 BlackHat Europe 2011 is already over! I’m waiting for my flight at Barcelona airport with Peter from Corelan Team, writing my wrap-up for the second day! It started with a talk by Sebastian Muniz & Alfredo Ortega:
BlackHat Europe 2011 is already over! I’m waiting for my flight at Barcelona airport with Peter from Corelan Team, writing my wrap-up for the second day! It started with a talk by Sebastian Muniz & Alfredo Ortega:
“Fuzzing and Debugging Cisco IOS“. Cisco IOS images are huge binary compressed files and use a single address space. This make them more vulnerable to exploits. The processes are managed by a cooperative priority based scheduler with a watchdog to kill the resources consuming processes. Cisco IOS also has a built-in GDP server but slighly different of the classic GDB protocol. To perform their researches, Sebastian and Alfredo used a free Cisco IOS emulator called Dynamips (note: even if the emulator is free, you need to have official Cisco IOS images). The emulator allows to boot several Cisco routers models. When you use an emulator to perform security research, always keep in mind: It’s a complete isolation very cost effective but you never have a 100% exact emulation. Once you found a vulnerability, you need to verify on a real system if it effectively works. How to start searching for vulnerabilities? Look for interesting strings like “Bad passwords” in the IOS image. The speakers performed some live demos using the IDA disassembler but honestly, I was unable to follow ;-). The conclusion of their talk? A router is like a regular computer or server, it runs software which contains plenty of bugs.
The second talk was also related to Cisco. Excellent presentation of George Hedfors about “Owning the data centre using Cisco NX-OS based switches“. Cisco surfs also on the “next generation” wave. Almost all vendors propose now such a version of their products. In the Cisco case, their new switches are called NX-OS. They are based on Linux system called MontaVista. They provide virtual switches environments. George started to investigate the security of NX-OS devices after he crashed a 7020 Cisco box (“oops!”) using a nine-years-old attack. He recovered the crash file, extract files from the .bin Cisco package and investigated. Routers are critical components of your infrastructure: all your traffic pass through them. If owned, packets can be altered, sniffed or injected on your network. What he found was very interesting (and scary!). First, the low level Linux system does not chroot the different available daemons running in the system. This means that a compromised daemon could have access to the whole system. Cisco provides a “DC3 shell” (which is the basic Cisco command line interface) which contains lot of hidden commands. The first research was to escape the regular interface and get a shell on the switch. How? GDB is available and allows commands like:
gdb> call system("bash")
The next founding was a very poor implementation of sudo. (“NOPASSWD” is not very safe). What about Layer-2? Do you remember the CDP (“Cisco Discovery Protocol“) vulnerability discovered by FX in 2001? (a single crafted CDP packet could cause a nice crash). In 2010, the same issue was back available in NX-OS. And, as CDP is running as root, just imagine the potential issues. Another one? Why is there a user ‘ftpuser‘ with password ‘nbv123‘. What’s the purpose of this user? No idea! Do you know the IDDQD or “God Mode“? There is one on NX-OS, “vsh” (the DC3 shell) accepts a parameter “-a” which allows all commands by disabling security roles. Nice!
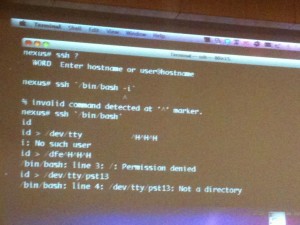
Another one? Check out the picture: ssh ‘/bin/bash’ works perfectly to spawn a root shell!
George reported his findings to Cisco a few months ago but nothing changed! In the room, a guy from Cisco was present and accepted to come on stage to answer questions. He could not do a lot but suggested to keep the pressure against Cisco to ask for a fix. Respect for this guy who accepted to open the discussion!
Last talk before the lunch break, Wim Remes gave a very nice presentation about log visualization, one of my favorite topics! First, you need to correctly collect and normalize your data before processing them via a visualization tool. It is also critical to choose the right tool depending on the results you want to achieve. A business report will be completely different of a technical or vulnerability report. To increase your reports accuracy, there are plenty of external sources that can be used (osvdb, datalossdb, cvedetails.com, …). Sometimes, 3D and nice effects have the wrong effects and make your reports unreadable. Nice & funny examples were displayed. Finally, Wim made a live demo of the Google Visualization. He also presented some bad examples and the corrected version to improve the visibility.
