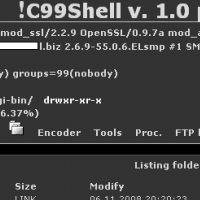
I published the following diary on isc.sans.org: “Obfuscating without XOR“. Malicious files are generated and spread over the wild Internet daily (read: “hourly”). The goal of the attackers is to use files that are: not know by signature-based solutions not easy to read for the human eye That’s why many