 A few days ago, I wrote a blog post about a Python script that I use with the new Amazon CloudTrail feature to grab logs from my Amazon cloud services. Because we use more and more cloud services in our digital life, the same principle should apply to all our online services. Recently, GitHub suffered of a brute force attack against accounts with weak passwords. This story was covered by a nice blog post. They took actions like blacklisting well-known weak passwords (By the way, they also offer 2-factors authentication). Why attacking GitHub accounts? Because user’s repositories contain very interesting information. Source code could be modified to add malicious code like a backdoor to existing code or some private data could be stolen (certificates, credentials, SSH keys, etc).
A few days ago, I wrote a blog post about a Python script that I use with the new Amazon CloudTrail feature to grab logs from my Amazon cloud services. Because we use more and more cloud services in our digital life, the same principle should apply to all our online services. Recently, GitHub suffered of a brute force attack against accounts with weak passwords. This story was covered by a nice blog post. They took actions like blacklisting well-known weak passwords (By the way, they also offer 2-factors authentication). Why attacking GitHub accounts? Because user’s repositories contain very interesting information. Source code could be modified to add malicious code like a backdoor to existing code or some private data could be stolen (certificates, credentials, SSH keys, etc).
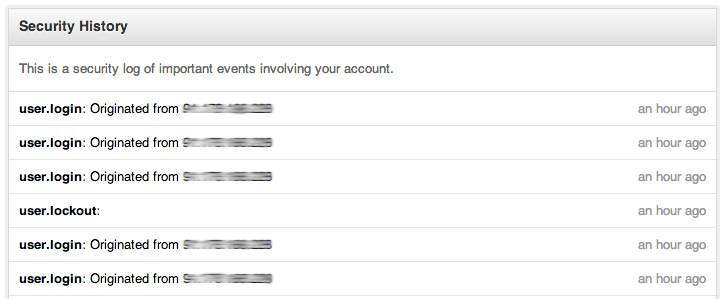
A very good point for GitHub, they have a “Security History†page which contains a lot of interesting information. The information is available on the following URL: https://www.github.com/settings/security.
Each event contains the following data:
- Event Name
- Actor
- Source IP address
- Timestamp
- Repository
- User
$ ./getgithublog.py -h
Usage: getgithublog.py [options]
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-u GITHUBUSER, --user=GITHUBUSER
github.com user name
-p GITHUBPASS, --password=GITHUBPASS
github.com password
-s STATUSFILE, --statusfile=STATUSFILE
status file for event history
-S SYSLOGSERVER, --syslog=SYSLOGSERVER
send Syslog messages to specified server
-d, --debug increase verbosity
$ ./getgithublog.py -u 'xxx' -p 'xxx' -d -s .github.status -S localhost
+++ Debug mode
+++ Sending Syslog events to localhost
+++ Using status file: .github.status
+++ Connecting to github.com
+++ Authentication successful, collecing security logs
+++ Last event epoch: 1385450685
$ grep github /var/log/syslog
Nov 27 09:37:46 h0neyp0t ./getgithublog.py[12710]: "event":"user.login","actor":"xxx","actor_ip":"x.x.x.x","created_at":"2013-11-27 00:35:47","note":"From GitHub.com","user":"xxx"
- I tried to extract the events based on safe elements in the returned HTML code. However, the script may become broken if GitHub decides to change the layout of the page.
- The scripts requires credentials. Use it carefully, take care of cron jobs or shell scripts
- The script starts a regular session with your account. This means that every time you execute the script, you create a new “user.login†event.
- Don’t run the script too often, GitHub has a protection against multiple repetitive logins and will lock you during a few minutes.
- Timestamps are returned based on the Pacific Time (UTC-8).
Happy logging! The script is available here.
RT @xme: [/dev/random] Tracking your Github Security Events http://t.co/jJdz5Savek
RT @xme: [/dev/random] Tracking your Github Security Events http://t.co/jJdz5Savek