After a short night playing the CTF and a lot of morning coffee, I was ready for the second day…
It started with a hot-topic: “Sensor & Logic Attack Surface of Driverless Vehicles” presented by Zoz. Even if not yet common on our roads today, self-driving cars (or cars with many driving helps) exist. The first self-driving car was developed in 1986 in Germany! (a car with embedded cameras). In Europe, they are many projects ongoing from the UK with Nissan, Volvo in Sweden or BMW in Germany. There is also an EU project called AUTOPILOT. The real revolution is coming in many fields: transportation, mapping services, a lot of civil applications. The idea is to prevent humans to make mistakes but… many failures may occur. What’s the logic behind these cars? We have the following architecture: Controls > collision avoidance > navigation & localization > planners/reasoners.

Vehicles are equipped with many sensors: GPS, LIDAR, Cameras, wave radars, IMU, compass, doppler, pressure, … Sensors are a source of uncertainty like noise, drift, latency. What kind of attacks can be performed against those sensors: DoS, spoofing. Instantaneously or based on aggregated data. In the rest of his presentation, Zoz reviewed, for each sensor, what are their weaknesses and how to abuse them.
Saad Kadhi presented “Disturbance: on the Sorry State of Cybersecurity and Potential Cures“. In the beginning, there was a first security tool: an anti-virus. It was born in 1970! It protected us (to some extent) but today, AV’s are not strong enough to protect us against the new threats like worms, trojans, ransomware and today fileless malware. But also unwanted applications like Mimikatz (PUA).

Saad referenced a paper about the “Microsoft Monoculture”. Monoculture can be seen as bad but it has advantages. The security of Microsoft products really improved in time. However, monoculture implies standards and class breaks. If targets are widely deployed, we increase the surface attack. Many security tools were impacted by vulnerabilities and the same applies for supply chain attacks. What if the same HVAC system was used by many organizations (remember the Target story). TeamViewer is a good example reported by Christopher Glyer (APT41). The security product zoo keeps growing but those products also introduce issues. And all those products run on top of vulnerable processors. All the products need people to be installed, used and maintained. But the human brain is not a computer (too much stuff to learn, distraction, burnouts) How to break the failure cycle? The idea of the talk was very nice but, I’m playing the Devil’s advocate here, in many (big) organizations, there is no alternative to buying expensive solutions from security vendors…
After a short but welcome coffee break, Mathieu Tarral presented “Leveraging KVM as a debugging platform“. Last year, Matthieu already presented his research about using hypervisors to perform malicious code analysis (r2vmi). This year, he came back with new stuff: VM introspection on KVM. An interesting approach again that deserves to be checked if you are playing with sandboxes and malware analysis.
The next talk was “The Red Square – Mapping the connections inside Russia’s APTI ecosystem” presented by Ari Eitan and Itay Cohen. I like the approach of the talk: search for connections between Russian malware samples. The research started by reading a lot of material. Then the following steps were implemented: gathering the samples, classification, find code similarities and analyze the found connections. The challenge of the classification was, as usual, the lack of naming convention. To help them in this process, they developed a tool called APT Detector (based on YARA rules).
The next talk was flagged as TLP:Amber, no review. “Fileless Malware Infection and Linux Process Injection in Linux OS” by Hendrik Adrian. Great content and thank you for the awesome content that you post regularly!
After the lunch, Andreia Gaita presented “Exploiting bug report systems in the game industry”. The target was not companies editing games but companies making middleware tools used by the gaming industry. Indeed like CMS or frameworks, why reinvent the wheel? Many games are based on the same engine. They are many but some are really popular like Unity. They are used by popular game editors, used by millions of people that make them very nice targets. A game engine can be seen as a layered approach, we have: Platform > Game Engine runtime > Script layer >Game.

Making a game is like the cinema industry. Programming is not the most important but scenarios, productions are. A key concept is “hot reloadable code”. The code is recompiled on the fly while the game is running (Andreeia made some demos). She explained how easy it is to attack, sometimes just be submitting a bug report. Once submitted, it is reviewed and escalated to the engine developers and guess what? The development environment is not very safe (ex: many recommendations are made to disable the AV!)
