 Here is a quick wrap-up from Heidelberg (Germany) where was organized the 9th edition of the TROOPERS conference. Unfortunately, due to an agenda conflict (my bad!), I was not able to attend the first day and just joined the conference this morning for the second day of talks. Here is a quick wrap-up of the talks that I watched. Notice also the awesome badge that was given to all the attendees and customized with their own name. It was also providing nice challenges!
Here is a quick wrap-up from Heidelberg (Germany) where was organized the 9th edition of the TROOPERS conference. Unfortunately, due to an agenda conflict (my bad!), I was not able to attend the first day and just joined the conference this morning for the second day of talks. Here is a quick wrap-up of the talks that I watched. Notice also the awesome badge that was given to all the attendees and customized with their own name. It was also providing nice challenges!
Today’s Keynote was presented by
Rodrigo Rubira Branco: “
A praise for hackers“. The topic was about hackers, how they are working and what makes them different that regular infosec professionals. IMHO, this keynote should be presented to journalists that still don’t understand what a hacker is! Rodrigo added many quotes in his slides that were interesting:
As the area of our knowledge grows, so too does the perimeter of our ignorance (Neil deGrasse Tyson)
No hacker is normal, they only differ in the extend of their madness
Never memorise something you can lookup in a book (A. Einstein)
If exploitation is an art, we have poetic license
We should hack because it is cool and we have fun
He explained how to handler information that we can grab here and there. Information or just data that receive in bulk (unprocessed). We have to do our own analysis and criticism. The classic example are vulnerabilities: do not report them blindly to upper levels. Take time to investigate if they are relevant depending on your environment. The issue is also to prioritize (due to the huge amount of data). Then, trust! Trust is given, not deserved. That’s why social engineering works. Hackers have also great ideas and develop tools. Think about projects like GrSecurity. They are still years ahead! Keep in mind:
- Complexity is bad
- Assumptions are dangerous
- Composition of systems != the security of each each element of that system
- What is proven is not necessarily correct of the pre-requirements and simplification of the computing model are not correct as well
 Then my first choice (amongst three slots in parallel) was the presentation of
Chris Truncer about “Passive Intelligence Gathering and Analytics”. For Chris, passive intelligence is just collecting meta-data. He started by explaining what is threat intelligence. The goal is to answer the following questions: Who? What and how? What do we know about the attack? Â Was is sophisticated? The first step is of course to collect logs! Then to parse them to extract useful information. What should you get depends on your business or organization. He reviewed some commercial tools / feeds that they have problem: they are expensive and they may be non relevant to your business because made by others. Is the investment worth the price? The solution is to switch to open source threat intelligence. But, if it’s cheaper, the information is as good as the source we have!

The next part of the tool was a presentation and demo of the tool developed by Chris: Just-Metadata. When he wrote the tool, the requirements were:
- Fast and easy to setup
- Minimum configuration
- Minimal dependencies
- Automate as much as possible
The goal of the tool is to load a set of IP addresses then, they will be queried against different modules to collect intelligence. Modules are: VirusTotal, Shodan, Whois databases, Geolocalization, etc… Then queries can be performed to generate stats. The tool is available here. Have a look at it if you have to deal with incidents involving many IP addresses!
Then,
Raphael Vinot and
Marion Marshalek presented “The Kings in your Castle”. After a quick review of what an “
APT” is (I like their definition: “
A fancy name for shit you can have in your network“), they explained how to use IOC’s (“
Indicators of Compromise“) to classify malware families and campaigns. But to perform this in an efficient way, you need a good tool. There is one:
MISP (“
Malware Information Sharing Platform“) developed by CIRCL (the Luxembourg CERT).
One of the MISP features is to be able to correlate events. They reviewed some correlation and interesting facts they found in the huge database of samples managed in the CIRCL MISP instance.
After the lunch break, I switched to the track dedicated to embedded devices / IoT. The afternoon started with
Dr Kevin Fu who presented “
Medical Devices Security: Hack or Hype?“.
Security (as well as the huge number of issues related to it) is not new in the medical sector. It started already in 2006. Many different types of devices were targeted by attackers: pacemakers, defibrillators, pumps, x-ray computers, … Kevin did not came with new facts, we already know that security on such devices is often close to zero. But he gave very nice example or “nightmare stories” from the medical field:
- Device pwned just by telneting to them (direct root access)
- A dental x-ray computer delivering beer ads
- An hospital took down due to a ransomware (recent story!)
- An hospital took down by a malicious Angry Birds game
- An hospital which switched from SSH to Telnet for “compliance” (because the vulnerability scanner was reporting too many false positives)
- Etc…
At the end of the talk, he presented a nice device developed by his university which tries to detect malicious activities on medical devices via their power consumption! Usually, nothing can be installed on such devices and his solution is non-intrusive. More details are available here.
