Already the last day of the conference! I could say that hack.lu was a “festival of calc.exe” this year! They popped up from everywhere 😉
We started with Ilja van Sprundel who talked about exploiting Delphi/Object Pascal. Applications written in Delphi are not often targets of attacks but interesting stuff can also be performed on them. That was the project presented by Ilja. Like all other languages, Delphi is vulnerable! Like in “C”, overflows, stack and head are a great way to make attacks. Once again, several calc.exe spawned from nowhere. How to mitigate? Compiler settings: Range-checking, overflow checking, By default, Delphi is not a ‘safe’ language. According to the speaker, they are a lot of vulnerable Delphi applications still in use.
Followed “Ownage 2.0”, presented by Saumil Shah. Saumil explained “how to own the world one desktop at a time”. The steps are: evolution, attack the eco-system, mass manufacture and 1+1+1+… Softwares are more and more complex and more bugs are introduced by developers who make mistakes. Users awareness is very important. Saumil gave a nice definition: “users are made to click”. The surface attack today is composed of Office documents, PDF, browsers (all of them) and helpers (Flash, Java, Quicktime, …) To prove this, let’s have a look at a typical user browser:
Another excellent Saumil’s quote: “calc.exe is the ‘hello world’ of bug exploitation!“. After explaining how to own the desktop, he explained the next step: how to deploy massively and own the world? Social networks are your best friend. URL shortener are also very dangerous. Several demos were performed using different techniques (note: Google is very helpful to find vulnerable sites) The conclustion of the presentation was: There has to be a new browser security model created.
The next topic was IpMorph or Unification of OS fingerprinting defeating presented by Guillaume Prigent and Florian Vichot from Diateam. They presented their work during FRHACK. The philosophy of this project could be “to live happy, live hidden”. Basically, IpMorph is able to make a Linux workstation being detected by a scanned as almost everything else). To develop the tool, Guillaume & Florian required a deep knowledge of other tools like nmap (know your enemy!). Some demos (recorded videos) where presented:
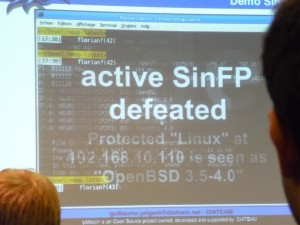
The goal of IpMorph is not to be used as a security tool. Security by obscurity is not a solution against external attacks.
Some tricks for defeating SSL in practice by Moxie Marlinspike. Like said Saumil: “users just click!”. Moxie explained the story of SSL and the major issues encountered years after years. Then, he presented his own tools: sslsniff & sslstrip. He explained how he performed a nice attack on SSL websites using a certificate containing a null-character (like “www.paypal.com\0thoughtcrime.org”). Scaring: lot of websites use locks pictures on their pages or even as favicon. By using sslstrip, it’s almost impossible for the end-users to know if he’s surfing a safe or unsafe site. By the way, yesterday, I was listening to the radio, I still eared that surfing on site with “https://” and a closed lock is safe… Moxie explained how the certificate revocation issue was disabled by defeating the OSCP protocol (“3” is the key number 😉 Finally, Moxies explained how softwares like Firefox or Thunderbird are performing their updates and how easy is it to fake them and why not force them to download false patches.
Just after the lunch, an auction was organized by syn2cat.lu. The next talk explained how to play with satellites environment (Christian Martorella). A satellite is a radio-frequency repeater. They are classified by their orbit and their functionalities (communication, GPS, …). The talk focused on DVB (Digital Video broadcast). Then Christian explained how to find DVB feeds? By using a DVB card (easily found on eBay), It’s possible to scan for feeds and attach a network interface to the feed found. Once done, wireshark can be used to sniff the traffic coming from the satellite. What are the types of attacks: DNS spoofing, TCP hijacking or attacking GRE (13% of the traffic on satellite is GRE traffic). He also showed how to make anonymous connections.
The next talk was about “Forensic and anti forensic enhancement with a HVM virtual monitor” by Adrien Derock. When I read the description of the talk, it looked interesting but the speaker gave too much theoretical slides (full of formulas) for a Friday afternoon at the end of the conference. I completely skipped this one…
Finally, the talk “When E.T. comes into Windows Mobile 6” closed the conference. Cédric Halbronn explained how the Windows Mobile operating system can be the target of attacks. This OS is a major player on the PDA market and is a nice target for hackers. The goal was to build a rootkit for WM6 with the environment constraints (embedded, mobile, services on the table). Cédric started with some technical aspects of WM6: 4GB of addressable memory (2GB for kernel space and 2GB for user space). Max 32 process with 32 MB mem/process, etc. Security policies are stored in the registry “[HKLM\Security\Policies\Pollicies]” and easily accessible. Injection of the rootkit can be done via physical access, MMS (vulnerability in WM2003) or WAP push msg. The rootkit persistence is achieved via registry, \windows\startup or create a service. Unsigned application can be hidden (no warning to the user!) via the registry or… just add your own certificate in the privileged store! 😉
Regarding the processes, you don’t need to hide yours: when a process has no window, hidden by default in the task manager. Worse, if you put the process name to NULL, it will be hidden in the process list! The installed backdoor is available via TCP/IP using one of the data network available (GPRS, 3G, Wifi or ActiveSync). Live demo using the backdoor webcontrol (web based tool): Cédric grabbed the emails from the target modile. To wake up a sleeping device, the attacker can send a sms to force the device to connect to the control center (always without intrusive message). Future possible enhancements? To take pictures, to use the microphone, tapping, ..
That’s all for this edition of hack.lu. As usual, interesting talks, I met a lot of people (some always known as others new) and had very constructive talks. See you next year I hope!