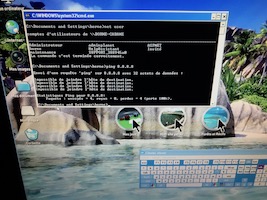
I published the following diary on isc.sans.org: “Microsoft Office VBA Macro Obfuscation via Metadata“: Often, malicious macros make use of the same functions to infect the victim’s computer. If a macro contains these strings, it can be flagged as malicious or, at least, considered as suspicious. Some examples of suspicious functions