Then, the next presentation was “What the log?! So many events, so little time…” by Miriam Wiesner from the Microsoft Defender ATP. In a typical attack, we have huge times between the attack and the detection. More than 200 days to be detected (depending on the industry). While 24-48h to pivot internally. And many simply don’t know that they’ve been breached. But we are safe! We have a firewall and an antivirus!”. Users remain the weakest link. Microsoft Security Compliance Toolkit 1.0 (). Event logs have so many events… Huge document at Microsoft >700 pages. Event List 1.0 is an Excel sheet to import baselines and choose a baseline to generate an event list for this baseline
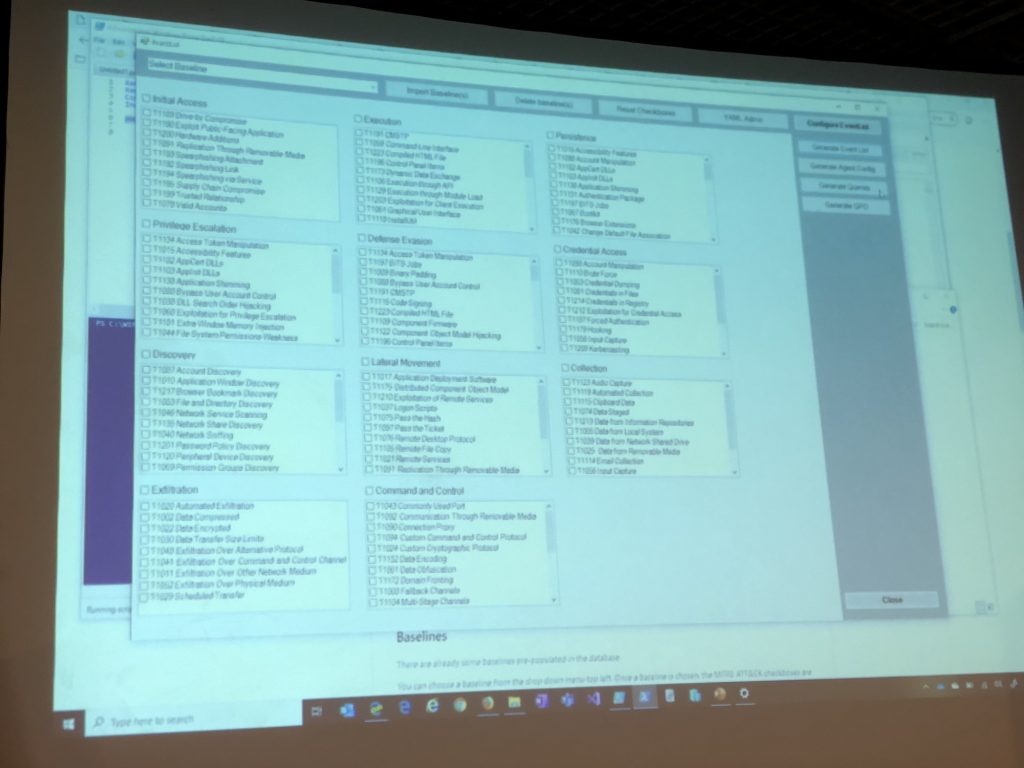
Event List is also compatible with the Mitre ATT&CK framework. You can generate GPO’s or rules for Splunk. Guess what? Event List is working with Sigma too! This one one of my preferred talk today!
