
Everybody agrees to consider “security by obscurity” a false sense of security. By using this principle, the security of an information system in (falsely) increased by hiding sensitive details. Such information can be removed like: by altering the application welcome banner (in Apache, sendmail, etc), by changing the default port (example: binding your SSH daemon on port 2222 instead of the standard 22), by renaming critical files with invalid names or extensions.
From an offensive point if view, attacking by obscurity can be much more interesting. If you launch an attack on a specific target, there are (mis)chances that your behavior will be detected by an IDS, a firewall or any other security countermeasure. One of the solution is to work “below the radar”. It means performing the attack at a very low rate to not trigger the rules in the security system or by avoiding regular patterns in your packets. Example when using Nmap:
# nmap -sF --max-rate 0.5 --scan-delay 3 192.168.0.0/24
In this command line:
- “–scan-delay” asks Nmap to wait at least the given amount of time between each probe it sends to a given host.
- “–max-rate” limits the scan sending rate to a given maximum
Note that, by default, Nmap randomizes the ports to scan (except the well-know ports for efficiency)
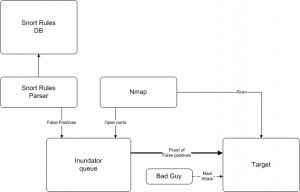
Another method is to use a solution like inundator. What’s the purpose of this tool? Quoted from the official website: “inundator is a multi-threaded, queue-driven, IDS evasion tool. Its purpose is to anonymously flood intrusion detection systems (specifically Snort) with traffic designed to trigger false positives via a SOCKS proxy in order to obfuscate a real attack.“
It could be resumed as “The security analyst’s nightmare” 😉 The principle is quite simple: Hide your real attacks amongst thousand of false-positive alerts generated by the IDS and hope that the real attack won’t be discovered.
- (Click to enlarge)
Based on the schema above, inundator reads the current Snort rules database and generate packets which will trigger the rules. A Nmap scan of the target host(s) is performed to detect interesting ports. inundator floods the target host(s) via the generated packets to the ports reported open by Nmap. In parallel, the real attack is performed. Of course, the flood of packets will be send via Tor or a bunch of open proxies to increase the number of sources.
Unfortunately, inundator is not able to detect the IDS in place and works only with the Snort signatures. If we come back to the “defensive” point of view, inundator can be used to stress test your Snort.
Source code: inundator_0.5.tar.gz
“security by obscurity†😉
http://yitingcheng.webs.com/psecretstash2010.htm
Thanks for your feedback! Indeed, a false positive is a false positive! Whatever the product… Signatures based IDS suxx! 😉
And congrats for the integration into BT!
Bitchin’ review! I really like the diagram 😀 You nailed the application flow perfectly.
You are correct in stating we cannot remotely identify the intrusion detection/prevention method used by the target system (or at all), as these are passive devices either run off a port mirror or ran transparently inline. However, you may be interested to know that several users have reported great success against IDS platforms other than Snort (see http://bailey.st/blog/2010/07/02/inundator-anonymous-ids-evasion/ for another good review against Suricata.)
Essentially Inundator will generate false positives on any IDS, IPS, webapp firewall, database firewall, etc that uses pattern matching rather than heuristics or anomaly-based detection mechanisms, as long as we can come close to matching the pattern. Sometimes the title of the false positive doesn’t match what’s in Snort’s rules files, but that’s okay — a false positive is still a false positive! Due to this fairly recent development, we have updated our website to remove the “(specifically Snort)” caveat.
Another piece of good news is Inundator is now officially part of BackTrack Linux!
Thanks again for the review,
/epixoip.