 BlackHat is back in Amsterdam and here is my wrap-up for the first day. It rained all my way to Amsterdam this morning but it will not prevent motivated people to join the Amsterdam RAI where is organised this 2014 edition of BlackHat Europe! They moved from the center of the city to a bigger conference center. Nice place, but far away from bars and restaurants. After the classic registration process and a nice breakfast, let’s go with today’s talks. As usual, Jeff Moss opened the conference with some facts about the event. Interesting: this year 50% of the audience is coming for the first time! Fresh blood is always good. People came from 68 different countries (eg Brazil, Surinam, Ukraine,..). Jeff’s message was also: feel free to ask questions, participate and learn… The community is very important.
BlackHat is back in Amsterdam and here is my wrap-up for the first day. It rained all my way to Amsterdam this morning but it will not prevent motivated people to join the Amsterdam RAI where is organised this 2014 edition of BlackHat Europe! They moved from the center of the city to a bigger conference center. Nice place, but far away from bars and restaurants. After the classic registration process and a nice breakfast, let’s go with today’s talks. As usual, Jeff Moss opened the conference with some facts about the event. Interesting: this year 50% of the audience is coming for the first time! Fresh blood is always good. People came from 68 different countries (eg Brazil, Surinam, Ukraine,..). Jeff’s message was also: feel free to ask questions, participate and learn… The community is very important.
The day started with the Adi Shamir’s keynote and some crypto. Ouch, crypto is hard to start a day but, after some theory, funny stuff was explained. Adi is currently the Borman Professor of Applied Mathematics at the Weizmann Institute of Science and his main area of research is cryptography. He is a co-inventor of the RSA algorithm. To resume, he’s the “S†of RSA!
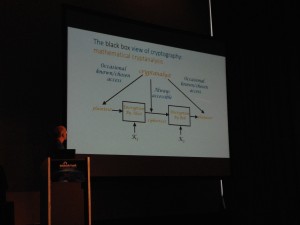
Today, writing paper about mathematical cryptanalysis is getting easier because we have many more targets to attack and more tools. But the definition of success also changed: it’s not only finding the secret key but comparing output of a system with garbage. On the other side, it’s also getting harder to get a practical impact: mathematical attacks had forced practitioners to dump cyphers. For years, we faced examples of attacks against crypto: DES, WEP, MD5/SHA1, etc… Then Adi came back to one of the simplest side-channel attack: power analysis. The goal is to check the fluctuations of power consumed by a device when it performs crypto operations. Can we use this technic to break the RSA scheme? Can we compare curves when coing mathematical operations and compare them. A paper was published at crypto2014: RSA key extraction by listening to computer. The question which then comes is how effective are tempest protections? Adi started to work on a new research: long range bi-directional communication with an air gapped computer system containing only untempered hardware. I played with this for the last few weeks. Imagine a nice building (pentagone) with many secrets. B. Schneier suggested to use an air-gap to protect from NSA. Really? First, the hardware solution is to install a mini-transmitter to the device. This requires just a one-time access to the device. Simple but very intrusive! And what about a software solution? In this case, again we need a one time access to the machine to plant a malware (via a USB stick, a phishing campaign, …). But once done, how to “talk” to the planted malware? That’s the “holy grail” of cyber-attacks: How to communicate with this device in an inaccessible location, let’s say 1200m away from the target. Challenge accepted by Adi! Using a simple scanner/printer and one flash light, Adi explained how we can send data to the printer by flashing the lights with specific sequences. The next step was to test the same from far away with a lazer. Adi wrote an application to program the laser to send messages. A possible attack scenario is the following: a malware initiate a scan at a certain time, get the scanned image and interpret it. But this can be very suspicious. Otherwise, let the victim scan a real document and use the lines from the edges! But what about ex-filtration of data? How to use the printer in the reserver direction? The attacker can pick up the scanning light emanating at night from the dark room. This is very slow. To improve the view to the printer, Adi used a drone to record lights from a higher position. In conclusion, they called the new technique “SCANGATE“. Take care of your all-in-one printers and a as  countermeasures, use black curtains or put the devices away from any external lights. This was a very nice keynote but practically the scenario is very difficult to implement in the real life but it makes you realize that attackers can have plenty of ideas!
BlackHat being a four-tracks conference, it is mandatory to make choices amongst the huge amount of interesting talks. The first one for me was a talks about Network Attached Storage (NAS) systems: “N.A.S.TY Systems that store network accessible shells†presented by Jacob Holcomb. A scaring fact to start: 100% of systems tested were vulnerable…And recently, Qnap was found to be vulnerable to shellshock. Jacob’s proof-of-concept was to develop a self-replicating code across devices. Many people / companies use NAS, so the attack surface is very big. Some key players: QNAP, Seagate, Netgear, D-Link, Buffalo. Classic configuration services are telnet, ssh, http but they also have an unnecessary service: a link to the “cloudâ€. 50% can be compromised without authentication and 22 CVE numbers were assigned by MITRE. Far worse than routers!

