Today, while hunting, I found a malicious HTML page in my spam trap. The page was a fake JP Morgan Chase bank. Nothing fancy. When I found such material, I usually search for “POST” HTTP requests to collect URLs and visit the websites that receive the victim’s data. As usual, the website was not properly protected and all files were readable. This one looked interesting:
The first question was: are those data relevant. Probably not… Why?
Today, many attackers protect their malicious website via an .htaccess file to restrict access to their victims only. In this case, the Chase bank being based in the US, we could expect that most of the visitors’ IP addresses to be geolocalized there but it was not the case this time. I downloaded the data file that contained 503 records. Indeed, most of them contained empty or irrelevant information. So I decided to have a look at the IP addresses. Who’s visiting the phishing site? Let’s generate some statistics!
$ grep ^ip: data.txt |cut -d ' ' -f 2 | sort -u >victims.csv $ wc -l victims.csv 150
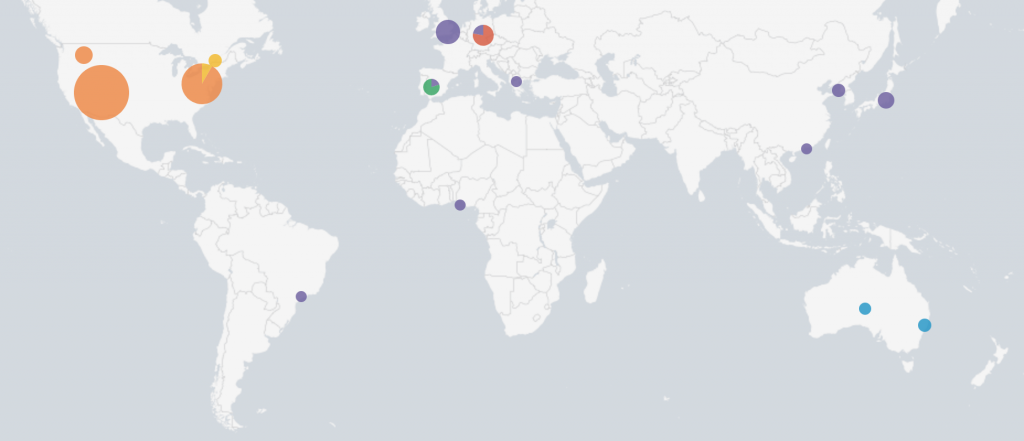
With Splunk, we can easily display them on a fancy map:
| inputlookup victims.csv | iplocation IP \ | inputlookup victims.csv | iplocation IP \ | stats count by IP, lat, lon, City, Country, Region
Here is the top-5 of countries which visited the phishing page or, more precisely, which submitted a POST request:
| United States | 64 |
| United Kingdom | 13 |
| France | 11 |
| Germany | 7 |
| Australia | 5 |
Some IP addresses visited multiple times the website:
| 37.187.173.11 | 187 |
| 51.15.46.11 | 77 |
| 219.117.238.170 | 21 |
| 87.249.110.180 | 9 |
| 95.85.8.153 | 6 |
A reverse lookup on the IP addresses revealed some interesting information:
- The Google App Engine was the top visitor
- Many VPS providers visited the page, probably owned by researchers (OVH, Amazon EC2)
- Service protecting against phishing sites visited the page (ex: phishtank.com, phishmongers.com, isitphishing.org)
- Many Tor exit-nodes
- Some online URL scanners (urlscan.io)
- Some CERTS (CIRCL)
Two nice names were found:
- Trendmicro
- Trustwave
No real victim left his/her data on the fake website. Some records contained data but fake ones (although probably entered manually). All the traffic was generated by crawlers, bot and security tools…

2 comments