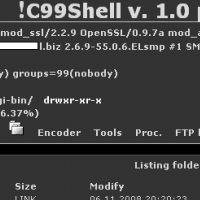
I published the following diary on isc.sans.org: “Webshell looking for interesting files“: Yesterday, I found on Pastebin a bunch of samples of a webshell that integrates an interesting feature: It provides a console mode that you can use to execute commands on the victim host. The look and feel of the