The testing methodology used by Jacob was classic: scanning, banner grabbing. investigating running services, analysing web applications, static code analysis and fuzzing. Different type of vulnerabilities were discovered: command injection, XSS, buffer overflow, lack of access control, info disclosure, backdoor, broken session management. Jacob gave some tips (countermeasures) for developers like to use the available API instead of calling system(). If you don’t have an alternative, just allow expected commands, nothing else!
What about a mass e exploitation Jacob performed a demo of his N.A.S.Ty worm… He focused on 3 targets: D-LINK DNS345 – TRENDnet  TN-200 / TN-2011T1 and WD MyCloud EX4 but others may be vulnerable too! How does it work?
- Scan for tcp/80
- Fingerprint
- Exploit
- Download & run the code
- Rinse and repeat
Jacob did a life demo of his worm against NAS located in the room. Once the worm infected a NAS, it kills itself and start scanning for other victimes from the newly infected NAS. Note that it does not check if the NAS is already infected. This means that more worms can run simultaneously and make some kind of DoS (slow response, bandwidth usage). A special mention to the project “hack routers and get paid” (see sohopelesslybroken.com. What about the remediation? For the vendors: transparent patch management, add security checks, apply security principles (like least privileges). For consumers: harden your devices! The worm part was interesting but we already knew that devices like NAS’s have a very weak security maturity!
After a first coffee break, my heart was balancing between SmartMeters and the “Internet of Things†stuff. As I already attended presentations about SmartMeters in the past, I decided to follow Candid Wueest’s talk, called “Quantified self – A path to self-enlightenment or just a security nightmareâ€. Candid started with a definition of “quantified selfâ€. Is it a new buzzword? The goal of those technologies is to record everything about your life (sleep cycles, calories, steps, heart beats etc…) .

Candid put some focus on fitness devices like the Fitbit wristband. This device records information via sensors and share them with a computer (or mobile device). Data are also sent to the cloud to perform interesting statistics and share the data with the user’s friends. Basically, if we introduce more data moves, we also increase the risks. (device, laptop/phone and finally cloud). The first issue reported by Candid was the unintentional data leak or the secret life of mobile applications. Amongst the different apps that were tests, they contacted in average 5 different domains and the winner contacted 14! Connections are used to exchange data with advertisement networks, the application provider, the OS provider, some social medias, etc. Always verify the default settings of your application. A bad example if Fitbit which add once the “sexual activity†visible to all by default! Then, passive information can also be leaked. If a publicity is displayed after the completion of an exercise, the traffic to the advertisement network can be used to detect when the user is doing some exercises. Health kits may contain PII (“Personal Identifiable Informationâ€) but 52% of the tested apps do not have a privacy policy. Your data are already analysed today. Candid gave the example of the earthquake in San Francisco where who was asleep at this time was analysed. Worse, 20% of tested apps send HTTP POST requests in clear text. And, if they use SSL, they accept self-signed certificates and don’t check revocation lists. Some cloud applications are also very bad. Some allow users enumeration (“GET /api/user/xxxâ€) others implement open relay via sendmail.php. The next part of talk was dedicated to devices using the Bluetooth low energy. It’s possible to scan for interesting devices and learn some information. As a proof-of-concept, Candid developed a “Blueberry Pi†based on a Raspberry, a USB4 dongle and a portable battery. When scanning sport events, you can collect plenty of data. He also scanned the BlackHat attendees but detected only 8 devices. The conclusion of this research? Your digital footprint will be (is already?) everywhere. Tale care when using health devices, when not used, turn off Bluetooth or the device itself, keep them updated (which is also a challenge). Look for a vendor with a security policy. This was a nice talk with a different approach of the Internet of Things.
Next to the lunch, Dan Koretsky talked about VDI (“Virtual Desktop Infrastructureâ€) with a presentation called “A practical attack against VDI solutions†and with more focus on mobile VDI solutions. What is VDI? The technology allows the user to have a remote desktop on any device: with three big advantages:
- Enablement
- Protection against DLP/lost device
- Protection against intrusion.
