After the MISP Summit on Monday, hack.lu, here is a quick review of the third event I’m attending in my crazy week in Luxembourg: BSides Luxembourg! It was already the 3rd edition (and the 2nd for me). The message is clear: this event focus on the “blue team” side, don’t expect offensive content like 0-days. I did not attend all the talks because there were two tracks and I spent some time to discuss with friends.
The first talk I attended was “Threat Hunting Linux & Mac using Elastic Auditbeat” by Aaron Jewitt. The talk covered the end-points problem when they run Linux or macOS. I twitted a few days ago that network monitoring is key to detect suspicious activity on a network but the main issue today for defenders is encryption. Most of the traffic is encrypted, DoH will be more and more popular. We need different solutions. A connection to Amazon over 443 has no context. Solution: end-point visibility. Windows has Sysmon and Event logs but what about UNIX flavored OS’s? Auditbeat to the rescue! Lightweight shipper to audit activities of users and processes. 3 modules: auditd (receive events from the Linux audit framework). The file integrity module generates events when files/folders are changed. Events content file metadata and hashes. The system module collects info about a system from 6 different datasets. It’s like a Sysmon for Linux & Mac. Datasets are available: Host, Login, Package, Process (the most useful for threat hunting), User. How to use Auditbear? The configuration is made via a YAML file. Configure the modules to be used, each module has specific config, set logging output. threat hunting is a never-ending process. You assume that you’ve been breached but you don’t know how/where/when. What about macOS? Apple is shy and doesn’t let you see what’s happening. objective-see.com/. Example of hunting on Mac: Persistence: Kernel extensions (KExts) Watch for ‘kextload’ process execution. Look ar /var/at/tabs/. “defaults” is a command to change the default: defaults read also : /private/etc is like /etc on Linux. bashrc, man.conf. Monitor Sudo activity. Monitor for strange parent/child processed (like Windows). And Linux? processes with /dev/tcp/*, php with fscockopen, The good old “|bash” 🙂 Conclusions: endpoint visibility can empower defenders. Keep an eye on Linux/macOS. This is really adding value to the network monitoring.
Just after this presentation, I switched to the other track to follow “Security Trade-offs in ElasticSearch” by Philipp Krenn. He explained some security facts about ElasticSearch.
“How to Shield an IoT product from the OWASP IoT Top-10” by Pablo Endres. After a brief recap about IoT, he switched to the dark side: the security of IoT devices. Huge topic! IoT is, by design, pretty complex: you have a mix of hardware, software, firmware, communication protocols, gateways (sometimes), network, data collection, and applications. Everybody remembers the joke: The “S” in IoT stands for “Security”. After reviewing different aspects of the (in)security of IoT devices, Pablo reviewed the OWASP IoT project and the top-10 vulnerabilities.
The next talk was really interesting because I’m also working on the same kind of project: “Automated Attack Surface Detection and Information Gathering” by Thorsten Ries. He described his project: automatically scan and enrich IP addresses used by his organization. Indeed, when you’ve many public IP addresses, it’s important to keep an eye on services they expose (by mistake or because a new vulnerability has been released for a specific application – example the famous RDP vulnerability). The idea is the following:
Scan > Enrich >Report > Mitigate
Thorsten explained how he performs these tasks, which components are interconnected (Shodan, Spiderfoot, etc). Interesting.
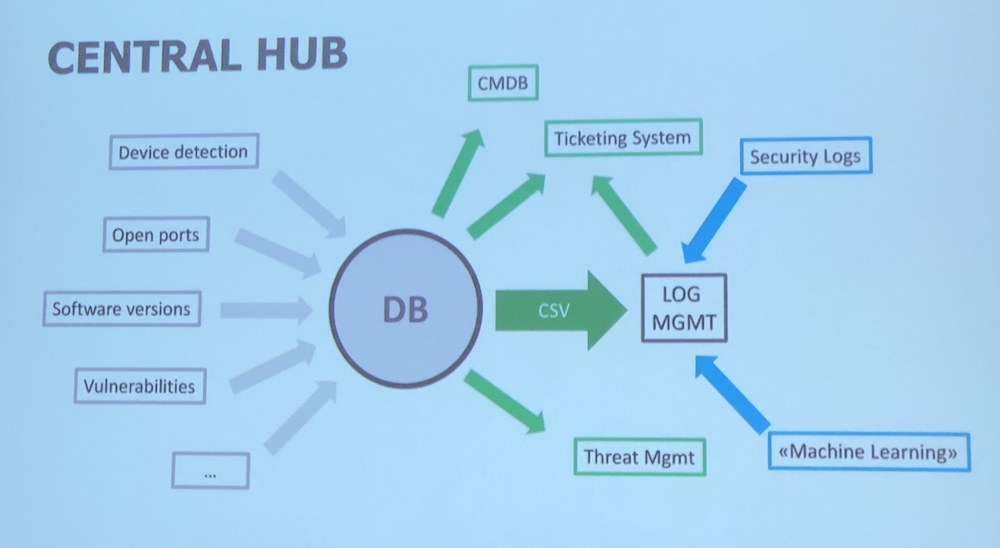
After the lunch break, it was my turn and I presented “A Walk Through Logs Hell“. This was a brand new talk that covered a series of mistakes that you could face with your log management solution. I had some pertinent questions during the Q&A.
Then, James Nemetz reviewed the Equifax breach with “(Identify)|Protect|Detect|Respond – A Deep Dive into a High Visibility 2017 Breach“. I like this kind of review because you learn many mistakes and realize that the same could apply in your own environments. To resume, it was a complete fail.
After the afternoon coffee break, Daan Raman presented the framework developed by NVISO, a Belgian security consultancy company. The framework is performing. statistical outlier detection. The idea is too not to detect activity using common signatures (this can be performed by many other tools) but to detect a known-bad event that are difficult to detect via the same rules. This is based on the generation of statistics model (that must be automated). ee-outliers, an open-source framework developed to detect statistical outliers in events stored in an Elasticsearch. The framework is available here.
Last but not least, Peter Czanik presented “What you most likely did not know about Sudo…”. The last time, I met Peter, I was also a speaker at the same time. Finally, I was able to attend his talk about the magic command and I was not disappointed! I’m using Sudo for 15+ years and I still learned new stuff. What is Sudo? This picture resumes everything:
For many people, Sudo configuration remains simple and looks like this:
%wheel ALL=(ALL) ALL
You can read this as who, where, as which user, which command can be executed but there are many other features that can be activated. First example: digest verification. If the binary allowed to a user is modified, Sudo will prevent the execution. Second example: session recording. You can record a Sudo session than play it back later. Small security issues: sessions are recorded locally and can be easily destroyed. In fact, the latest release of Sudo has a modular plugin architecture and features can be added (as shared libraries or directly in the code). An interesting plugin is an approval system that allows another admin to review the command that will be executed via Sudo and to allow/reject it. You can see this as a “dual-control system”. The plugin is called sudo_pair. Then Peter explained how to integrate Sudo with Syslog-NG for better logging and reporting. Finally, I explained what’s in the pipe for future release. Great job!
That’s over! My week in Luxembourg is completed, driving back to Belgium. See you soon for other wrap-up’s!
