
Hello Everyone, it’s BlackHat time again! Here is my wrap-up for the first day. Yesterday evening, after a safe drive to Amsterdam with @corelanc0d3r, we went out for dinner and had good times with other friends and guys from the Rapid7 team who maintain the Cuckoo project. The conference is organized at the same location as the last edition, the Grand Hotel Krasnapolsky, a very nice place in the centre of the city. After a standard dose (but necessary) of caffeine, Jeff Moss performed a brief introduction of the conference. For this edition, 500 people registered to attend the conference. Jeff insisted on the feedback that attendees can provide to build better events in the future and choose the right directions to meet most of our expectation. New events will be organised like local (geographically) events and events dedicated to trainings only. What are the current trends? Mobile and embedded devices remain on top of the talks. Another classic, some minutes were also allowed to the main sponsor for  some “marketing” messages.
As usual, the conference started with a keynote. This year, the speaker was Rick Falkvinge, the founder of the first Pirate Party which is now represented in 60+ countries. Rick started with a clear message: “I’m a politician“. He moved from jeans/t-shirts to ties. The title of his presentation was “Shelters or windmills: the struggle for power and information advantage” or how governments behave with information across years and how the history repeat itself.
Since the written language, Internet became the most important media. Monks copied books during years. This process took lot of time and was very expensive but they kept control of information. First fact reported by Rick:  “If you can dictate true from false, you wield the most power at all“. This is the information advantage. Then, the printing press was another big step. It allowed to distribute cheaply, quickly and accurately to the masses. More and more people started to “publish“. As an example, the Bible was published in multiple languages. This give the power of interpretation but let to punishment for duplication. Does this story sound familiar? “All of this happened before, all of this will happen again” (famous quote fro Battlestar Galactica). If you control the truth, you control your adversaries. and prevent your replacement. In all times, new things scared people. And some industries used the fear to protect their business. As an example: the automobile was called “horseless carriage” and needed a team of three people to be operated: a driver, a stoker and red flag weaver walking in front of the car. Keep in mind: Once a technology shift is on the way, it must occur quickly or big industries will fear and try to block. What about the right to make money? If you invest, you take a risk and hope to get a good return on investment. The example of ice makers is good. Those companies stored huge amounts of ice to be sold to people. But when fridges appeared, this industry disappeared quickly (loss of income). Technology has always changed the business models… and always will. In 1849: the British parliament authorised the first public library to open. Editors complained that to read a book you’ve to pay first and that nobody will continue to write books. Guess what? Did it happen? Authors continued to write books. Copyright industry always complained that “the sky is falling” and have multiple enemies: it started with self-playing pianos, gramophones then television, tapes, video recorders and, today, Internet, Cloud applications, MP3. Today’s ISP’s and telecom operators are a nice target for the copyright industry. Government keep the pressure on them to implement tracking solutions (tapping). But, wait, what about the regular letters? They are never read, tracker and mailman is never responsible for the content of the delivered messages. They are a great way to distribute drugs by the way. Why such differences with the modern media? We have to fight to give to your children the same rights to communicate as we had with letters. Where are we today? Governments strike back with seizing corporate data, attacking  the messenger immunity. Rick referred to mobile phones as “government tracking devices that can also by used to call people“. Think about the story of Skype: France would like to see Skype as a telco to be able to tap communications. A good conclusion to the keynote was this quote:
“Curiosity is not a crime. Locking up knowledge and culture however is.”
The Rick’s message to all the people present in the room: We hold the information advantage and we know how to use tools to avoid them to block us! This was an awesome keynote with good messages to keep in mind. Note that if I agree with most of the ideas presented by Rick, this blog remains a-political.
After a small coffee break, I spent the first part of the day with Nikhil Mittal who prepared a workshop about PowerShell for Penetration Testers. How this standard Microsoft tool can be used during your pen test projects.
Nikhil started with the basics: Windows PowerShell is a task-based command-line shell and scripting language. It is present on the most general targets so easy for post exploitation and provides powerful method to reside in systems and networks. Why use PowerShell? It provides access to everything in a Windows platform, easy to learn, well documented and trusted by most administrators. If you are new to PowerShell, the first step is to use its integrated help-system:
Get-Help <cmdlet name|topic name> Get-Help About_<topic>
You can compare this help to the UNIX manpages. PowerShell ISE has also a GUI, editor environment with nice features. Cmdlets are task based commands and many of them are interesting for pentesters like get processes. What can we achieved from PowerShell? Browse the registry, list users, browser Internet Explorer history. PowerShell and Metasploit? How to use both of them? msfencode supports PowerShell to create payloads using the “-t psh” argument. It was very interesting but a little too long (three time slots).
