightmare.
The bug was even covered as a breaking news by medias. Some of them, as usual, reported so stupid stuff! No, heartbleed is not a virus! Blaming medias is easy but the lack of knowledge hit also pure IT people. I found this quote particularly scarying:
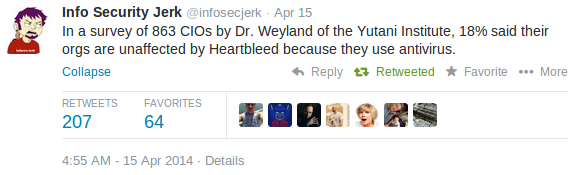
I did not expect CIOs to be able to describe the bug itself, it’s not their job. But in 2014, thinking that an antivirus solution protects you against anything is a fail! OpenSSL being used as a key library in so many products and solutions (free as commercial), almost everybody was unprotected. I was too! Patch, change password, revoke and create new certificates, the procedure is known for a while and IT department had hard days to patcth everything. A few weeks after the release of an OpenSSL patch (it was released on the 7th of April), it was time to ask myself if the bug is still alive at least in Belgium. This weekend, I searched for vulnerable systems across the Belgium IP space. I focused on HTTPS but keep in mind that the bug may affect much more services! Here are the results:
- 7.704.578 IP addresses tested
- 70.408 HTTPS services open to the wild
- 2.502 IP addresses reported as vulnerable
Those are only IPv4 addresses but many systems being dual-stacked, scanning IPv6 ranges won’t make a big difference in this case IMHO. I won’t disclose the list of vulnerable hosts here. The nmap NSE script was used and no real data gathering was performed of course! Some statistics looks interesting:
- Many infected services are running being residential connections
- Some ISP’s or hosting companies are still vulnerable (they should be in front line to patch right?)
- Lot of webmails are impacted
- Remote access services (SSL-VPN) are also present in the list
My feeling is strange… The Heartbleed bug is a huge one which may have big impacts however residential users and small companies can’t be blamed for remaining unprotected, security is not their core business. But is it a valid reason to not take corrective actions and leave them as is? Biggest Belgian ISP have many customers infected. They could maybe use their helpdesk force and do some outgoing calls campaigns? For all the others, check if you are still vulnerable and… patch again and again! If you have some doubts, ask your service provider or IT consultant!
Dr. Weyland? Charles Bishop Weyland??? He is not just “of”, he is a co-founder of the Yutani Corporation, which surely has more than one Institute! They’re famous since 1979… Which geek hasn’t heard of the Weyland-Yutani Corporation? (https://en.wikipedia.org/wiki/Alien_%28franchise%29)
The statement is not sourced, the nickname Info Security Jerk is not very reassuring, either… I’m not saying it’s fake, but without additional information it sure looks like it! 🙂
I mean 82%…
Cool quote. Maybe the other 72% think they’re safe thanks to their firewall 🙂
RT @xme: [/dev/random] Heartbleed Impact in Belgium? http://t.co/tq38ar4ddT
RT @xme: [/dev/random] Heartbleed Impact in Belgium? http://t.co/tq38ar4ddT
RT @xme: [/dev/random] Heartbleed Impact in Belgium? http://t.co/tq38ar4ddT