I’m using Tor for so long that I can’t remember! The main reasons to use it are to access some websites while preserving my anonymity (after all that’s the main purpose of Tor) but also to access dangerous resources like command & control servers or sites delivering malicious content. The last reason is to perform scans and assessments of web services. This is often mandatory when the tested server adds your IP address to a temporary block list. I know how it can be annoying because I’m performing the same for my web servers… But, even when you use Tor, your current IP address (the one of the Tor exit node) can be blocked as well. So you have to “renew” it (a bit like DHCP – rough comparison).
I have a Tor proxy running in my lab and accessible from any host/application connected in the same VLAN. Today, most tools have an option to use a (SOCKS) proxy.
BurpSuite is my favorite tool to test web applications and it can be configured to perform all requests through Tor. This will prevent me to become blocked by the web application until… the Tor exit node becomes blocked too! I faced this situation recently. To bypass this issue, you could try to renew the Tor circuit at regular intervals to use another exit node but a new circuit does not always provide you a new IP address! For optimation reasons, Tor will select the best path for you following some parameters (I never really checked the magic behind that). But, at least, your IP address should change from time to time.
To renew the Tor circuit, you can restart or send a SIGHUP signal to the process. A less aggressive way is to configure the control port (by default listening to port 9051). If you do this, don’t forget to configure a password to restrict access:
$ tor --hash-password MySuperStrongPW 16:FA53BE7AAFA42E726068794B0408F6BACCC3165413B940071BF3E78494
Save this password in the /etc/tor/torrc file:
ControlPort 9051 HashedControlPassword 16:FA53BE7AAFA42E726068794B0408F6BACCC3165413B940071BF3E78494
Now, you can renew your circuit. Automate this in a cronjob:
*/3 * * * * printf 'authenticate "MySuperTrongPW"\r\nsignal newnym\r\n' | nc 127.0.0.1 9051
To improve the IP address renewal, I changed my lab setup and use a small project found on GitHub: TorIpChanger. This tool will allow you to get a new IP address without problems. You can run it in a Docker container:
# git clone https://github.com/DusanMadar/TorIpChanger.git
# cd TorIpChanger
# docker-compose up -d
Note: Don’t forget to change the default password in the docker-compose.yml.
TorIpChanger starts a small daemon listening to port TCP/8080. You can renew your Tor IP address with this command:
$ curl http://localhost:8080/changeip/
{"error":"","newIp":"185.220.101.144"}
The returned JSON could be a bit strange but “error”:”” means that everything is fine. I tested it in a loop with a sleep of 30″:
$ while true; do curl http://localhost:8080/changeip/; sleep 60; done
{"error":"","newIp":"185.100.87.129"}
{"error":"","newIp":"107.189.12.240"}
{"error":"","newIp":"5.199.143.202"}
{"error":"","newIp":"107.189.7.175"}
{"error":"","newIp":"101.100.146.147"}
{"error":"","newIp":"141.95.18.225"}
{"error":"","newIp":"217.79.178.53"}
{"error":"","newIp":"103.28.52.93"}
{"error":"","newIp":"198.144.121.43"}
{"error":"","newIp":"92.35.70.172"}
{"error":"","newIp":"185.220.101.52"}
{"error":"","newIp":"185.31.175.213"}
{"error":"","newIp":"185.220.101.145"}
{"error":"","newIp":"185.220.102.240"}
{"error":"","newIp":"192.42.116.17"}
{"error":"","newIp":"185.220.101.187"}
{"error":"","newIp":"185.220.101.167"}
{"error":"","newIp":"185.220.102.251"}
{"error":"","newIp":"176.10.104.240"}
{"error":"","newIp":"185.220.102.241"}
{"error":"","newIp":"5.255.97.170"}
{"error":"","newIp":"23.236.146.162"}
{"error":"","newIp":"51.15.235.211"}
{"error":"","newIp":"107.189.14.76"}
{"error":"","newIp":"18.27.197.252"}
{"error":"","newIp":"128.31.0.13"}
{"error":"","newIp":"109.70.100.19"}
And, like above, you can automate it via a cronjob.
