Today started the 2014 edition of Hack in Paris, a French security conference held in Disneyland Resort Paris – a very nice place for such kind of event! The conference started with a sunny sky over the conference centre in the New York hotel. I arrived just in time to register and to grab some coffee. Here is my wrap-up for the first day. Happy reading!
Today started the 2014 edition of Hack in Paris, a French security conference held in Disneyland Resort Paris – a very nice place for such kind of event! The conference started with a sunny sky over the conference centre in the New York hotel. I arrived just in time to register and to grab some coffee. Here is my wrap-up for the first day. Happy reading!
The opening keynote was presented by Winn Schwartau, a regular speaker at HIP! This time, he spoke about “Beyond Information Warfare: Hack Early, Hack Hardâ€. The main message delivered by Winn was: “We are still defending against the past. To defend, you have to know how to attackâ€.
As explained by Winn, he grew up “analog†(read: with no bits nor bytes). At the beginning, he had to build everything by his own. In the nineties, the message broadcasted by authorities was: “No, we don’t have to worry about hacker!â€. The government was there to protect us. Some predictions from 1991:
- Malwares
- Chipping (installing a mod chip into a game console)
- DDoS
- The initial idea
- Test/lab
- Commercial
- Consumerize
- Adapt malware
- Hostile
- Weapons
The first regular speaker was Paul Coggins with a presentation called “Digital Energy – BPTâ€. If Winn explained in his keynote that we must look further and take care of new technologies, Paul explained how critical infrastructures are still owned today using old fashioned attacks. For me, the keynote and this talk went in opposite directions.
The fact that critical infrastructure are easily compromised today is called “BPT†or “Basic Persistent Threat†(at the opposite of APT). Most critical infrastructures suffer of very basic security issues: Internet access is available at multiple levels, default passwords are used, vendors need remote access, … It’s not uncommon to see a dual-home Windows box used between a corporate and a SCADA environment. Paul reviewed some (nightmare) stories where infrastructure were compromised using simple attacks like:
- Public SSH servers pwned via a brute-force attack
- Misconfiguration of an IPTV provider which mixed data & TV traffic
- Directory traversal on a billing server
- Misconfgurations
- 6K DSL routers compromised with a rogue DNS server
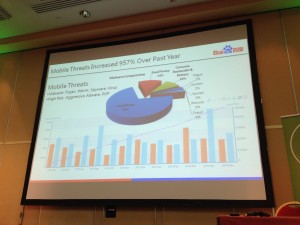
After a first coffee break, Thomas Lei Wang, from Baidu – the Chinse search engine, presented “Breaking Through the Bottleneck: A look at mobile malware spreadâ€. The talk started with an impressive number: Mobile threats increased by 957% over past year! The top goal of malware developers is to steal money (71%). Our mobile devices have money and privacy. It can be very harmful if compromised.
The goal of the presentation was to describe how malwares spread? Thomas reviewed 12 (!) ways:
- via an official app store (ex: Google Play). By example, DropDialer.A evades Google controls and download a new package once installed.
- via a 3rd-party app stores (ex: softandrtoid.ru)
- via a text message (ex: Worm!Samsapo.A send SMS with a link to a malicious package)
- via femtocell (ex: FakeCMCC.A)
- via QR code (ex: JiFake.A)
- via Bluetooth (ex: Obad.A)
- via 3rd-party ROMs (ex: Oldboot)
- via Social networks (Opfake.B) Facebook / Twitter
- via Mobile Ad Network (BadNews.A)
- via IM (Priyanka)
- via drive by download (compromised website) NotCompatible.A)
- via USB (Droidpack.A@Windows -> FakeBank.A@Android
To summaryze the talk: malwares spread via different techniques across regions/countries. The main infection vector remains the 3rd party app sotres and forums, femtocell increases rapidly and USB is the most dangerous way! If you want to have a look at some malicious code for mobile phones, Thomas has an online archive containing all the malware samples mentioned in his talk:Â hxxp://pan.baidu.com/s/1c06E7T2 (password: HIP2014Thomas). This talk was very interesting!
 Then Joseph Pi Rodriguez & Pedro Guillen Nuhez presented “Fuzzing, reversing & mathsâ€. The talk title was not clear because they focused their research on backup solutions and more precisely the communications between clients and servers. Why backup solutions? Because it’s a critical component of IT infrastructure, all companies have one and they are sold as a security product (they are trusted). A first remark: vendors of backup solutions do not focus on security!
Joseph & Pedro found a lot of 0-day vulnerabilities and contacts with vendors were not very successful. The explained in details how they reverse engineered different solutions and found interesting vulnerabilities. The “victims†were:
- Retrospect
- Novosoft Handy Backup
Krzysztof Kotowicz, working for Google, presented his research about JavaScript crypto:  “Bitting into the forbidden fruit, lessons from trusting Javascript cryptoâ€. It started with a question towards the audience: Who think that doing crypto is JS is a good/bad idea? A lot of people already discussed about this topic but Krzystof performed his own research. Usually, Javascript crypto considered harmful:
- It’s not needed
- It’s dangerous
- It’s hard
- JavaScript crypto is doomed to fail
Some examples of applications using JavaScript crypto? We have crypto.cat, mailvelope.com or openpgpjs.org. The talk was a complete demonstration that the language has many weaknesses which impact crypto operations. The process was:
- To look at the code
- To find vulnerabilities
- To understand the root cause
- To compare to native crypto
JavaScript has many weaknesses like this one:
Math.min() > Math.max()
Developers don’t use types and this could cause problems with crypto. Cryptocat was given as an example. Krzysztof explained how a user  “__proto__†could break the chat! JavaScript has also silent errors and out of bound array access to not throw an error! The next issue is the context within JavaScript code is execute: in the browser! It runs in a JS engine with different API’s, different restrictions/policies (Same Origin Policy, iframe sandbox, etc). Browser have a nice attack surface (network stack, HTML parser, JS engine). For JS crypto, the browser is the OS and the browser security = host security. With a difference: the application delivery: we don’t install websites like apps. For Krzysztof, the best way to reduce the attack surface is to run JavaScript crypto code as a browser extension! This was a very good talk, very didactic!
After the afternoon coffee break, John Butterworth came to talk about UEFI (“Unified Extensible Firmware Interfaceâ€). His talk title was “Defeating UEFI/Win8 secure bootâ€. Old PC’s use a BIOS to initialize the system and boot the OS. This BIOS is very old and lack of security controls but modern platforms implement controls to protect the firmware.
UEFI BIOS is the successor of the classic PC BIOS. It implements a feature called “secure bootâ€. The security is better but it cannot prevent the inimitable malicious write to the boot loader. John explained deeply how secure boot can be abused. Starting with Windows 8, Microsoft provides an API to interact with secure boot. Here are some attack scenario’s explained by John:
- Attack 1: Modify the secure boot policy
- Attack 2 : Delete setup variable
- Attack 3: Modify the StdDefaults
The talk was very very technical and slide presented very quickly, very difficult to follow.
Finally, Thomas Roth presented “ARM Arch64 – writing exploits for the next ARM architectureâ€. Thomas is one of those guys who have a very strong knowledge of their topic. He reviewed the new ARM 64bits architecture and how to write exploit for this kind of CPU. I was lost 😉
And, this is it for the first day, stay tuned for the second day!