
And we are back with the second wrap-up of BlackHat Europe 2013! Â After a dinner with friends and some beers at Rapid7 and IOActive parties, I went back to the hotel to finish the first day wrap-up. I woke up, tool shower, grab some coffee and I’m ready for the second day! No workshop planned for today only talks. Here is a review of the one I attended.
My first choice was to attend the session “Honeypot that can bite: reverse penetration” presented by Alexey Sintsov. This talk is based on Alexey’s experiences with honeypots. He played a lot with honeypots and IDS systems. Their primary goal is to understand how attackers work and to take appropriate preventive actions. Based on the attempts, alerts can be created into IDS, etc. This is a known story, nothing new.

But, which kind of questions could we ask ourselves?  What the attacker tried, what is he looking for, how are we prepared? Based on the collected data, it could be interesting to search who are the attackers (R&D companies, governments, competitors, …). Some interesting questions that can be investigated:
- Is it a false positive or real attack?
- Is is a targeted attack or a bonnet?
- Performed by a professional or script kiddie?
Alexey’s goal was to decloak and track the attacker to “brake his legs” as said Alexey ;-). But we can do more: replay back! Why not answer to the attacker with the same exploit back to the source. Bad guys have softwares used to attack you but they can also have vulnerabilities that could be exploited too.  In case of a web attack, was the attacker a human? Did he used a classic application. if yes, maybe we can exploit it. Based on the attack, we can have a “skill-o-meter” to classify the attack type (human/bot) and the malicious intention of the attacker. We can also use social-engineering skills to grab interesting information about our attacker and we could attack his own environment (ex: his home ADSL router). Other interesting data is pictures, text files, SSIDs, trace route, DNS, screenshots, camera recording. Alexei gave a real example performed in Russia with the Defcon Russia web portal which required a “invite code” to enter. It was of course a honeypot with a rogue Java applet ready to be downloaded. Big warning: when doing this, do never store personal data just technical info! Another problem: the attacker may use multiple proxies, TOR or pivot via another compromised box. Once you grabbed some data from the attacker, it’s easy to correlate them with other sources to find even more interesting stuff (Google is your best friend to achieve this). Another example explained by Alexei:  How he collected data from popular free mail services in Russia. Based on his research, the following profile of attackers were detected:
- White hat companies tested the applet
- Independent researchers
- Backdoored government hosts
- Script kiddies

Conclusion: it works! Finally, a last type of attack was covered, via third party services like social networks.  If the user is authenticated on alternate services (LinkedIn is a good example) it’s easy to steal more information about him. A nice quote to conclude this presentation:
“The only real defense is offensive defense” (Mao Zedong)
Nice presentation to start the day. I would expect a bigger warning about this kind of behaviour. By attacking your attacker, you cross a line and could be seen also as a “bad guy“. Take care when playing this kind of game.
Then, Thomas Roth presented “Next Generation Mobile Rootkits”. Mobile devices security remains a hot-topic during this edition of BlackHat! Mobile root kits are use for surveillance, usage statistics and criminal activities. They are two targets: the baseband and the CPU. The baseband has a full access to memory. This talk will cover the trust zone in the CPU.

