Last Tuesday, I launched a small challenge to win a ticket for the BruCON conference. The challenge was solved in approximatively 20:30 and I received the first correct submission of the hash at 23:30 (congratulations to Quentin Kaiser!). It’s time to give you the solution to this small challenge. It was web-based and did not require specific tools. Only being creative!
The challenge started with a simple URL: http://bot.sushicon.org/. If you visit this URL, you will get a simple message:
Nice try but nothing here... Looking for a PHP page?
Any URI redirects to the same page. There is a robots.txt file that should also give you a hint: we need to find a PHP page:
User-agent: * Disallow: /*.php$
From there, they are multiple techniques to find the expected entry page: The FQDN name could also be a hint “bot”.sushicon.org. But most of the players found the page just be bruteforce the website. The page was easy to find, only 3 characters: “/bot.php”. Just browse to this page:
Unknown command: "TW96aWxsYS81LjA=". Need some help?
Your bot is execting a command but which one? The strings reported by the bot should look familiar to you: It’s a Base64-encoded string (“=”). Let’s decode it:
$ echo TW96aWxsYS81LjA= | base64 -D Mozilla/5.0
This is the command received by the bot. But you did not submit any command yet. Where this command is coming from? What does your browser send to a server at each HTTP request? A User-Agent of course! It seems that your bot is expecting commands passed via the User-Agent:
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.100 Safari/537.36
Let’s confirm this by sending another user-agent:
$ curl -A $(echo test|base64) http://bot.sushicon.org/bot.php
Unknown command: "ZEdWemRBbz0=". Need some help?
We see indeed a new Based64-encoded string. Ok, but now, which commands are accepted by your bot? There is a hint: “Need some help?”. Let’s submit “help” in Base64 (it’s not case sensitive):
$ curl -A $(echo -n help|base64) http://bot.sushicon.org/bot.php Please submit a command: PING, ECHO, TOKEN, KEY, HELP
“PING” and “ECHO” are just there for the fun. Let’s issue the other commands:
$ curl -A $(echo -n token|base64) http://bot.sushicon.org/bot.php dkBCcXh7awJWUwdRAgYDDwtRUVFWV1JXVQJXCgwEAQcEBQMAAlYMBAYABwMAAwVXVl9QAVJUVlwFUVYCBwAHUVQBUgoCV1U= $ curl -A $(echo -n key|base64) http://bot.sushicon.org/bot.php 427275434f4e30783042
The token looks Base64 encoded (again), let’s decode it. What could you try with a token and a key? Let’s try to XOR them. You can use any tool to achieve this but Cyberchef is very good at performing such tasks:
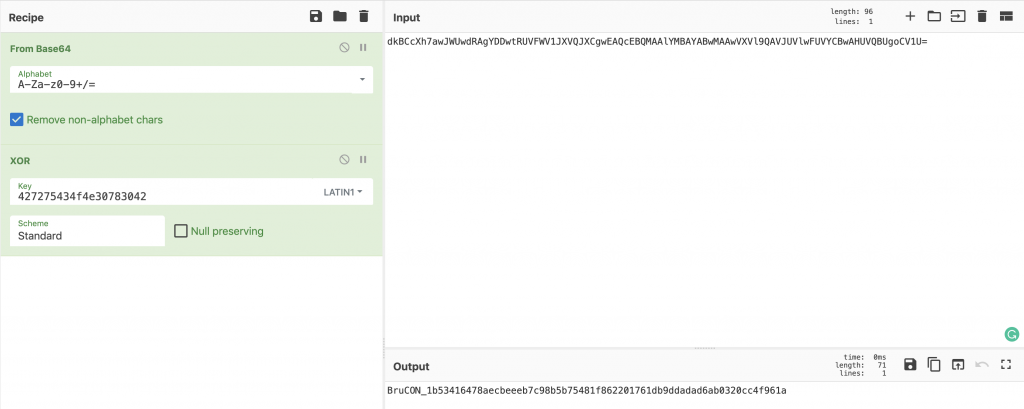
What about the players now? Two people solved the challenge (well, they contacted me and provided to correct answer), the second a few minutes after the winner! Here are some stats about the server:

218 unique IP addresses connected to the challenge:
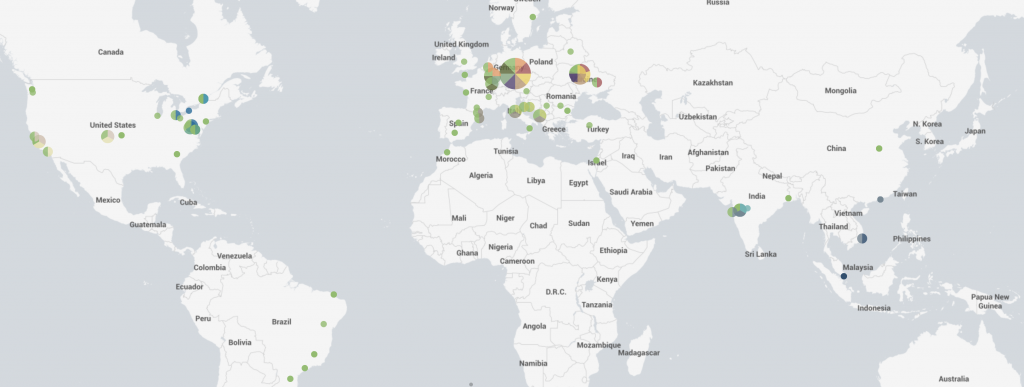
I think that many people tried to use automated tools (scanner) to try to solve the challenge. Amongst 1.560.017 HTTP requests, only 3091 requests were performed against /bot.php! (only 0,19%!)
We are sold out. I think that we are still looking for some volunteers to help us during the conference. Otherwise, register a training and you get access to the conference. Maybe have a look at sponsors and try to get one 🙂 Good luck!
I’m looking for a ticket for BruCON conference on Friday 11 October.
Please mail me if you have one ben.verhasselt[at]protonmail.com
tx