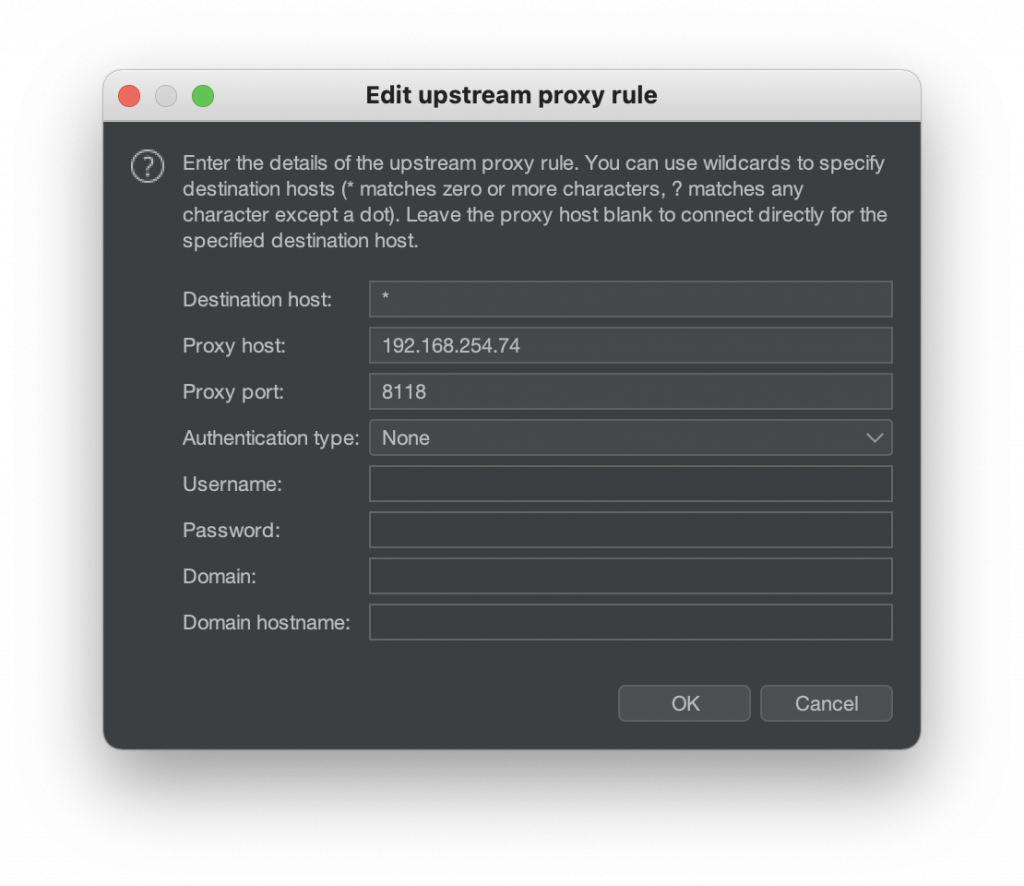
To use Tor, the approach is different. A TorProxy is now used and listens for requests on TCP/8118. You can reconfigure this proxy in BurpSuite:
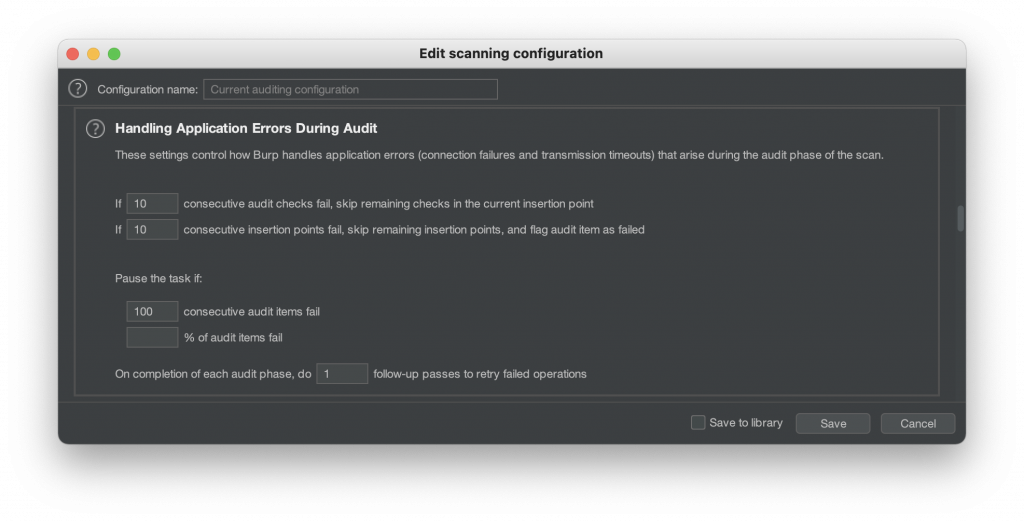
To prevent active scanning from failing too often (if the current IP address is already blocked before the renewal), I optimized the following values. This gave me pretty good results and did not break any scan:
A final note about this technique: if the webserver you are testing implements sessions based on extra parameters like your IP address, it will of course fail or have side effects. Besides some timeouts (when the IP is renewed), I did not expect any issues, except the fact that Tor remains sometimes very slow. But that’s another story!