There is a black market for vulnerabilities, nothing new with this fact! A brand new 0-day can be sold for huge amounts of money. The goal of this blog post is not to cover this market of vulnerabilities but the way some of them are disclosed today. It’s just a reflexion I had when reading some news about the Rompager:
2014 is almost behind us and we faced some critical vulnerabilities in the last months! If some of them affected very critical and widely spread software components, some also were publicly released in the wild with all the classic components of a commercial marketing action.
Previously, vulnerabilities were disclosed on specific communications channels like mailing-lists (full-disclosure being one of the most known). Then, came social networks like Twitter (which remains a key player for broadcast information) but, across the last months, we saw more and more vulnerabilities disclosed with:
- A logo
- A fancy name
- A dedicated website (with a nice domain name)
Vulnerabilities are referenced via assigned IDs. The most used reference system is called “CVE” or “Common Vulnerabilities and Exposures“. Security professionals are always speaking about such identifiers. To give you an example, the Rompager vulnerability is reference as CVE-2014-9222. But some vulnerabitilies receive a name and all the marketing material associated to them. Here are some examples: Heartbleed, Poodle, Sandworm or, the latest, the Misfortune cookie.



Such vulnerabilities are critical and affect millions of devices and, thanks to the help of their marketing presence, they were also relayed by regular mass media to the general public, sometimes in a good way but sometimes with a very bad coverage. Often, behind this marketing material, there are big players in the infosec landscape who are fighting for being the first one to release the vulnerability. Examples:
- mis.fortunecok.ie has been released by CheckPoint.
- Heartbleed by Codenomicon
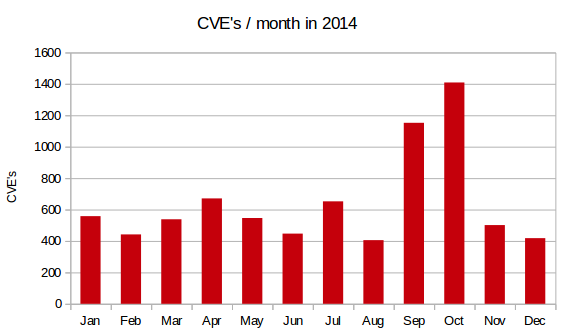
If speaking about major vulnerabilities to a broader audience is of course a good initiative, it must be performed in the right way. I’m afraid that more and more vulnerabilities will be known to the general public but keep in mind that they are the top of the iceberg. There are new vulnerabilities found every day and some of them are also very nasty! The graphic below gives you an idea of CVE numbers assigned per month in 2014 (7739 as of today!). As you can see, it’s far more than the four vulnerabilities mentionned above.
To resume: not only “general public” vulnerabilites must be addressed. All of them are important and could lead to a complete compromise of your infrastructure (remember: the weakest link). I hate marketing, also in information security! 😉
Heartbleed was found independently by Codenomicon and Google. Not only Codenomicon
RT @xme: [/dev/random] The Marketing of Vulnerabilities http://t.co/4aNUQSTpOb
RT @xme: [/dev/random] The Marketing of Vulnerabilities http://t.co/4aNUQSTpOb
RT @xme: [/dev/random] The Marketing of Vulnerabilities http://t.co/4aNUQSTpOb
RT @xme: [/dev/random] The Marketing of Vulnerabilities http://t.co/4aNUQSTpOb
RT @xme: [/dev/random] The Marketing of Vulnerabilities http://t.co/4aNUQSTpOb
RT @xme: [/dev/random] The Marketing of Vulnerabilities http://t.co/4aNUQSTpOb