And here is my third and last wrap-up for the 2019 edition of hack.lu!
The last day is always harder for many people after the social event but I was on time to follow the first talk: “Beyond Windows Forensics with Built-in Microsoft Tooling” by Thomas Fischer. Thomas’s goal was to give some “ideas” to people who attended the talk to implement new things when back at work.

Shadow IT is a problem because when you’ve to investigate an incident on a device that you don’t own, you don’t have all the tools like on a corporate computer. How to quickly investigate without messing up everything? Most of the time, they are running Windows. Good news, Powershell is available everywhere since Windows 7. It supports regexes, uses objects for data. You can instruct Powershell to fetch a script via HTTP and execute it in memory (thanks to “IEX”). You can access files, registry, event logs. There is also a lot of scripts available online. We have the foundations. Then Thomas presented “SRUM” or “System Resource Usage Monitor”. It’s a Windows component available since Windows 8 that collects processes and network-related metrics over time (since the machine boot!). Application History (from the task manager) is also a good source of data. All started processes (even if removed from the system) are logged. The rest of the talk was a suite of demos based on Powershell scripts used to pull data from the SRUM database. I think that SRUM + scripts deserve to be presented in a workshop format to give people a chance to try it. Thomas’s scripts are available here.
Then, we switched to the APT world with “Effectiveness in simplicity: The Taskmasters APT” presented by Elmar Nabigaev. The APT group discovered is called “TaskMasters” and uses very simple TTP’s! Discovered in 2010, they focus on espionage and have a big toolbox. What about their victims? Military contractors, governments, telecom but also small businesses. Their kill chain is: Initial vector unknown (probably phishing emails) > Escalation (EternalBlue, Stolen creds) > Lateral movement (scanning, tunneling, scheduled tasks, RDP) > Exfiltration. Elmar reviewed the malware behind the attack: Remshell. What about the toolbox that used? It is based on public tools (Microsoft SysInternals, scanners, webshells, WinRAR) as well as private tools (fcopy, 404-Webshell, EthernalBlueExploiter). Some tools were reviewed but also some mistakes the attackers made More details about this research is available here.
After the morning coffee break, we switched to the wonderful world of containers with “Who contains the containers” presented by Ioana Andrada and Emilien Le Jamtel. Seeing the big success around container technologies, this is a hot topic. First, how easy it is to compromize containers? The presentation focused on Dockers. Many containers are deployed in the wild, often without real security concerns. About images: what’s the source? Can we trust it? Is it securely build? Does it leak interesting secrets? Is it up to date? What privileges are required? (Here is an interesting link about container hardening). Many Docker daemons expose their API port in the wild (TCP/2375-2376). Use TLS and enable debugging log level for API calls. Kubernetes (the orchestration tool) must also be properly secured. Kubernetes uses “objects”: pod, service, volume, namespace. It also has many API’s you should not expose:

During the next part, by Emilien, was about attacks against containers. CVE-2019-5736 is the most-known (it affects “runc”) but also CVE-2018-8115 (Docker for Windows). Why would you expose Docker API’s on the Internet!?
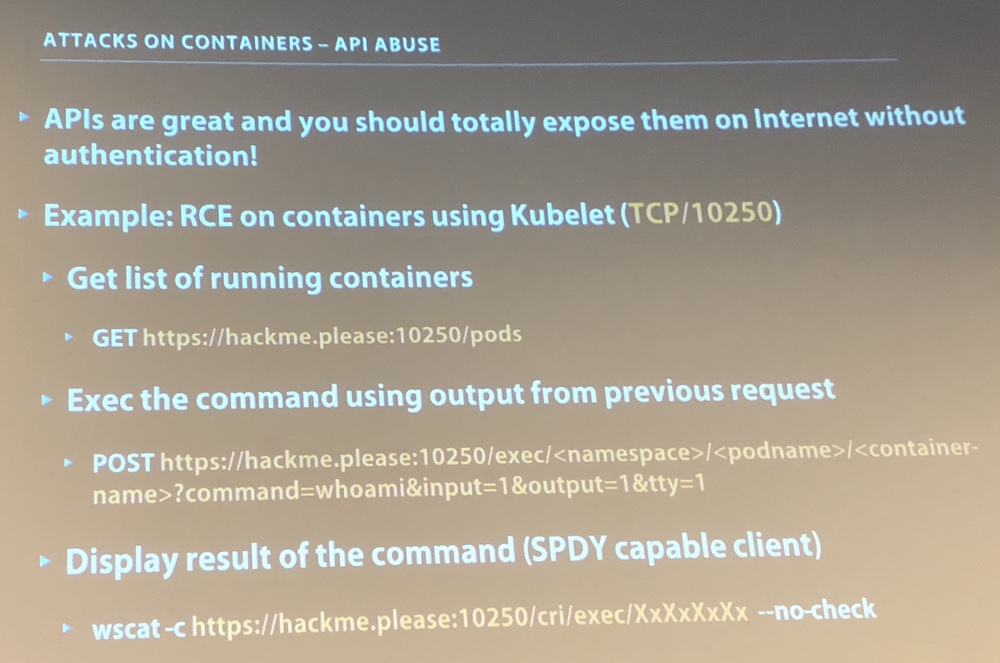
Emilien explained how easy it is to find publicly accessible Docker instances and how you can start a container from the API with a mounted folder from the host. Docker runs as root by default. Just start a Ubuntu image, mount /etc as /tmp and “cat /tmp/shadow”, booooom! Finally, some interesting cases based on scanning for exposed infra. xmrig miners are the most common usage made of compromize containers. If you play with Docker containers, here is an interesting tool mentioned: dive. It was my preferred talk for today!
I skipped the next talk: “spispy: opensource SPI flash emulation” by Trammel Hudson.
After the lunch break, the afternoon started with “Piercing the Veil: Server Side Request Forgery attacks on Internal Networks” by Alissa Herrera. It was about a successful attack using SSF (“Server Side Request Forgery”). To resume; it’s an attack to maliciously make a server perform a request/lookup. This can lead to Intranet attacks. It’s not a new attack, it has been described for the first time in Phrack! Alissa reviewed different ways to exploit this vulnerability and also some of her findings while having a look at .mil servers.
Next one, “Defeating Bluetooth Low Energy 5 PRNG for fun and jamming” by Damien Cauquil. Damien gave this talk at BruCON a few weeks ago but I was able to follow him.

