 Here we go for a new edition of the Botconf edition. Already the third one. This conference is moving every year across France and, after Nantes and Nancy, the organizers chose Paris and more precisely the Google France venue! Really a nice one, typically in the Google atmosphere. I commuted from Belgium early and arrived in time to grab some coffee and attend the opening session by Eric Freyssinet, the chairman of the Botconf organization. To resume, the conference, here are a few numbers:
Here we go for a new edition of the Botconf edition. Already the third one. This conference is moving every year across France and, after Nantes and Nancy, the organizers chose Paris and more precisely the Google France venue! Really a nice one, typically in the Google atmosphere. I commuted from Belgium early and arrived in time to grab some coffee and attend the opening session by Eric Freyssinet, the chairman of the Botconf organization. To resume, the conference, here are a few numbers:
- Total budget: 80.000€
- 260 attendees
- 3 keynotes
- 20 talks
- 6 short talks
- A bunch of lightning talks
- 1 social event
A mention to the nice idea that should be followed by all security events: they had a social media policy in place this year. One comment about some talks: some speakers asked to not be recorded, others asked to not disclose information disclosed during the talk. Why not implement the TLP protocol before each presentation? Just wondering…
The first keynote slot was assigned to Margarita Louca from Europol: “Successful botnets takedowns: The good-cooperation partâ€. More precisely, it’s the EC3 (“European Cyber Crime Center“). This talk was flagged as “restricted” and not all information will be reported here. Europol is a mandatory actor in “takedown†operations (to bring botnets infrastructure and owners out of service). After a resume of the EC3 organisation and missions, she reviewed some successful takedown operations. But, as she explained, there are a lot of issues (technical, administrative): court orders can’t be changed to reflect changes in botnets, lack of resources. Margarita give as example the takedown of Shylock which was considered as a bad operation. Some parts of the infrastructure can be difficult to shutdown. The example given by Margarita was about the .su domains. The challenges that authorities are facing:
- Bild trust amongst participants
- Report
- Inform the public (media)
- Share(!)
- Minimise profitability
Some local laws can be issues. By example, in the Netherlands, IP addresses are considered as personal data! A nice introduction to start the day.
Then, the normal schedule started with “Ponmocup, the full story: A giant hiding in the shadows†by Maarten van Dantzig and Jonathan Klijnsma. Ponmocup is not brand new (it was already covered in previous editions of Botconf) but it is still alive (since 2006!).
It is attributed to multiple organisations, possibly  Russian speaking people. It infected a very high number of victims and is a multi)purpose framework. It also uses undocumented Windows API calls. In a first phase, Maarten & Jonathan explained how victimes are infected. The malware implements very nice tricks to defeat security researchers like specific referrers, cookies, IP blacklists, etc. They also implement clever techniques to prevent the direct download of the malware. Also, if you try to often, you’ll be blacklisted. Amongst the anti-analyzis features, the malware checks for processes, usernames, drivers, monitor size, recently opened documents, browsers history, installed apps, etc. Good job! During the installation phase, the malware reset system restore points and disable the system restore feature. It also open firewalls and disable UAC. A unique artefact is created per infected host based on the volume serial number! Each copy is unique to the target. The most amazing feature of Ponmocup: it’s really framework with multiple (25) modules known: AV killers, SOCKS proxy, SIP scanners, FTP stealers, system info gathering, Facebook cookie stealer, Bitcoin wallet grabber, etc. Another feature to prevent sinkholing: not all domains are deployed at once but grouped by versions of the payload. The takedown will only effect a part of the botnet. The speakers reviewed many feature of the malware, they work was really impressive. To summarize, Ponmocup:
- Is active for 7 years
- Infected 15M+ victims
- 500K are still active
More details were released by Fox-IT: the report and IOC’s.
To prevent sinkholing, not all domains are deployed at once but grouped by versions payloads… The takedown will only affect a part of the botnet. Great job!
The next talk was a short one and presented by two people: Alexander Chailykto and Aliaksandr Trafimchuk. The title was “DGA clustering and analysis: mastering modern, evolving threatsâ€. DGA (or “Domain Generation Algorithmâ€) is a key element in modern malware. This technique was first used by Conficker.