After the lunch, I decided to switch back to the regular talks schedule and attended “Building a defensive network for medical device security” presented by Jay Radcliffe. He made the research about the insulin pump (Human SCADA system) presented during BlackHat 2011. The amount of researches about medical devices increased over the last years with a focus on embedded devices. But barriers remains: access to devices is difficult, costs are huge and access to devices is restricted by prescription. Ex: an insulin pomp costs between $5000 to $9000). Don’t forget the legal concerns! Hopefuly there is a pressure to change. The US Congress ordered investigations and security researchers are pushing hard for change (Shodan reports more and more medical devices directly connected to the Internet). How such devices are approved? By the US Government (United States Medical Device Approval) but the processes remains hard: PMA (“Pre-Market Approval“) or 510K (pre-marketing submission). FCC (“Federal Communications Commission“) has also an approval process for devices that have wireless communications. This is clearly not easy… And what about Europe? There are EU directives like 93/42/ECC which is the medical device directive but… contains no mention of security of communication. Check out the approval process. Who could read this:
There are classification problems:  Europe & US have specific categories for devices based on their function (ex: In vitro, diagnostic).  The first category is a peripheral attached to an “OS” (Windows, Linux, …). The scope is very wide. Common problems are the patching and hardening of the operating system. Also, the lifespan of the device is longer that the lifespan of the OS. Hopefully, there exists mechanism to patch and update (more and more eyes are looking for issues). The second category are independent medical devices. Embedded with no OS and proprietary code. The software is hardcoded, how do you upgrade? There are far less eyes looking at the problem. They also use DYI code (crypto & obfuscation)… read “weak”. Good thing: The code base is small and they can support the full lifespan. The third category uses wireless connectivity (802.11, BlueTooth or ICS/MICS). In this case the problems are a lack of updates (ex: WEP vs WPA2). They provide security through obscurity and don’t have physical barriers. Jay’s big fear? There is a pressure on regulatory agencies to address the issue but they don’t have experience (don’t know how to fixe it) and regulatory agencies should not legislate solution on technology. There is a lack of infrastructure and security experts to take the responsibility of this. There is a need of a framework for security in four steps:
- Focus on process and procedures associated with addressing security issues
- Clear up process and procedures for patches and updates, provide guidance on the use of AV on commercial OS platforms
- From a testing stand point, it would be useful to identify DLLs/LIBs that are used by a medical device and classify them in categories (provided by the vendor, 3rd party or not used). This could allow IT to better determine the risks of OS patches.
- Require 3rd party testing as part of the approval process. Full report must be submitted with remediations
What to conclude? Vendors of medical devices must start to use this framework now. Go though the business continuity process for vulnerability disclosure. If you will received such device in your body, you’ll be very happy to know that it has been pentested by a company you know has good reputation. It was a non technical presentation but worth interesting from my point of view.
The next talk was “Meshing Stuff Up: Ad-Hoc mesh networks with Android” by Josh Thomas (mOnk_dot) and Jeff Robble (stoker). They presented their SPAN (“Smart Phone Ad-Hoc Networking“). It’s an open source research project founded by the MITRE corporation. The goal is to use it during crisis communications. First of all, what is a mesh network? It’s based on one-to-one communications between devices. Â Why could it be so important? In 2005, the hurricane Katrina brought down three millions land lines down and 2000 cell towers. How to communicate in such situations? Same scenario during the earthquake in Haiti in 2010. There is multiple examples like those ones (Arab spring). But there is also a need to avoid tapping and manipulation like in Israel or the Anonymous. Idea: why not use our cell phones to build meshed networks? Pro: headless networks, dynamically grows and self-healing. Nodes can also act as gateway devices.
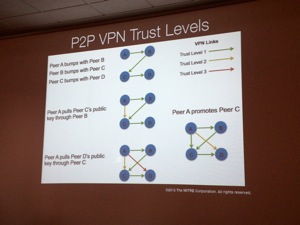
The SPAN project implements a framework to just make regular applications work via a transparent backend. This is implemented using a “stack” with multiple layers from the Linux kernel routing (bottom) to the App (top). What were the problems to solve? First the wireless chip (mostly Broadcom on mobile devices). Some devices do not support Ad-Hoc mode. In the kernel, there is a flag defined at compilation which disable some UDP packets to be sent when the screen is off (to keep a good battery life). This option must be of course disabled to allow a device to present all the time on the network. The next challenge was how to share SPAN? By default, you cannot share APK files via BlueTooth (it’s filtered out by extension). NFC does not allow file transfert. Enable the Master mode (AP) and share api files using a web browser. What about iOS? Jailbreak is required! SPAN can be distributed via alternative stores (Cydia). What about mesh routing? They are proactive or reactive protocols. Reactive protocols are OSLR, BATMAN, Babel. Reactive ones are for example DSR (Dynamic Source Routing). The next point addressed by the speakers: What about security in mesh networks? How to authenticate yourself? You can use certificated assigned by CA, use self-generated keys or common shared key. Trust level are important:
What about life situations? The max range for most Galaxy devices is 500 feet. The throughput was between 13.3 Mbits/s and 30.6 Mbits/s depending on the device model. What are the apps available? MANET Voice Chat (like walkie talkie). The future? Extend support to other platforms, improve the framework and routing. Â Another idea is to use the unused CPU cycles in mobile phones to distribute computing power across the mesh network. Again an interesting presentation which gave a good example when hacking devices and protocols can be a benefit for everybody. Also an interesting talk but I hoped to see at least a live demo of communication between two Android devices. Maybe the biggest question as a conclusion: Will you be ready to add your mobile device in a mesh network?
The fist day ended with my presentation about CuckooMXÂ at the BlackHat arsenal. I was very happily surprise to see more people than expected. The big advantage with the Arsenal: people who join have a real interest (well, I hope) in the tool you present. My project is still a proof of concept at the moment but I had great feedback. This is a good motivation to work again on it.
It’s done for today! Well, not yet! The day ended with the Rapid7 and IOActive parties. The breaking news was the official launch of Kali Linux by the Offensive Security team. From the different feedback I received, I missed some very interesting talks. You can also check the following friends’ blogs to read wrap-ups of sessions I did not attend: cupfighter.net and corelan.be.  Stay tuned for the 2nd day tomorrow…
Here are some extra pictures:








RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #1 http://t.co/8WCQTJUzh7
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #1 http://t.co/8WCQTJUzh7
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #1 http://t.co/8WCQTJUzh7
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #1 http://t.co/8WCQTJUzh7
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #1 http://t.co/8WCQTJUzh7
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #1 http://t.co/8WCQTJUzh7
@xme Xavier, could you post the pictures in HQ? 🙂
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #1 http://t.co/8WCQTJUzh7
@xme Thanks another time for taking time to write (so interesting) con wrap-up !!
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #1 http://t.co/8WCQTJUzh7