This zone is a secure processor integrated into Cortex-A CPUs. Thomas explained what is the trust zone. As a practical example, he gave Netflix. They require device-certification. For HD streams, video decoding is running on TrustZone with direct access to the screen. So, no way to record the stream on Android devices (DRM). This looks to be good protection. After coveting how the TrustedZone works, Thomas explains how to build a root kit in this zone. First why? People haven’t talked about the problems that come with TrustZone. It’s also about the vendor distrusting the user. Not easy to test on hardware but there is an open source solution to emulate a TrustedZone (qemu-trustzone). The speakers knew his topic but I was completely lost. The presentation was too complex for my poor brain.
After a good lunch, the last set of talks started with “Using D-Space to open doors” by Brad Antoniewicz. The topic was how to attack proximity card access systems. This talk is the result of researches performed about communications between cards & readers. But what is D-Space? It comes from a book written by Daniel Suarez where people are wearing some kind of glasses and are able to “control” things (like the Google glasses in fact). A classic physical access architecture looks like this:
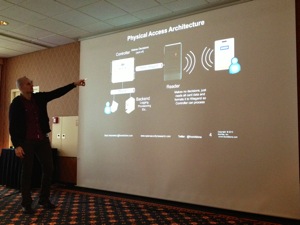
Brad created this environment for +/- $400 based on an Arduino controller. First, the reader’s job: It is to get data from the card and format it for wired transmission. An HID ProxCard contains only a number based on 26 bits split onto two sets: the facility ID/site code (0-255), the card number (0-65535) and two parity bits (pretty simple). So, there are chances that two companies use the safe facility code! Bob in company A may be allowed on site A0 and humber 100 like Alice in another company and cards can be exchanged! Risk is low but exists! How to clone a card? Proxmark3. Open source project. Proxbrute is another tool. Cards are sequentially numbered. Privilege escalation via lost, temporary or skimmed badges. iClass cards, another technology, stores the value on the card but are more secure (two levels: standard or high security). In case of the high security mode, you define the key yourself. How to get the key? proxclone.com has a technique to access the reader memory and pull the key. Between the reader and the controller, a standard protocol is used (Wiegand protocol or sometimes RS232). Wiegand tools (based on Arduino) can perform attacks: skimming, emulator, fuzzier or brute forcer. What about targeting the controller? The one used by Brad was a HID VertX v2000. This model is very popular. How to find a controller? Simply scan for open ports UDP/4070. You will get the type, the model, firmware version etc. The controller is even reachable via Telnet without password. It’s an embedded Linux with a root account and a crapy password. The password is hardcoded in the application. Change the root password, you break the controller! Interesting stuff is stored in DB files: AccessDB, IdentDB (allowed doors, time restrictions). They are populated by the backend server. You can inject your own card number in the DB using the tool developed by Brad:
./VertX_CacheTool -c 00263F9500 -r
But doing this, you generate a log entry! How to open a door in a safe (hidden) way? Using serial debugging and commands:
hwtestserial -d /dev/ttyS2 -b 38400 -p None -s1 -v 100 -txhex xxxxxxxxxxxxxxxxxx
Same via the Web UI! You can open a door using a GET request:
./VertX_WebOpen.py
It’s possble to make a door stay unlocked or locked! The last part is the backend. What can we do? It’s called WebBrix. It runs on Windows with a default SQL db (sa with no password). A service is running on port TCP/4070. The protocol is plaintext by default (encrypt not default). Here again, the application is crappy and vulnerable to multiple attacks.
Code of tools is available online: github.com/brad-anton. Unfortunately, due to a technical problem (a missing 110v – 220v converter), Brad was not able to perform a live demo. A great talk with practical stuff! You should never see your access badges from the same point of view!
And we continue with another talk! “Dude, where’s my laptop?” presented by Simon Roses Fermeling and Curro Marquez. Every day, thousands of mobile devices are lost or stolen. Often they contain personal or corporate (but critical on both cases) data: contacts, emails, photos, passwords, apps, etc. There is a huge market behind this and vendors propose lot of solutions to protect our beloved toys. But are they really efficient and what do they do if the device is stolen? That’s what covered Simon’s talk. First he performed a revue of the market. Here are two interesting statistics?
- 10K mobile phones are stolen per month in London
- Laptop thefts totalled more than $3.5 millions in 2005

There are two technologies that apply to mobile devices: BYOx (“x” means whatever you want) and MDM & co family. What are their anti-theft features? Encryption, remote wipe of files, screen lock, info sent to a C&C like IP addresses, GPS location, camera shot. They claim to offer strong security and helping to recover the device. Is it true? How to find a good one? Google Play reports 1000+ results when you search for “anti-theft” (for Android devices). The marketing message is: “Just relax“:

They lack of a good design. How data is protected: at rest/in transit? Can wiped data are really gone? Can tempering be detected and stopped? So, how work thieves? Simon demonstrated some techniques. They can attack via the network, via the system or reverse-engineer apps. Most anti-theft solutions are visible. Should not be a good idea to cover itself and work silently? Some solutions are not secure at all and send data in plaintext over the air. Physical access to can achieved in a Faraday box/bag to avoid any connection. Keep in mind: No connectivity = no protection. Â Attackers have plenty of time to root the device. Here again, apps store data in cleartext (data at rest) or weak crypto is used (MD5 without salt). A first demo was shown (video) about Prey and how to bypass the lock out, so easy! The next feature reviewed by Simon was the secure wipe. Apps do not have secure delete capabilities and many times SD cards content is not deleted. Tip for thieves: once the device is stolen, remove the SD card as soon as possible! If data is wiped, it can be recovered using forensic tools. Simon developed a tool called “John Hard Vegas” (will be available by next week). It can detect anti-theft tools, disable them and steal credentials. From an attacker point of view, how can we insert a root kit in the stolen device?
- Shield device
- Tamper device
- Install root kit
- Enable anti-theft
- Return device
- Owner happy!
Then followed a ssecond demo: Via a Backtrack distro which played a MitM attack and intercepted communications with the server and sent rogue data back to the client. Â Awesome. Conclusions to this talk are a huge amount of risks. The first one is the lack of encryption. And when used, it’s via poor algorithms. Apps are unsafe too (debug mode enabled, no data validation). Data is not safely wiped and they can be easily defeated. Maybe the best solution is to keep an eye on your devices and beware of public networks. A last message to the vendors: build secure software not security software. Very nice talk!
Finally, Jacob Williams talked about cloud application with “DropSmack: How cloud synchronisation services render your corporate firewall worthless?“. Jacob developed a course on cloud forensics and is the right guy to talk about synchronisation services like Dropbox. He demonstrated how to use Dropbox to p0wn a protected corporate network and how to use DropSmack. Why Dropbox? Because it is the “Coca-cola” of the synchronisation softwares. It provides a command and control channel by design! Infecting files destined for a backup could be interesting.

Dropbox suffered of some major authentication issues (like the “no password” day in 2011) but nobody is really looking at alternatives. Nothing news, in 2011, the idea to use synchronisation software already emerged. Everytime something was disclosed, Dropbox fixed it. Dropbox was already a topic of security talks in conferences. Jacob gave a real example with a client who asked him to perform an “APT-like” attack. The standard methods failed as well as physical security. Spam was also blocked. He looked for an alternative and found a personal email address: the one of the CIO. With an email address it was easy to own the laptop and this guy was using Dropbox! How to grab his credentials? The Dropbox DB was encrypted. Dropbox could be used to infect the internal network and be the C2 channel. They needed a malware which could communicate with a Dropbox sync process (not a regular meterpreter). Dropsmack was born! Data exfiltration and command output are also sent via Dropbox. It implements the following basic commands: PUT, GET, DELETE, EXECUTE, SLEEP, MOVE. How to deploy?
- Embed DropSmack in a doc already synchronized
- Add some macro goodness
- Load file back
- File synchronizes
- Have a coke & wait 😉
What can we do with DropSmack? The PUT command allows to upload an EXE but name must not be .exe or dropbox will delete it. GET is the opposite. EXEC executes a file with the user privileges. Best is to output to a file and download it with a GET command. MOVE and DEL don’t need a description. SLEEP can be used to minimise the impact of pop-up’s displayed on the victim desktop after each synchronisation (could be annoying). How to detect DropSmack? IDS: worthless, Firewall: mostly worthless, AV: no comment, DLP: same. Only whitelisting software won’t let the new application (DropSmack) to execute. Will a NG firewall save you? In  2012, more than 75% of respondents to a NGFW survey said that their workload increased due to application controls (like the IDS in the 90’s). It remains a black or white decision to allow Dropbox on your network? What if you device to allow DropBox? It uses LanSync (port 17500 UDP/TCP), block access to Amazon S3 (used by Dropbox), not doable. Not easy and again will increase your workload. It’s time to talk to your management and find out what’s the best policy for synchronisation services. Jacob finished his presentation with a live demo of DropSmack. What about the future? Read and extract information from DropBox configurations, allow alternative default Dropbox synchronisation folder and get rid of the boring popups! Awesome talk to end the day.
This closes the BlackHat Europe 2013 event! A good event where I met lot of new friends. Just one remark to the organisers: For the next edition, give me attention to the Arsenal. Try to promote it more and setup sessions during breaks to attract more people. Now, it’s time to drive back to Belgium and let’s enjoy the weekend! Have a safe trip back to $HOME!
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #2 http://t.co/BwgMEjLwVL
RT @xme: [/dev/random] BlackHat Europe 2013 Wrap-Up Day #2 http://t.co/BwgMEjLwVL