Problems with DGA are:
- Impossible to block
- Only a small amount will be really used by the malware
- Sinkholing not effective
They developed a tool called DGALAB. It supports the following DGA Types:
- Static DGA – generate the same domains overtime (just reimplement the algorithm)
- Date-based DGA – current date is used as input
- Seed-based DGA – seed as input (hardcoded but not easy to extract)
- Combination of the last two
The features of DGALAB are:
- Modular system (new type of DGA will be supported)
- Generate full list of domains
- Combines sillier DGAs automatically into one group
- Effective whitelisting system
- Resource saving emulation
The tool is based on Cuckoo sandbox and Cuckoomon, running with VMware as hypervisor with some fixes in the virtual environment and a specific kernel. They finished the talk by a presentation. This tool could be very useful is integrated into an existing solution like a firewall, IDS, etc.
After the lunch, another short talk was presented by Zoltan Balazs: “Sandbox detection for the masses: leak, abuse, testâ€. Zoltan started with some questions to the audience. It’s a fact: everybody has the same issues… malwares detect our sandboxes and we need more hardened sandboxes.
It is easy for a malware developer to detect sandbox… Zoltan did a quick demo with VirtualBox… Common issues are:
- The screen resolution:
- Installed software (python, Tracer, PHP, Debugging tools, Strawberry Perl,
- Running common processed (python.exe)
- The CPU type… Who run’s an Intel Pentium Pro ? Also the number of cores
- Computer system (Bochs, VirtualBox, KVM, Optiklex 990, P5QSE, etc
- Mouse: move movement
- Memory size, a desktop with 1GB of memory? 🙂
- Machine name
Also, usually, the user desktop is a mess! It’s also possible to watch for  CPU usage, network connections. The lessons learned: they are many ways to bypass dynamic analysis. A message for the sandbox solutions developers: try harder! It was a short talk but it deserved to be a regular one, a lot of interesting information were reported by Zoltan. I liked it!
Then Lukasz Siewierski from CERT.pl was scheduled with a talk called “Polish threat landscapeâ€. Lukasz told a story of a social engineering attack against a Polish company. The same story could apply to any company in any other country!
The attack scenario was a classic one: a mail was sent, someone responded, then a second mail was sent with a pseudo NDA. Once the company pwned, the attacker stole the list of customers and sent fake invoices to them from the company. Then, the presentation switched from a technical review of this case to a more nasty one. Lukasz explained how the company reacted and sued a journalist pretending that they were never hacked and customer details never disclosed… Interesting story!
Gavin O’Gorman talked about the “Butterfly attackersâ€. Butterfly, as named by Symantec is a corporate espionage group which compromised major corporations for 3y. Here again, no recording, no disclosure of information.
Then, Veronica Valeros, from Cisco, presented “Make it count: An analysis of a brute-force botnetâ€. Her research started from a fact: we usually analyse what’s happening in the first minutes of a malware infection. What about one week, one month or at 03:00AM?
She found a sample which looked normal but a few days later, it started to have another behaviour… It downloaded new payloads and started to perform brute-force attacks! Its target were WordPress websites. Not surprising seing the huge amount of such websites available! The attack in some numbers:
- 1 bot
- Visited 7000 sites
- 1 was successfully accessed
- It took ~3.5h
- 6 sites compromized per day
Like the previous short talk, it was very interesting. Straight to the point was nice facts!
Frank Denis presented his research: “The missing piece in threat intelligenceâ€. Frank is working at OVH and has access to a very nice source of malicious activity.
ISP’s have to deal with multiple problems. They host services that are abused, compromized and it’s very difficult to manage them. The example of IP addresses is a nice one. An IP address can be reassigned to customer and the new customer will also inherit the reputation is this IP. This could have a big impact on his business. Also, some vendors have bad behaviours and just re-use data from online services. Example: some vendors block IP addresses because their virustotal.com score is > 0! Frank explained how ISP react in bad way and have lot of issues to track the issues. Then came the idea to propose a structured language to describe actions take by ISP’s after a report. As an example, IP addresses could be flagged as:
- Reserved
- Unassigned
- Suspended
- Clean
- Notified
- Deleted
- Resumed
- …
Of course, the next challenging step is to make peers use the same language. To achieve this, Frank developed a tool called ERISÂ which helps to use the DIP protocol as named by Frank. The benefit are multiple:
- Law enforcement agencies can have instant access to valuable info
- Researchers and SIEM operators can have instant feedback
- Service provides and incident handlers can save time
- Users get more visibility
A very nice idea. Now, the goal is to make others parties aware of the tool and protocol.
