 After months of preparation with a growing pressure, the 0x04 edition of BruCON is already behind us! I was still on board to take care of all the bits & bytes aspects. This year was a specific one. The venue changed (we moved from Brussels to the beautiful city of Ghent). For me, this move had another major impact: the venue was provided without any network connectivity. The challenge was to build a network from scratch! As you can imagine, deploying a network services to 500 hackers during two days is not easy. Yes, dear attendees, you aren’t common users 😉
After months of preparation with a growing pressure, the 0x04 edition of BruCON is already behind us! I was still on board to take care of all the bits & bytes aspects. This year was a specific one. The venue changed (we moved from Brussels to the beautiful city of Ghent). For me, this move had another major impact: the venue was provided without any network connectivity. The challenge was to build a network from scratch! As you can imagine, deploying a network services to 500 hackers during two days is not easy. Yes, dear attendees, you aren’t common users 😉
To increase the presssure, another last minute change occurred: We were allowed to access the venue on Wednesday starting from 07:00AM (only two hours before the opening of the conference). But the challenge was completed and visitors were able to take their breakfast while surfing the web! I’d like to congratulate the volunteers of the network crew who did a great job!


If building a network from zero is a real challenge, it has also advantages. The most important is a full-control of the infrastructure: bandwidth, switches, servers, access devices, services and… logs! Yeah, logs, one of my favorite topic. As you can imagine, everything was logged during the event. First of all to keep traces (evidences): According to the Belgian law, when you provide an Internet access, you are considered as an Internet provider and have to take care of your network. Secondly, to analyze the logs and generate nice stats. So, let’s check what our visitors did during the two days?
First, the bandwidth. If the new venue was a great location, it was also lacking of Internet point of presences! After long investigations, the only solution was to use a WiMAX link! This kind of solution being expensive, we had a limited bandwidth compared to the previous editions but, hopefully, it did not affect the visitors who surfed smoothly.
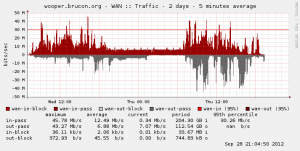
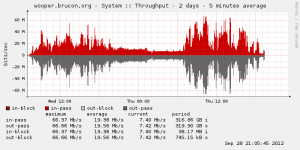
What about our visitors? It looks that many of you are scary to use offered WiFi networks and prefer to use data connection via your mobile devices. I was surprise to see a very low amount of concurrent devices connected to the network (peak: 189 DHCP leases). During the conferences, we offered 10111 leases to 416 unique MAC addresses. What about the type of devices?
| Manufacturers | Detected MAC Addresses |
| Intel | 189 |
| Apple | 95 |
| Samsung | 33 |
| AzureWare | 31 |
| Hon Hai Precision | 26 |
| VMware | 23 |
| Liteon Technology | 13 |
| RIM | 9 |
| HTC | 9 |
| Cadmus Computer Systems | 9 |
We operated our own DNS relay to log all the queries. 356885 queries were performed (only “A” records). A total of 43480 unique URLs were resolved by the DNS. Here is the top-20 of resolved hosts:
| Domain/FQDN | Queries |
| google.com | 22104 |
| ubuntu.com | 21178 |
| daisy.ubuntu.com | 19569 |
| brucon.org | 18862 |
| twitter.com | 12686 |
| thehexfactor.org | 10940 |
| e3191.c.akamaiedge.net | 6776 |
| t.co | 14027 |
| logs.loggly.com | 6025 |
| apple.com | 5518 |
| www.facebook.com | 5411 |
| www.google.com | 4781 |
| api.twitter.com | 4347 |
| google.be | 3329 |
| microsoft.com | 2812 |
| thf.brucon.org | 2504 |
| google-analytics.com | 2310 |
| icloud.com | 2293 |
| nettitude.com | 1976 |
| ssl.gstatic.com | 1855 |
I was surprised to see logs.loggly.com in this list! This FQDN is used by the Loggly (a cloud logging service) API to submit logs! Somebody was submitting events during the conference!?
The web traffic was also analyzed. Here is the top-10 of websites visited from the BruCON network.
| Websites | Visits |
| google-analytics.com | 2926 |
| google.be | 1775 |
| google.com | 1486 |
| facebook.com | 1264 |
| twimg.com | 1230 |
| twitter.com | 1185 |
| scorecardsearch.com | 913 |
| quantserve.com | 839 |
| double-click.net | 781 |
| googlesyndication.com | 719 |
What about companies present at BruCON? Using a simple grep, it’s easy to retrieve a list of organizations. Often, the internal domain ends with “.local” or “.corp“. As some visitors are still using corporate devices during the conference (ouuuh, bad!). We extracted some names and were happy to have visitors coming from (a very short list):
- altum.local
- certezza.local
- erasme.local
- kpnnl.local
- nsense.local
- swift.corp
Amazing, just for the swift.corp domain, I collected 29 unique internal server names! Like the previous edition, there was also an IDS (standard config & rules). It remained calm and nothing special was detected (this does not mean nothing happened! 🙂
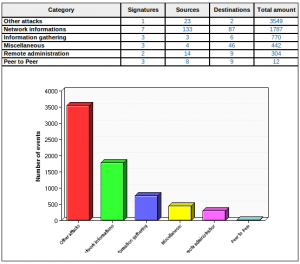
All communications were blocked between clients to avoid internal floods, scans and other funny stuff. Finally, a few words about our wall of sheep which was successfully tested (and approved? 😉 by some our visitors:
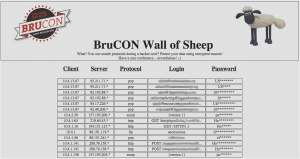
I can’t resist to give you some numbers (again):
- 4506 events logged
- 4 protocols detected (SNMP, HTTP, POP, FTP)
- 76 unique logins detected (real: ~50 due people playing with the wall)
Unfortunately, we could not provide IPv6 connectivity this year, it’s on our todo list for the next edition. Other data were collected but they will be covered in another blog post… Stay tuned!
I was not able to process the traffic. The appliance was delivered with a bad upgrade path and prevented sandboxes to run 🙁
Next year maybe…
What have been detected by FireEYE during the conference ? Which kind of appliance did you use, WEB / MAIL.
The U1 server (in the middle) was the firewall/DHCP/DNS (basic network services)
The orange (yellow? 😉 box was the network sniffer (syslog concentrator, wall of sheep, network stats)
what is the server used for ? storage ?
what is the yellow device you have there ?