 This is my wrap-up of the last RSA Conference which occurred in London. As usual, it’s a mix of t-shirts and ties. But, vendors followed the rules of the game and came with less promotional material for their next-top-ultra-last-generation-solution-to-beat-all-hackers-from-outer-space.
This is my wrap-up of the last RSA Conference which occurred in London. As usual, it’s a mix of t-shirts and ties. But, vendors followed the rules of the game and came with less promotional material for their next-top-ultra-last-generation-solution-to-beat-all-hackers-from-outer-space.
As usual, the first half-day was dedicated to keynotes with great speakers. As organizer, RSA started the show with an introduction to current threats and what are the common countermeasures to implement (like continuous monitoring). Nothing new, just keep in mind that “people are the new perimeter“. Then, Thomas P. Heiser came back on the major security breach that hit RSA a few months ago. Based on this true example, he explained how to survive a major security incident. Question to RSA: Why didn’t you implement this before the breach? The third speaker was Herbert ‘High’ Thompson, a regular guest… So brilliant speaker! He explained the science of security fragility using the image of “pillars of trust”. Using funny examples, he explained five immutable laws:
- “Secure” systems fail in the face of “out of context attacks”
- Expect failures!
- People (employees, contractors, suppliers, …) will make mistakes. Plan for them!
- Assume your environment is contested and behave accordingly
- Constantly reevaluate assumptions. Pillars of trust can erode quickly!
The last keynote was presented by Microsoft and was way too much commercial! The only interesting stuff to remember is the fact that zero-day vulnerabilities are not the biggest threat. 99% of attacks are performed against vulnerabilities which already have patches available. (Source: the Microsoft SIR). Don’t you still have some patches to install? After the lunch, the track sessions started.
The fist one I attended was presented by Ira Winkler about “How to recruit spies on the Internet“. Ira started with a brief review of social networks. Do you remember applications/protocols like IRC, NNTP (Usenet) or Compuserve? The youngests amongst you certainly no. Those were already social networks! What are the motivation for spying? This can be resumed with the acronym “MICE“: “Money, Ideology, Coercion and Ego“. Ira demonstrated how spies find people on social networks and “force” them to steal information. Interesting talk. He prefers to refer to “human elicitation” instead of “social engineering“.
I also attended the talk of Ivan Ristic about mitigating SSL/TLS threats. Ivan’s slides were updated with the latest information from the SSL world but it was the same presentation as HITB Amsterdam. Note to the organizers: next time, schedule Ivan in a bigger room! He’s a great speaker and there was plenty of people interested on this topic.
The last presentation of Tuesday I attended was “Emerging threats in mobile computing” by Adam Meyers. No breaking news but a nice review of the current issues that organizations are facing with mobiles devices. What to keep in mind? Attackers choose their targets based on the number of sold devices (broaden surface attack) instead of the technology! Most mobile devices have a too restricted API (locked down) which prevent good security software to be developed.
The day two started with a presentation of Mike Shema about HTML5 and its security pitfalls. As I’m a newbie with the new version of the HTML standard, it was a good opportunity to learn more about its security. Basically, the scope of HTML5 is to add canvas, audio and video capabilities to the existing standard and to replace the well know applications like Flash, Silverlight and anything that loads in a browser. It reflects the changes of modern websites. First, HTML5 does not fix the problems of HTML but adds:
- Security from design
- Prepared statements (SQL injection)
- Cryptography
- X-Frame-Options header (click-jacking)
- Origin header (XSRF)
Note that security depends mainly of the user behavior: Browser tabs do not enforce security and think about URL shorteners or QR-codes! HTML5 also implements several new “risky” features:
- Parsing surprises (single quote vs double quotes)
- WebWorkers: worker() and sharedworker() enable threading within JavaScript. A funny DoS attack is to create a loop which will consume CPU cycles and drain batteries of mobile devices.
- WebStorage is a new place to put contextual information but which should be stored on server side! This is a nice place to search for sensitive information.