What are the threats with mobile VDI solutions? The first threat is directly related to “mRat” or “Mobile Remote Access Trojan” which record keys (key-logger). With the help of Checkpoint, lot of traffic was analysed and some interesting stats grabbed:
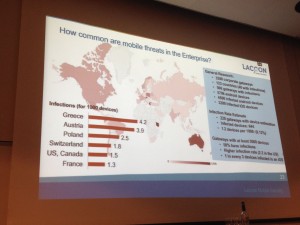
The second threat is to grab credentials locally on Android. The third one is screen scrapping. This can be done using an access to the clipboard (CTRL-A then CTRL-C) or screen recording. Finally, the fourth threat is playing a MitM attack. Nothing fancy in this presentation, nothing new, we already know that a solution like VDI is good as long as the end-point is not c compromised Finally, the last five minutes were more marketing with details about the solution developed by Dan’s company.
In a short presentation, Sergej Schumilo and Ralf Spennenberg presented their research called “Don’t trust your USB†or how to find bugs in USB device drivers? Do you remember Teensy? This small USB device was able to compromise a device by simulating a keyboard and sending keystrokes to the victim. But what’s the new motivation? To compromise a system via the USB bus. This research was done using massive usage of virtual machines with systematic and comprehensive fuzzing. The talk explained how to perform this task at a very high performance rate.
My next choice was “How I hacked your ATM with friend’s Raspberry Pi†presented by Alexey Osipov and Olga Kochtova. The topic looked interesting with a new way to use a Raspberry Pi computer. The presentation started with a small history of ATM’s. Did you know that the first ATM was installed in 1967 by Barclay’s bank? If at the beginning it was not seen as a revolution, today, we could not live without an ATM close to us to get some cash! That’s also why ATM’s are nice targets: they contain money.

Then the speakers explained their motivations behind this research? Banks are curious! Usually, the attack scenario starts with a malware injected into the ATM thanks to a physical access. It is injected using an USB stick or a CDROM. The most know attack is the one performed by Barnaby Jack “ATM Jackpottingâ€. They are also physical attacks (skimmers and pin readers). But, how hard is it to get inside an ATM? The ATM has two major zones: a “service†zone where maintenance can be performed and where the computer is installed and the “safe†zone where is stored the money. Usually, the service zone is protected by a plastic cover with a single lock. The safe zone is made of steel and concrete with rotary code or electronic locks and two types of locks. The next part of the talk was a description of the attack using a Raspberry Pi connected to the computer and remotely accessible. Once access to the ATM, a Raspberry can be installed connected to the USB bus (+ battery + wifi). They briefly explained how the attack was performed but with not many details. The presentation made during the OWASP Belgium chapter in May was much more complete! Conclusion of this talk: The service zone is important and must be properly secured, current methods of protection is not enough. Here again, nothing brand new…
If I was a bit disappointed by the presentation that I followed in the afternoon, the last one of the day was the best one (IMHO). The last talk was “Firmware.RE – Firmware unpacking, analysis and vulnerability discovery as a service†by Jonas Zaddach.

The idea of this research started with another fact: Embedded systems are everywhere! They can do a lot of things but it’s even more funny to make them talk to each others and even more to the Internet! (IoT). The classic type of embedded systems are routers, printers or VoIP systems. Jonas reviewed some nightmare stories (backdoors for routers and abusing PostScript with printers). And many many other devices… The problem is that analysis all those devices requires a lot of time. This can’t be performed  manually. The idea of the research was to make a large scale analysis to see if embedded systems suffer of the same vulnerabilities. But the problems with large scale analysis are:
- Different hardware, architectures an OSes
- Users and requirements
- Security goals
How to automate this?
- Download firmware’s
- Perform basic static analysis
- Correlate across firmwares
The big advantage is that the analysis is non intrusive, it can be performed online and it is very scalable but mainly challenges remain! The first challenge is how to get the firmware? They are multiple sources and ways to get them. There was no large scale firmware datasets available. They downloaded lot of firmwares but some of them were not available. The second challenge was the firmware identification: How to detect firmware across thousands of files? How to reliability unpack and learn formats? Example: upgrade a printer via a PS file, how to detect it as a firmware? The architecture they developed is based on a crawler which downloads and stores firmware in a db. The firmware is sent to the cloud application for analysis (unpack, static analysis, fuzzy hashing);. A password hash cracker is also available to crack found passwords. Everything is managed by a web interface. As of today, the crawler already collected 759K files (1.8TB) From those files, 1.7M files were extracted! What were the common issues found:
- Misconfigurations (configs, credentials)
- Data enrichments (keywords, banners)
- Correlation (fuzzy hashes, SSLÂ keys, credentials)
The analysis system will be available to everybody and do not hesitate to submit your firmware. The tool is available at the following address: www.firmware.re (It will be publicly available soon after the conference). The first day was closed by a reception in the business corner where people did some networking. See you tomorrow for the second day!
2 comments