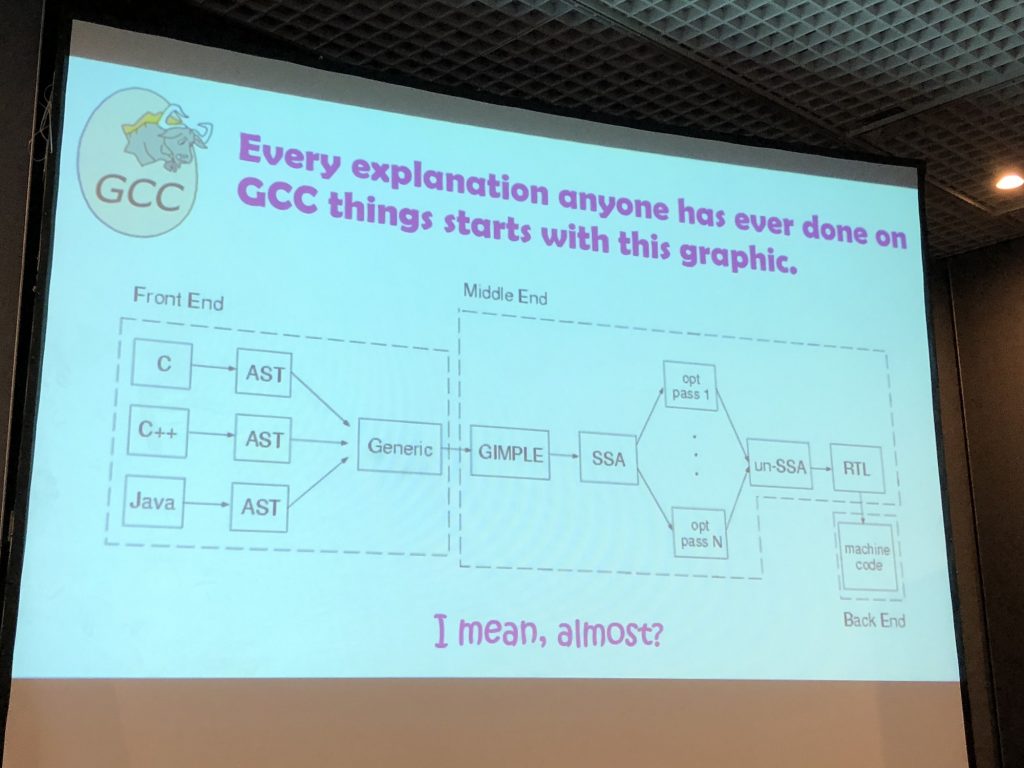
Marion Marshalek presented “The Glitch In The Matrix“. Marion works at Intel STORM and was presenting for the 5th time at hack.lu. As usual, her slides were very deep and technical but well designed. To resume, we always say that if an attacker has physical access to your computer, you might consider it as lost. Marion explained that the same is true for compilers. If an attacker has access to your compiler (GCC in this case), you can’t trust the generated code
After the afternoon coffee break, “Hacktivism as a defense technique in a cyberwar. #FRD Lessons for Ukraine” was presented by Kostiantyn Korsun, from Ukraine. This country is known to have been/be under constant waves of cyber-attacks: The election in 2014, BlackEnergy in 2015, NotPetya in 2017, etc.. Attacks are successful because vulnerabilities are present everywhere. That’s why the concept of “FRD” was introduced or “F*ck Responsible Disclosure”. It’s a mix of responsible and full-disclosure. Public information are disclosed but without working exploit. The motivation behind this is the overall improvement of the country’s security. But is it legal?

They are many positive points thanks to FRD: more visibility, increase in budget. And it’s supported by Ukrainian Law Enforcement services. So, it’s fun, legal, brings positive things and is always ongoing. But it’s important to keep in mind the difference between “open” access to data and “hacking”. This topic was indeed covered during the Q&A session! For some attendees, the limit was not very clear.
And we continued with “DeTT&CT: Mapping your Blue Team to MITRE ATT&CK” by Ruben Bouman () & Marcus Bakker. They explained the issues they faced and how they improved their hunting capabilities. Where to start hunting? They follow this path: Data Source > Visibility > Detection > TTP’s. The next part of the presentation covered the framework they developed (DeTTECT) to administrate, score and compare data sources quality, visibility detection and behaviors.
The last slot for today was assigned to Takahiro Haruyama who presented “Defeating APT10 Compiler-level Obfuscations“. Compilers have multiple optimization and obfuscation techniques that are a pain for malware analyst. One of the technique is called “Opaque predicates” and was covered by Takahiro. It was way too deep for me!
The day finished with some fun: the classic lightning talks (5 mins / speaker) and a brand new idea: “Call for Failure”. The goal is to give 10 mins to a speaker to let him tell a failure or nightmare story he faced (we all have stories like this). It was a big success with 5 submissions and a lot of laughs!
Slides will be published soon and I’d like to mention Cooper who’s doing an amazing job to record talks, post-process and publish them on Youtube in almost real-time!