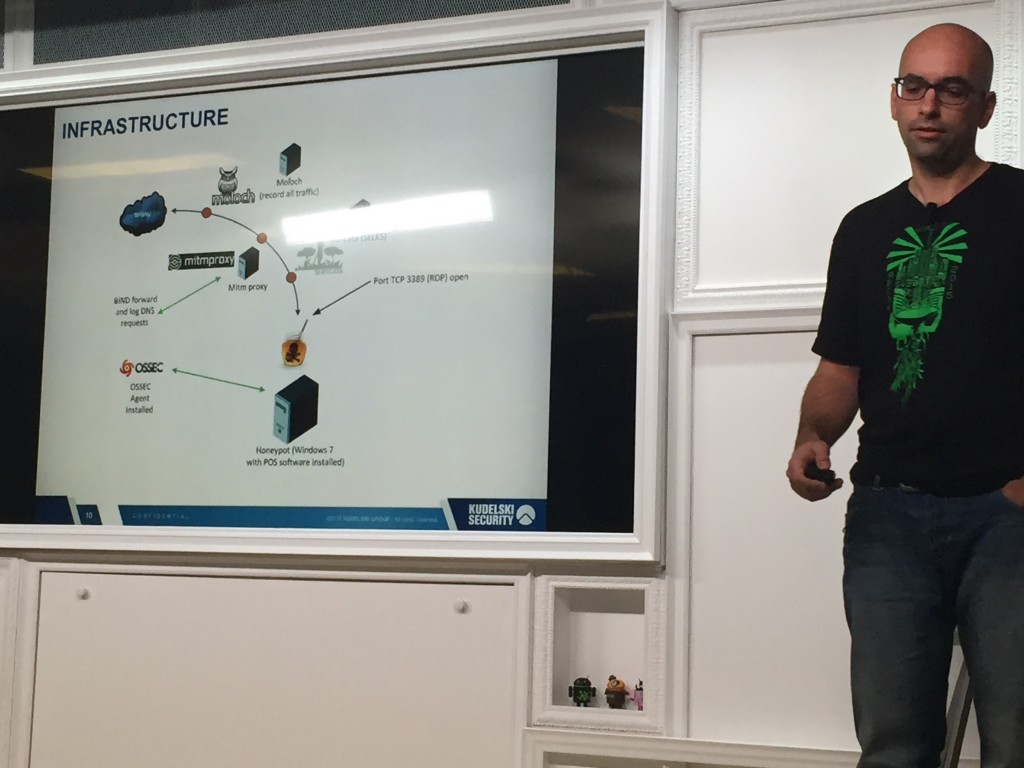
Marc Dioudet talked about “Honey!? Where is my POS?â€. The goal of his research was to understand better the techniques and procedures used to abuse POS (“Point of Sales“).
After a short review of a standard POS system and why they remains juicy targets, Marc explained the solution he deployed to build his own POS honeypot. After only three hours, he already got a hit with a good old Morto malware infection. He also explained why it was difficult to attract attackers. Initially, the server was locate in Germany where chip & pin is commonly used. Once he move the server to the US, he got more hits!
Finally, John Bambenek spoke about takedowns of botnets (again) with a presentation called “Takedowns; case studies ad what we all could be doing betterâ€. Like Margarita this morning, he explained why it is so difficult to organize the takedown of a botnet.
For John, our problem today is the following: We are on the losing end of an arm race. We are doomed. But it’s a good news for us, security professional, we will have enough job for us! What is a takedown? It is based on:
- Special actions in security
- Seizing domains
- Getting hosting company to clean up the mess
- Marketing ploy?
A fact: Why do we have to take down botnets? For John, it’s because most people can’t buy the very expensive products developed by most vendors. A takedown must be seen as a disruption because it implements new firewall rules, blacklists, DGA list examples, … Are they effective? Not always and, worse, they can have side effect! Often, actors recovers themselves within a few hours. Collateral damages are always possible. John gave the example of medical devices infected with Conficker. What about the pacemakers managed by those devices? John reviewed some nice examples of takedowns:
- No-IP (by Microsoft)
- Conficker
- Kelihos (this one had 4 different takedowns and is still alive!)
A nice talk with many useful information in a “do and don’t” style. This talk closed the first day! See you tomorrow for another wrap-up…







RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0
RT @xme: [/dev/random] #Botconf 2015 Wrap-Up Day #1 https://t.co/gRodR321a0