- WebSockets allows new ways to make XSS more interesting, host detection, post scanning, DoS or information stealing.
- WebGL crosses the boundaries from user-space to kernel-space drivers.
To protect against those issues, there is only two ways of working:
- Considering the code! Developers have to write clean code. Use frameworks (ex: jquery), it’s easy and safe, just update the framework to get rid of security issues.
- Control the “plugin plague” and restrict the extensions installed in your browsers.
More information is available on html5sec.org. The slides are available on www.deadliestwebattacks.com.
Keynotes were back until the lunch. Sean Doherty (Symantec) presented an history of attacks and to what ask customers? Basically: balancing the information security budget, protection of their heterogeneous complex infrastructure against complex attacks and how to control their information explosion. The presentation ended with more focus on some Symantec products, sad. That’s good to protect the information but first where is it and in which form?
Then, a panel about APT followed (again and again, same story) and a lecture from Stefano Grassi (Poste Italiane) about the state of cyber-crime in Europe. I’m certainly not a top speaker but coming on stage and reading a paper without intonation… No way! Finally, the first half-day was closed by a nice presentation of Cisco about its new product (again commercial info!) to control the information flows. Basically, Cisco said that the mainframe was replaced by PC’s and now they are replaced by mobile devices. Those are more and more difficult to control. Based on a W^4 model (who / what / when / where), Cisco focuses on the layer 7 to analyze the data.
Just after the lunch, I attended one of the best track of the day: Mitja Kolsek spoke about “Remote binary planing – An overlooked vulnerability affair”. This vulnerability exists for years in Microsoft applications and can be qualified of “super-start”. It allow arbitrary code execution, is easy to find and exploit, is reliable, requires no specific privileges, can be executed remotely and work through firewalls! Secunia maintains a list of unsecure library loading”. This vulnerability exploits the “DLL Search Order” implemented in the LoadLibrary() function. The “CWD” or “Current Working Directory” is in the search path of any DLL loaded by an executable. The goal is to make the application access a rogue DLL in this CWD. How? Some developers assume that a DLL is local, some DLL aren’t present in newest OS (like dwmapi.dll), some software are partially installed or customized. Finally some applications work based on assumptions like media players (the CODEC must be available). To inject the malicious code, the DllMain() function almost always works or the original DLL can be modified. The attack is performed in three steps:
- Plant a malicious DLL
- Set CWD to the directory where resides the DLL
- Wait! 😉
Windows changes the CWD often: when you double-click on a file in Explorer, during file open/save operations, so it’s easy to force
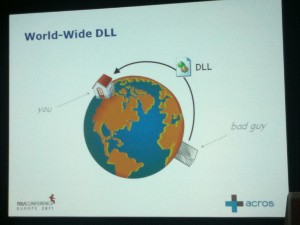
- (Planting a DLL from a remote share)
the user to change its CWD. If the rogue DLL is located on a remote share, firewalls are not an issue: by design, Windows falls back to Webdav if SMB does not work(!). A live demo was performed. A .vcf file was opened by Outlook Express which loaded a rogue DLL in the same directory. Pwn3d! During his research, Mija found that most Windows applications are vulnerable. How to protect? Use absolute paths to libraries and executables and follow guidelines available on www.binaryplanting.com.
You know SQL databases but do you know NoSQL databases (ex: MongoDB)? Bryan Sullivan presented a track about attacking and defending NoSQL. First, all NoSQL instances discourage using authentication(!). A simple port-scan is a win to find DB servers. Bryan focused on the combination of MongoDB + PHP and prove that injection are still possible even if no SQL is used. Example:
http://www.server.com?user[$ne]=admin&pass[$ne]=admin
Interesting talk based on my zero knowledge of NoSQL! The next presentation “Why technical metrics aren’t enough?” looked interesting by reading the abstract in the conference brochure but I did not like it. The idea was interesting: instead of using classic security indicators (like vulnerability scans and password policy), ten things were presented that you need to monitor for efficient security reporting.
