I’m just back at $HOME. Let’s go for the second day wrap-up! This morning, I walked to the hotel in the sun to take a breakfast. Very nice weather over Amsterdam again today! Bruce Schneier was the second keynote speaker.
Do I still need to present him? He came to talk about  “Trust, security and society” which is the topic of his new book. Bruce has always a new book to promote! 😉

In the real life, we feel safe. We trust people all the time (the taxi driver, the server at the restaurant, the pilot who brings us to Amsterdam, etc). Society does not function without trust. How society makes this work? Trust is a really complicated concept! When you say “I trust a friend“, you speak about the person, not his actions. We can also trust actions of people in a specific context. Back to the first example with the taxi driver, we don’t know his motivations, we just trust him to drive us to our destination safely. Another example: trusting a server who gives us a bottle of water. For airlines, you don’t trust people (the pilot) but you trust the airline company which should produce skilled pilots. You don’t have to know how a system works, you just trust it (ATM machines are a good example). But if there are too many factors, the system will collapse. “Parasites” can only survive if they are not too good. Security is how we can set the level of trust to an acceptable level, otherwise it will collapse. They are different types of pressures:
- Moral : We fill bad if we do, we don’t want to (Do I steal those goods or not?)
- Reputation: What people will think of your behavior
- Institutions: They have rules and enforcement has been delegated
The problem with the two first type of pressures: They don’t scale (societies are growing) And what’s the power of reputation? Bruce gave a funny example. In a company, people can buy coffee. They have to leave some coins next to the coffee machine. Â At the end of the day, a comparison between the money and the number of coffee cups give the percentage of people who paid (or not). A study showed that only be adding a picture of eyes behind the coffee machine, the number of paying people increased.
Technology allows our society to get better in lot of different ways (more people, more complexity, more social network, distances, frequency, etc) Wait, it looks like a definition of the Internet. Internet is just a copy of the real society from a security point of view, new attack vectors are used by criminals like in real life. Attackers can make use of innovations faster cause they are not limited by boundaries. To maintain good security is to react quickly by evaluating what attackers will do next. A final problem is that society is not always right. The assumption that a group is correct is not always true!  It this topic interest you, read Bruce’s book! Bruce is really a good speaker, no slides just stories and real-life examples!
After a coffee break, Andrei Costin talked about the danger of PostScript files. Why PostScript? MFP’s (“Multi Functions Printers“) carry a lot of abuse potentials. They contain confidential documents, they remain unpatched, they are (sometimes) facing the Internet or are available on the network. Modern printers are targets since a decade! Did you know that lot of printers are facing the Internet? And generic MFP payload delivery occurs using Word or Java. Back to PostScript! PostScript is used to handle complex procession tasks. This is a programming language: Stack based and turing-complete. PostScript printer driver transforms document to PostScript streams for specific devices and data stream on PRN. Windows based systems can process PostScrtipt files  too (via an interpreter) and execute code on your PC. PostScript is like a Java sandbox. It has simple control statements (if/else, loop, while) and simplest DoS is an infinite loop:
!%
{}loop
Demo time! How to kill Word with less then 10 characters.
Another demo: “Dynamically types concatenate” aspect, by example to evade IDS:
({) (}) (l) (o) (o) (p)
count 1 sub { mergestr } repeat
cvx
exec
Next demo: Real world application: MS Office PostScript crash! What about GhostScript? Dynamic document forging/generation can be used with some Social Engineering techniques. Andrei gave an awesome example with a rogue PostScript file; If the file is opened with Ghostscript nothing happened otherwise the malicious code is executed. Example of a real attack? On a PC the invoice show an amount of 100 EUR but once printed: 1000 EUR 🙂 Who will read the document just printed? It will be signed! As said Bruce before, we trust the printer!
PostScript can also address some web2.0 issues? Some online services are also vulnerable to rogue PostScript documents. 20+ online services were found to be vulnerable at different level (Google was one of them). Some fun facts? Some GhostScript are running as root. Some runs GS without -dSAFER, some run vulnerable versions (heap and stack overflows).
What about physical devices? Installation of firmware upgrades is performed via PostScript documents. Admin restriction fails to prevent memory dumping. Even if devices are protected at interface level. API’s remain available. HTTPS/IPSEC secrets are “default” and “leaky”: they are in memory! Printers protected by a PIN code or a badge reader are also vulnerable. Document is also available in the memory!
Can you imagine performing a network scan via printers? Printers use lot of protocols to detect devices on the network. Guess where this information is stored? In memory of course, using the same techniques, you can retrieve information about the network topology without using any active scanner on the network. To perform social engineering, coupons, discount codes are great! People like free stuffs! Conclusions: Don’t print suspicious documents. Printing is bad for environment but also for your security ;-) Andrei’s papers are available online.
The next talk I attended was “How to use Taint to find vulnerabilities?” by Alex Bazhanyuk and Nikita Tarakamov. In parallel to this track, there was the one about the new IOS jailbreak. But I decided to stay in the same room to follow Nikita’s talk. Too many people went to the jailbreak session.