Then, again on the same topic (IoT), Attila Marosi presented “How easy to grow robust botnets with low hanging fruits“. I was a bit disappointed by the content of the presentation. Based on the abstract, I expected to learn how a botnet was deployed and managed across different types of connected devices.
But the talk was a compilation of scans and findings (D-Link routers, Polycom video-conference systems, Haier router, …)
My last talk was about a Russian attack.
Wayne Huang and Sun Huang presented their research about the “
Northern Gold Campaign“. Some facts about it:
- It is operated by Russian speaking people
- They compromize WordPress websites (they purchased lists of admins of shared hosting providers on the black market)
- They deployed Qbot on 500K systems
- Collected traffic (from banking websites)
They explained step by step the attack chain:
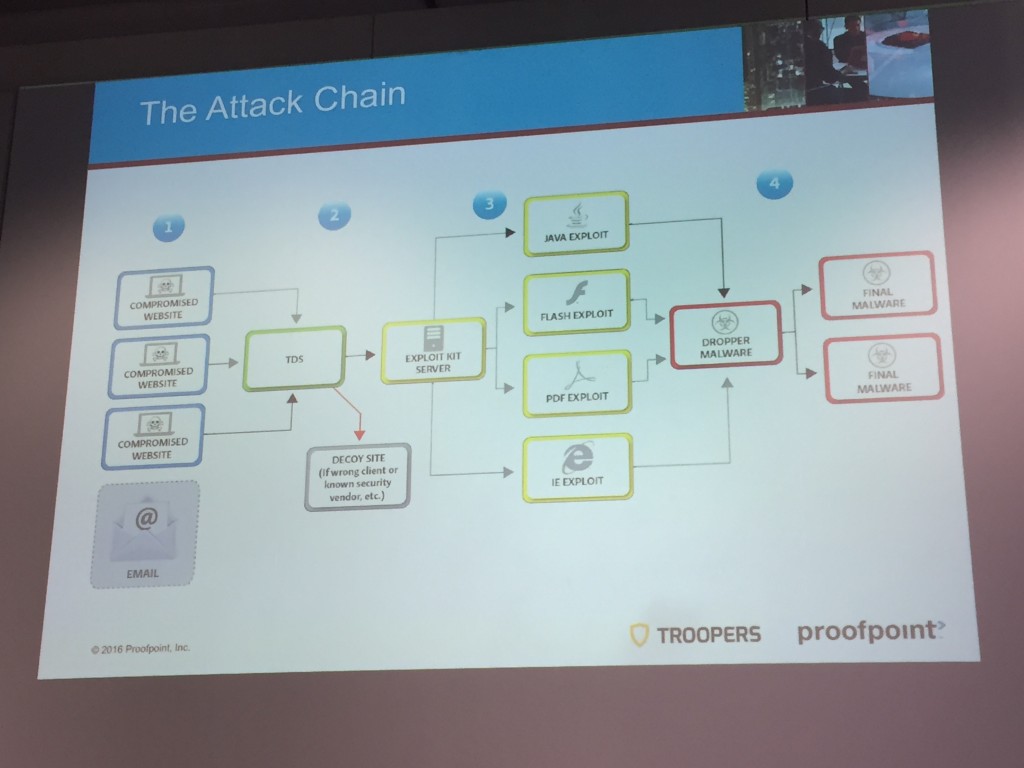
What are the different components to infect people, the TDS (“Traffic Distribution System”) and its protection, the exploit kits and C2 communications. They had access to the source code of tools used by the bad guys and were able to demonstrate the features and controls in place. It was a very interesting talk!
That’s all for today! A great organization, nice venue, native IPv6 wireless access, dedicated GSM network, lot of charity actions (auctions, hackers run, etc) and a very nice atmosphere. See you next year at the same place I hope (for the 10th edition!)
 Here is a quick wrap-up from Heidelberg (Germany) where was organized the 9th edition of the TROOPERS conference. Unfortunately, due to an agenda conflict (my bad!), I was not able to attend the first day and just joined the conference this morning for the second day of talks. Here is a quick wrap-up of the talks that I watched. Notice also the awesome badge that was given to all the attendees and customized with their own name. It was also providing nice challenges!
Here is a quick wrap-up from Heidelberg (Germany) where was organized the 9th edition of the TROOPERS conference. Unfortunately, due to an agenda conflict (my bad!), I was not able to attend the first day and just joined the conference this morning for the second day of talks. Here is a quick wrap-up of the talks that I watched. Notice also the awesome badge that was given to all the attendees and customized with their own name. It was also providing nice challenges!




2 comments