 Here is my wrap-up for the second day of the conference NoSuchCon organised in Paris. Where is the first wrap-up will you maybe ask? Due to an important last minute change in my planning, I just drove to Paris yesterday evening and missed the first day! This is the second edition of this French conference organised in Paris at the same place. A very nice location even if the audio/video devices are not of a top-quality. The event remains also the same: one single track with international speakers and talks oriented to “offensive” security. This year, I was invited to take part of the selection commitee.
Here is my wrap-up for the second day of the conference NoSuchCon organised in Paris. Where is the first wrap-up will you maybe ask? Due to an important last minute change in my planning, I just drove to Paris yesterday evening and missed the first day! This is the second edition of this French conference organised in Paris at the same place. A very nice location even if the audio/video devices are not of a top-quality. The event remains also the same: one single track with international speakers and talks oriented to “offensive” security. This year, I was invited to take part of the selection commitee.
The very first talk was presented by Andrea Allievi who did a wonderful job around the latest Windows operating system kernel patch protection.  The full title was “Understanding and defeating Windows 8.1 Kernel Path Protectionâ€. Andrea is the designer of the first UEFI bootkit in 2012. The first part of the presentation was a review of the most important terms around the Windows kernel protection:
- Patchguard
- Driver signing enforcement
- Deferred procedure call
- Asynchronous procedure call
The research started with the Snake campaign and the Uroburos bootkit. The bootkit can’t affect Windows 8.1. Andrea reversed the bootkit and adapted it to defeat the patch protection. Windows 8.1 has a code integrity feature implemented completely different that windows 7. Andrea’s approach was to use a kernel driver. The next step was to explain how does work the kernel patch protection and how to attack the Patchguard. Finally, Andrea presented new attack types and finished with a demo. Interesting presentation but the most important info is how to protect agains this? The exploit is very difficult to implement (it took 3 months to Andrea to achieve this) but use SecureBoot and don’t trust any code downloaded from the Internet! (sounds logical).
The second talk was presented Benjamin Delpy who is well known for his tool, Mimikatz, one of the pentester’s best friend in Windows environments! After a brief reminder/introduction to the Windows authentication methods (NTLM, Kerberos) and the associated attacks, Pass-The-Hash (NTLM) and Pass-The-Ticket (Kerberos), Benjamin explained what are “Golden Tickets“: A golden ticket is a homemade ticket, not generated by the KDC.
This means they aren’t limited by GPO’s and any data can be put into them. But the nice feature is their expiration! Once generated, the key does not change for … years! Then, Benjamin explained what is “Silver Ticket” (exactly such as a Golden Ticket, except the krbtgt key). Multiple demos were made by Benjamin. I especially liked the fact that Kerberos tickets dumped on OS X or Ubuntu (which can be part of a Windows domain) can be reused on Windows by Mimikatz! Who said that Mac computers are safe on a network? Benjamin continues to develop his tool which is more and more a must have!
After a coffee break, the next target was the Google Apps Engine. Nicolas Collignon investigated the security around this PAAS (“Platform as a Service“) & Devkit used by many developers. The supported programming languages are: Python, Java, PHP & Go. The architecture is quite common and based on a load-balancer, a reverse-proxy, an application server and backend services (DB). The first part focused on the application. Nothing really change and classic attacks remain valid. Example: Developers still manipulate raw SQL queries, control raw HTTP responses and need to implement security features. If security controls are present, they are not always enabled by default. Example: the urlfetch API does not verify SSL certificates by default. Nicolas also explained how to obtain Python RCE (“Remote Code Execution“) via a XMPP service. The next part was attacking the GAE infrastructure. This is difficult because it can’t be reproduce in a lab. The provisioning API is a nice target because developers use weak credentials (hey, what’s new here?) and also share credentials between production and development environments. A classic fail is to store the production domain key in a non-safe place! (Accessing this key is a dangerous as a compromised Windows domain admin account). The next part focused on the sandbox mechanism proposed by Google with many examples. Nicolas’s conclusions are:
- Classic web attacks still work because developers must write safe code!
- Google did a good job, Python sandbox can be evaded only at the 1st layer.
- Sensitive credentials are stored in applications (when accounts outside Google are used)
After the lunch break, Ezequiel Gutesman presented  “Blended web and database attacks on real-time, in-memory platform“. What is “in-memory” platform? Usually DBMS rely on disk to store their data but today they are solutions which store data in memory. Why? Memory is cheap today, there is an increase amount of data to process and performance is a key. Well-known solutions are Oracle, SQLserver and SAP HANA.
Ezequiel’s research focused on SAP HANA. The solution is based on many components (DB, HTTP server) and provide a nice attack surface. This is a blended architecture. Instead of an application using a DB connection with limited (or unrestricted) access, the application is the same as the database user. User privileges should be restricted at the DB level. This changes the impact of classic attacks:
- SQLi are restricted to the user privileges (better)
- XSS is more powerful (bad)
After the introduction, some attack vectors against HANA were reviewed. About SQL injections, HANA has a nice feature: history tables. If the user does not delete it, the information remains available! XSS attacks were reviewed as well as integration with the R-Server.
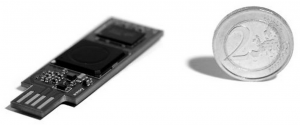
The next talk was the presentation of an awesome hardware project: the USBarmory. Andrea Barisani explained in details on the project started, how they developed the hardware and what issues they faced. The idea of this device was to provide a open-hardware running open-source software with:
- Mass storage device with automatic encryption, virus scanning, host authentication and data wipping
- OpenSSH client and agent for untrusted hosts (kiosk) router for end-to-end VPN tunneling, Tor
- A password manager with integrated web server electronic wallet
- A portable penetration testing platform low level USB security testing
The development started in January 2014 and the product should be available for sale in December.
And the last talk was the one of Richard Johnson who spoke about fuzzing application with “Fuzzing and patch analysis: SAGEly Advice“. It started with an introduction to automated test generation. The goal is to target a program with a full coverage of all possible states influenced by external input. This can be done via two approaches:
- Random Testing (or Fuzzing) with a zero-knowledge fo the target
- Concolic Testing
If fuzzing is very interesting, it has limitations because it cannot cover all possible states (a fuzzer tool is unaware of data constraints). That’s where concolic testing can help. Richard explained the concept in details with many examples. Finally, a tool was presented: Moflow::Fuzzflow and some real-life example where the tool was used to find vulnerabilities in software.
The day ended with a nice social event. Stay tuned for the last set of talks tomorrow!


“@xme: [/dev/random] #NoSuchCon Wrap-Up Day #1 http://t.co/gWt8BD4ToB†< The right version is now online!