 Who is not protected by a firewall today? Nobody! Our Internet (as well as local) traffic is inspected by multiple firewall layers. They are present everywhere: on Internet gateways, in front of data-centers, between departments, even your workstation is running a firewall. For a few years, a new type of firewalls has emerged, called “Next Generation” firewalls. What’s the difference with classic ones? Roughly, new players are really filtering packets up to the 7th layer. Instead of old-fashion rules like “IP a.b.c.d is allowed to connect to IP e.f.g.h on port xxx“, Next Generation firewalls understand: “User JohnDoe is allowed to use MSN but he cannot transfer files“.
Who is not protected by a firewall today? Nobody! Our Internet (as well as local) traffic is inspected by multiple firewall layers. They are present everywhere: on Internet gateways, in front of data-centers, between departments, even your workstation is running a firewall. For a few years, a new type of firewalls has emerged, called “Next Generation” firewalls. What’s the difference with classic ones? Roughly, new players are really filtering packets up to the 7th layer. Instead of old-fashion rules like “IP a.b.c.d is allowed to connect to IP e.f.g.h on port xxx“, Next Generation firewalls understand: “User JohnDoe is allowed to use MSN but he cannot transfer files“.
Regardless the firewall types deployed, all of them have security holes! Just because firewalls are maintained by human and we are… well known to make mistakes! Today’s organizations are protected by plenty of firewalls developed by multiple vendors. They are managed by multiple teams working in shifts, in different countries or outsourced. One of the biggest issues is to assume that firewalls are bullet-proof. Good examples are some risks assessment frameworks. Auditors are mandated to audit an organization security perimeter and base their job on checklists:
- Do you have a firewall? [Yes|No]
- Does your firewall have a high-availability configuration? [Yes|No]
- Does your firewall implement state-full inspection? [Yes|No]
If you answered “Yes” to those three questions, there is absolutely no warranty that your business is safe! The firewall policies (security, NAT, etc) must be regularly reviewed to avoid common errors. They are often not committed to harm the organization security but are just the result of human mistakes. Here are some examples:
- Errors while calculating subnet masks
- Typo-errors (so dumb!)
- Deleted allowed protocols in a rule which became “Any”
- Bad anti-spoofing (no knowledge of the topology)
- Too permissive rules
- …
Any change applied to a firewall policy might have a bad impact on the business: servers can be temporary disconnected from the Internet, from the rest of the network or (worst!) dangerous protocols can be allowed from the Internet. That’s why regular firewall audits must be performed and tools exists to help auditors in this way. From my point of view three big axes must be audited:
- Security on the firewall itself (using the “W^4” principle: Who did What, When and Why?)
- Policy compliance (with the organization rules, the legal rules or business compliance requirements)
- Performance
Why performance? Security rules are processed in a sequential order (top-down). Unused rules must be removed and the most used must be moved on the top of the policy. Some available tools are commercial and others are free. Let’s have a look at Flint. It is a free (open source) tool provided by Matasano (they also developed Playbook, a tool for synchronizing firewalls configurations from a web-based console). Flint will analyze your firewall policy and report detected issues:
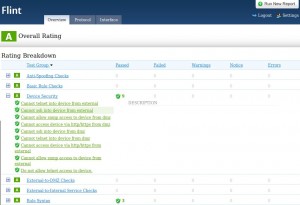
From the different axes describe above, Flint will only address the security but it does it quite well. It examines your firewall rules (via a file upload or a copy-paste in a text area) and highlights the discovered problems like rusty configurations, permissive rules. It’s a nice tool to perform a sanity check of your new rules before their implementation. Flint could also help you to put your hands in complex configurations. At the moment, the following firewall models are supported (in version 1.0.4):
- Most Cisco devices, including the PIX ASA
- Open source firewalls, including BSD’s excellent PF and Linux iptables (“soon”)
As Matasano supports Netscreen/Juniper in Playbook, I hope that the support for those firewalls will be added soon. I downloaded and played with the VMware version and it seems that PF firewalls are already supported. For sure, the tool lacks of documentation at the moment. Keep an eye on the product, once more firewall supported, it could be a nice audit tool! But using free or commercial tools, keep an eye on your firewalls!