 Here is a Python script that I developed for my personal use: mime2vt.py. I decided to release it because I think it could be helpful for many of you. In 2012, I started a project called CuckooMX. The goal was to automatically scan attachments in emails with Cuckoo to find for potential malicious files. Unfortunately, the project never reached a milestone to use it smoothly. Maintaining a set of Cuckoo sandboxes is really a pain and consume precious computing resources, so why not use the cloud? Yeah, the evil cloud can also be useful!
Here is a Python script that I developed for my personal use: mime2vt.py. I decided to release it because I think it could be helpful for many of you. In 2012, I started a project called CuckooMX. The goal was to automatically scan attachments in emails with Cuckoo to find for potential malicious files. Unfortunately, the project never reached a milestone to use it smoothly. Maintaining a set of Cuckoo sandboxes is really a pain and consume precious computing resources, so why not use the cloud? Yeah, the evil cloud can also be useful!
I wrote a new Python script which extracts MIME types from emails and checks them against virustotal.com. I’m using it to scan my spam folder. But the domain rootshell.be has been registered in January 2001, this means that I’ve email addresses in almost all spam lists over the world! Besides scanning some private addresses, I’ve a catch-all address which sometimes receives  very interesting emails! The last update was to integrate the script with Elasticsearch to have a better reporting.
The implemented features are:
- Use your own virustotal API.
- MIME attachments can be dumped in a directory (for later investigations)
- Unuseful MIME types can be excluded (ex:Â image/png,image/gif,image/jpeg,text/plain,text/html)
- Results are logged via Syslog
- Zip archives are inspected/processed
- Virustotal results are send to an Elasticsearch instance
The primary purpose of this tool is to automate the scan of attachments for juicy files. It does NOT protect (no files are blocked). Here is an example of logged result:
Nov 18 13:48:25 marge mime2vt.py[5225]: File: 7ce782ba4e23d6cf7b4896f9cd7481cc.obj \
(7ce782ba4e23d6cf7b4896f9cd7481cc) Score: 0/55 Scanned: 2014-11-17 08:29:14 (1 day, 5:19:11)
Dec 12 18:41:20 marge mime2vt.py[1104]: Processing zip archive: 4359ae6078390f417ab0d4411527a5c2.zip
Dec 12 18:41:21 marge mime2vt.py[1104]: File: VOICE748-348736.scr \
(acb05e95d713b1772fb96a5e607d539f) Score: 38/53 Scanned: 2014-11-13 15:45:04 (29 days, 2:56:17)
If the file has already been scanned by Virustotal, its score is returned as well as the scan time (+ time difference). If the file is unknown, it is uploaded for analyzis. Optionally, the Virustotal JSON reply can be indexed by Elasticsearch to generate live dashboards:
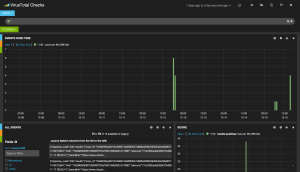
The script can be used from the command line to parse data from STDIN or (as I do) it can be used from a Procmail config file (or any other mail handling tool):
:0
* ^X-Spam-Flag: YES
{
:0c
| /usr/local/bin/mime2vt.py -d /tmp/mime -c /etc/mime2vt.conf
:0
spam
}
The script is available here. If you’ve ideas to improve it, please share!
The same could apply to Squid indeed. But a proxy manages much more potential malicious objects and performance is a key.
If a mail can be delayed by a few seconss, the end-user HTTP experience must remain good.
Hi Xavier,
I use something similar from NobsWare (https://code.google.com/p/procmail2virustotal/source/detail?r=140f633408eec0971f0464f8c816e41d1eea977e) but I was thinking of expanding this filter.
What if we could use this script for example Squid or any other proxy then SMTP – that would be really great and offers the same or better protection then SItecoms’ cloud security (http://www.sitecomcloudsecurity.com/about.aspx) – which exactly does that: create a hash of the contents and compares the hash with an online database (possible even Virustotal?).
What do you think of this?
Perhaps a squid redirector or such can run the script and gives a 403 on a hit?
Cheers,
Michiel
RT @xme: [/dev/random] Automatic MIME Parts Scanning with VirusTotal http://t.co/bTxxvk7NMv
RT @xme: [/dev/random] Automatic MIME Parts Scanning with VirusTotal http://t.co/bTxxvk7NMv
RT @xme: [/dev/random] Automatic MIME Parts Scanning with VirusTotal http://t.co/bTxxvk7NMv
RT @xme: [/dev/random] Automatic MIME Parts Scanning with VirusTotal http://t.co/bTxxvk7NMv
RT @xme: [/dev/random] Automatic MIME Parts Scanning with VirusTotal http://t.co/bTxxvk7NMv