After the lunch and some nice discussions under the Spanish sun, back to the presentations with two guys from Radware, Yuri Gushin & Alex Behar who presented their research about DoS mitigations or “Building Floodgates: Cutting-Edge Denial of Service Mitigation“. In information security, the following physical principle remains true:
“For every action, there is an equal and opposite actions.”
It’s a fact today on the Internet that if you make profit online, you are a potential target for a DoS. And such DoS may have big impacts if your web application is stored in the cloud where, usually, you pay your bandwidth usage! What are the evolutions of attacks?
- Layer-3 – Just a flood of packets (to overload the infrastructure)
- Layer-4 – More sophisticated (it consumes more cpu). Example: a syn-flood)
- Layer-7 – Abuse applications resources (HTTP page flood, DNS query flood)
How to protect against those attacks? There are basically two operational modes: static or adaptive. The second one adapts the thresholds based on available resources). Detection may be based on the rate or behavioral. A good example of behavioral detection is the comparison of the percentage of DNS requests against the percentage of HTTP requests. And finally, they explained how to protect your infrastructure to get rid of the DoS. They developed a tool called Roboo, freely available on www.ecl-labs.org. This is an open source robot HTTP mitigator. By using Flash and JavaScript, it tries to detect real browser from bots and scripts. When a client send a request to the web server, Roboo intercepts it and, via a challenge-response mechanism, authenticate the client as a real browser (with Flash and JavaScript capabilities) or as a bot or script. In the second case, the request is rejected and will never reach the web server itself. Roboo is written in Perl and can be integrated into nginx. A live demo was peformed. Roboo blocked as LOIC DoS attack against the website. This is a first version and some improvements could be added. Note that it is also possible to add white lists based on IP addresses or User-Agents.
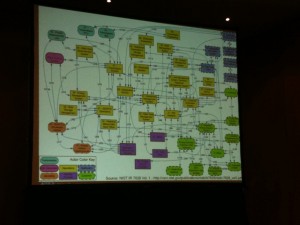
Justin Searle presented his work on another interesting topic: “Attacking and Defending the Smart Grid“. Yes, the “Smart Grid” which is often reported by media as a worst case. For Justin, this is only a marketing term which addresses several services like market operations, services providers, generation, transmissions and distribution to the customer. Each service has its own domains which are interconnected via secure communication interface. This can be represented as the following nice map:
Nice isn’t? Justin explained how the components interact to each others. Then he reviewed the security issues. For him, client side attacks will remain a critical point in Smart Grid environment. The same attack surface is available as a regular network. More defense layers are required and network segregation, restriction, access controls must be implemented. And, of course, no Internet access at all! From a server point of view, server side attacks remains also the same. Smart Grid systems are managed using web based interfaces. What about CRSF attacks? The infrastructure requires the same security level as a regular one (patching, logging, etc). Nothing new! Justin talked about weak encryption issues, hardware attacks, firmware vulnerabilities, flash images manipulations. Smart Grid is definitively a hot topic where security must be properly managed.
Finally, the very last talk! About “Monoculture – the other side” presented by the same Cisco guy who answered question during the NX-OS talk: Damir Rajnovic. I had no precise idea about the content of the talk but curious, I attended. Damir started by a generic definition of monoculture: It is the exploitation of a single crop, usually considered as bad. They he explained how this principle also apply to information security. When you use a single product or brand (all coming from the same vendor), you amplify adverse effects of an attack. That’s why it is recommended to deploy products from different vendors. But it is effective? Sometimes, the monoculture is forced by vendors who apply discounts. More you buy from them, more discount you receive. Then, Damir explained the principle of NVP (“N-Version Programming“) and how it affect information security. By analysis the vendor pairs (they appear together more often than others), it came to the conclustion that most commercial products have many dependencies. In fact, they are based on the same “software blocks” like (Apache, OpenSSH, SSH, etc). But the presentation slided to a distinguished commercial one (IMHO!). Damir explained that vendors (like Cisco – what a coincidence!) may patch or changes some software blocks by their own to be less vulnerable. The conclusion of this talk could be: “Use only Cisco devices but with different versions of IOS”. Sad!
I’m now back to home and finished my post. I liked the talks regarding defensive security like Roboo and visualization. More defensive topics should be covered (IMHO). Great event as usual, lot of fun and met lot of new contacts! See you again as soon as possible guys!
Message to the BlackHat organizers: If you read this post, please schedule the next edition back to April, the weather will be better! 😉
One comment