The day ended with a presentation of the Verizon Data Breach Investigation Report by Jelle Niemantsverdriet. First, thanks to him for the big mention to a previous blog port: “All You Need Are Logs“! One of the key quote to keep in mind was: “Brains beat boxes“. No need to deploy new security solutions without analysis the situation first! Use your time, plan, prepare and test.
The last day started earlier with a talk about “database firewalls” by Steve Moyle (Oracle). Why do we need a database firewall? Simply because databases are involved in most attacks! They contain interesting records or can be used to propagate malware code (JavaScript/iframe injection). Traditional security solutions leave data stored in databases vulnerable. By definition, a DB firewall is
“A device or program that controls the flow of network database traffic between networks and databases hosts that employ differing security postures“
They must understand the language of databases: SQL. First line of defense: monitors and control, prevent SQL injections, unauthorized access, misuse of DB privileges. Of course, logging is important and interaction can be captured (for forensic or compliance requirements). What are the challenges? To support different vendors and DB, network access, architecture. Network sniffing is a key issue: where to deploy them? Amongst basic controls (select, drop, insert), some more complex controls are
- DB Firewall
sometimes required like alerting of 500+ records of the same table are returned. How the firewall blocks forbidden data? It drops the database connection, drops the request/reply packets, disables user account or replaces the SQL with benign alternative. Some of them are complex to implement (require interaction with the DB server). Database traffic is often importand (millions of requests/day). Receding the false positive if a key success factor! Interesting presentation but, like Web Application Firewalls, they can be used to mitigate attacks but the developers/DBA’s must do a good job. That’s the key!
The second talk was about consoles! by Christopher Boyd (@paperghost). That was a good surprise for Christopher to see his talks accepted by the reviewing committee! It’s a digital domination: millions of consoles were already sold (all models) and data send to network by players are valuable (do you remember the “Sony” story?). Players connects console online but don’t get a clue about what are the threats. A 2010 survey showed that 49% of players have a console in workplace. Manufacturers have tips to increase security but players don’t read it/apply it. Your account value is directly related to your score on the black market. War never changes: Different types of attacks exist again gamers (DDoS, traffic poisoning), sneak attack (social engineering). Direct attacks allow messages to be posted on screen during game sessions (ex: phishing websites) .
What about forensic and audit in port IPv4 address exhaustion world? Eric Vyncke make a great presentation (the best of this day). First, he reviewed the status of IPv4 usage by our Internet Service Providers. They are changing the Internet due to IPv4 exhaustion and deploying IPv6. Service providers are deploying NAT between the customers and Internet (“carrier grade NAT”) and are deploying IPv6 in parallel. What’s the impact of sharing IPv4 addresses? NAT breaks some applications! Modern websites are using multiple AJAX connections. Imagine one IP address shared amongst 1000 customers: This reduce the number of ports per customer. A nice example was given using Google Maps. But what about business applications? Other problems will arise:
- What about IP reputation? If you share IP’s with a spammer?
- DoS mitigation? Can we still blacklists IP?
- What about rate limiting? (Google sorry page)
Data retention is also problematic: Logging the source port is mandatory. From NOW, Eric recommends to start logging the source ports in your applications! Note that this may have a huge impact on your log management tools. Great talk with nice tips & tricks about IPv6 security.
After the lunch, it was my turn to be on stage. I presented my talk “All your logs are belong to you!“. A lot of people attended and I had interesting questions/contacts. A bit stressed but it went well.
The day finished with Rick Howard now presenting “An Insider’s Look at International Cyber Security Threats and Trends†and with Sir Tim Berners-Lee, himself, the inventor of the World Wide Web. He spoke about his vision of online security, even if pretending to not be a security professional. That was cool to listen to a great personality like him.
RSA remains a conference focusing on “defensive security” (compared to “offensive security” presented at other events like BlackHat or BruCON). In parallel to the talks, like all conferences, it was an good occasion to meet again friends and make new ones!