What is taint analysis theory? Taint sources are network, keyboard, memory, disk, function outputs. Taint propagation is a data flow technique.  Static taint analysis is performed over multiple paths of a program. More information about taint analysis can be found here. BitBlaze is a binary analysis infrastructure to automatically extract security-related properties from binary code. SASV main parts are IDA pro plugins and BitBlaze: Vine + utils, TEMU + plugins. Then I was lost, too complex for me! 😉
After the lunch break, there was two talks in parallel about mobile operating systems: “Bypassing the Android Permission Model” or the second part of the IOS jailbreak. I decided to attend the IOS one for the fun. There were rumours that the new jailbreak will be released! The talk covered the A5. There is no tethered jailbreak on A5 because there is currently no public boot level exploit for it. But they found a way to use Racoon as an injection vector. The problem was: How to copy Corona files on the file system which is read-only at boot and how to bypass ASLR? VPN settings are not validated by configd before being passed to Racoon. The dream team explained step by step how they successfully exploited the while stuff. One the payload installed, the next step was to find a way to trigger a VPN connection? They discovered that Safari can trigger this to perform certificate based authentication. Â But typing an URL in Safari is boring, they used a Webclip.

Next step, the sandbox. What’s the sandbox? Code name “Seatbelt“, based off the TrustedBSD MAC (“Mandatory Access Control“). Sandbox.kext is a registered MAC policy. How to get the patched copy of raccoon (1-modified byte) onto the device? ptrace is not working well and Apple makes it unrestricted but it can control an unsandboxed process. To resume:
- Create a non sandbox version of raccoon
- Find notified PID
- Put notifyd’s main thread on the IPC thread
- Block notified with our exploit IPC message
- Write rest of ROP stack to shm
- Launch the exploit
The team explained in details all the steps to own the IOS devices. More information available here:
- http://www.semantiscope.com/research/BHDC2011/BHDC2011-Slides.pdf
- https://guthub.com/dionthegod/XNUSandbox
So, after the talk, the official news of the day was there: the jailbreak for 5.1.1 is publicly available but greenpois0n.com was temporary down. My opinion, they brought it down during the talk to be sure to release the exploit at the right time. This announce caused a flood of Twitter messages! People were following the talk worldwide waiting for “the” announce. Congratulations to the Dream Team. Once you see the talk it seems easy but they passed days of investigations to achieve this!
The next talk was about the Amazon cloud services. It started later because the speaker, Kenneth White, was unavailable!? When he started the presentation, he first talked for a long time about health researches (viruses, diseases) and the associated processed to remediate to them. Finally, he switched to the main topic: Amazon! Everybody knows this major player in cloud technologies. What are the promises of AWS (“Amazon Cloud Services“)?
- Scaling
- They are busy with the boring part of the infrastructure
- On demand
- Pain reduction
- Zero procurement headaches
- Cost (!)
The killer feature is indeed the cost of the public cloud! You will fail if you compare VM’s to a cloud. Your SAN/NAS is not the cloud. Could you survive to a DDoS without the cloud? Finally, by using the cloud you can focus on more interesting stuffs in your job. Kenneth reviewed interesting information about AWS. Who’s behind?

What’s their grow? Some interesting numbers: They hired 22.5K new employees. They advertise 800K public IP addresses. What about their data centers infrastructure? Most information is publicly available:
- Facility built-outs, availability zones & regions
- Power capacity and redundancy
- Pictures
- Physical , process and technical controls.
About the data centers, did you know that they are build by one of the most powerful company called Digital Reality? To analyse their backbone, BGP is your best friend. But you’ll have to take time to analyze all the peers!
I expected more details about Amazon. I was a bit disappointed by the content of the presentation. The real Amazon stuff started at the middle of the talk!
Finally the last presentation was performed by Marco Balduzzi about “SatanCloud – a journey into the privacy and security risks of a cloud computing“.