Damien explained in detail what’s new in version 5.0 of BTLE? Security mechanisms are pairing, secure connections, and channel selection algorithm. The known attacks (for BTLE <4.2) are: Sniffing, jamming or hijacking. What introduced BTLE 5? Better throughput, better range, and improved coexistence. The new channel selection algorithm is PRNG-based and more “random” than the previous one. In the next part of his presentation, Damien explained that the PRNG is “not really a PRNG”. It was designed to improve coexistence, not security. With BTLE 5, Damien updated his testing framework btlejack.
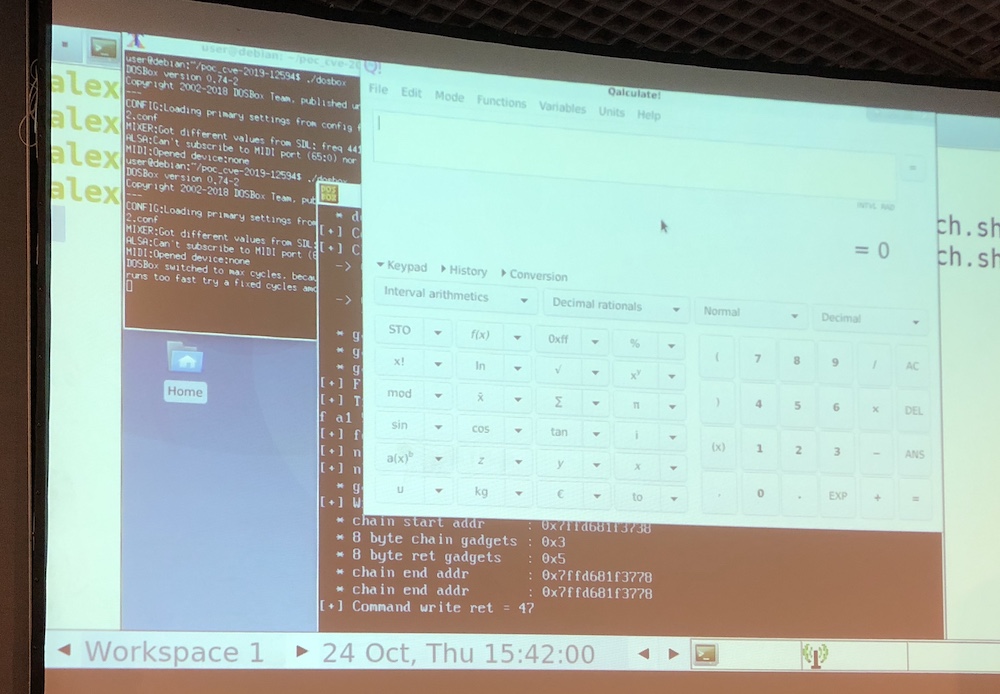
We needed a good refill of caffeine before the last set of talks. First, “DOS Software Security: Is there Anyone Left to Patch a 25-year old Vulnerability?” by Alexandre Bartel. When I read “DOS” in the abstract, I though “denial of service” but Alexandre spoke about the “Disk Operating System”, yes you read it properly the good old operating system. DOS does not mean “Dead Operating System”. It started in 1966 with DOS/360, then Atari DOS and many other different flavors like MS-DOS, FreeDOS (in 1998). But it is still alive! Example: McLaren used it on laptops to interconnect with the F1 cars (a bespoke CA card). Today, you can still use it via DOSBox, a DOS emulator. Alexandre started to fuzz DOS to find vulnerabilities and found an interesting buffer overflow. It’s crazy to see how game development companies still rely on DOSBox and games use the same engine (Ex: Shadow Warrior). The next idea was: what if we could access the local filesystem of the host running DOSBox. Better, what if we could access the memory and exploit the host? Challenge completed, Alexandre demonstrated a DOSBox that spawns a calculator on the underlying Linux host!
Last but not least, “DNS On Fire” was presented by Paul Rascagneres & Warren Mercer. After a brief recap of how DNS is working, they explained what a DNS redirect attack is (with many examples). This research started while analyzing a malware sample. Communication with the C2 was performed through HTTP requests or… DNS!

DNSpionage uses interesting techniques to communicate over DNS. A DNS request to the C2 returns a fake IP address that, decoded, gives the command to be executed (ok, the number of commands is limited). Then, the command results are exfiltration via more DNS requests (by groups of four chars!). In the next part, they presented Sea Turtle. DNS hijacking is really a pain and is used for a long time. Key take away: monitor your DNS records for any suspicious change and also the Certificate Transparency project for any SSL certificate generated for your domain(s).
That was my last wrap-up, the 2019 edition is already over. Tomorrow, let’s follow BSides Luxembourg (I’ll also speak there).