The talk used Amazon (again!) EC2 – IaaS (“Infrastructure as a Service“). Marco refreshed our brain with a brief review of the cloud computing. Most of us are using the cloud everything. You use gmail.com isn’t it? Three models exist:
- SaaS: Software is provided (ex: salesforce.com)
- PaaS: Computing or solution platform (ex: Google apps)
- IaaS: Computers, Storage, firewall, networks are provided (ex: EC2)
The talk focused on IaaS where the market leader is Amazon. EC2 provides access to a virtualized server (Amazon Machine Images). AMI’s are provided by Amazon but users may provide their own images as well as third-party companies. AMI’s can be build from a live system, from an ISO or another AMI. Configuration is simple: credentials, resources (sizing), the region where start the instance and an inbound firewall. The instance will be available via a public IP like “ec2-IP-region.computer.amazonaws.com” over SSH/RDP. First important thing to keep in mind, Amazon don’t care about the AMI security! Then Marco reviewed the problem of sharing images via the Amazon catalog. What are the threats:
- Secure it against external attacks
- Malicious image providers?
- Sanitizing the image to protect the privacy of the provider
A tool has been created to automate the security analysis of images: SatanCloud. It performs a remote scan using Nmap and a local scan using Nessus for local vulnerabilities (only the critical ones for performance reasons). What were the findings?
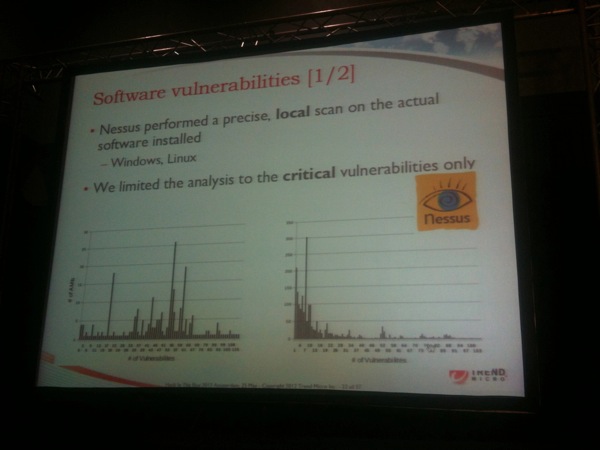
Incredible: 98% of Windows and 58% of Linux AMI’s came with critical vulnerabilities! 87 Debians AMI’s still had the notorious SSH vulnerability. Two AMI’s where infected by viruses. Some Trojans with key logger were found. Two Linux AMI’s were configured to send logs to a remote host! Some private keys can be installed on images and left behind the execution and use to make new images.

About forgotten keys? 56 private keys were found to log in to other machines. 54 of them even not protected by a pass-phrase! Linux systems have shells which generate history files. Those files were also scanned and 869 history files were found:

The next investigation was: Are deleted data really removed? AMI’s can be bundled using different methods. Block based building methods are vulnerable to file undelete attacks. 1100 Linux AMI’s were inspected using extundelete. They recovered 28GB of data! (SSH private keys, PGP keys, password files and many documents). And for Windows AMI’s? WinUndelete is your best friend! Same issue…
This research was performed with the contribution of Amazon Security Team. Vulnerable AMI’s status was changed from public to private. A tutorial was created to help customers to share their images in a secure way. Good collaboration from Amazon!
Lessons learned? Prepare your own image otherwise update the software, enable the firewall, delete (safely) unwanted data, check for outgoing connections => harden your server as if it was local (best practices). A very good talk to share with all system admins who play with Amazon EC2! My preferred one for the second day.
The closing keynote was given by Jaya Baloo from Verizon: “Identify, Privacy and Security“. Jaya’s first question was: “Isn’t it time the Internet had an identity solution?“.

We have too many passwords. This generates too much risks and, for enterprise, it’s complex and cost money. A question immediately raised from the audience: “Why complexity is bad?” Jaya think that a simple authentication mechanism could benefit to the security of users. “We need an identity ecosystem in the cloud“, Really? The challenge is a good balance between privacy and identity insurance.
A mention to an interesting online service provided by rapleaf.com: They grab data from the Internet and based on email addresses lists you have access to plenty of information (age, gender and location are free). Why collect identifies? advertising market! Privacy legislation is principally aims to protect you against government and specific organizations. But it does not address against organizations or the mistake of their employees.  Jaya made a good review of the problematic of the implementation of a unique authentication system.
Then the closing ceremony with the results of the different contests and a word from the organizers. This year, the venue changed and it was (IMHO) positive. The hotel was nice and close to restaurants, bars. I left immediately after the talks and was unable to say goodbye to old and new friends. So I do it now: It was nice to meet you once again (for some), for the first time (for others). See you soon!