 When Internet ARPAnet was invented in the seventies, its goal was to interconnect military resources using packets based networks and to be strong enough to resist to “attacks”. Loosing some devices in the network could not affect the communications. Later, the same technology was re-used to build the public network that you still use today to read to article: the Internet!
When Internet ARPAnet was invented in the seventies, its goal was to interconnect military resources using packets based networks and to be strong enough to resist to “attacks”. Loosing some devices in the network could not affect the communications. Later, the same technology was re-used to build the public network that you still use today to read to article: the Internet!
But the networks becoming more and more interconnected and complex, it was mandatory to develop protocols to dynamically route all of them. There are many routing protocols like RIP, OSPF and… BGP!
I’ll not fully explain the BGP (“Border Gateway Protocol“) protocol here, I’m definitely not a BGP expert but I played a lot with it when I worked for Internet providers. To resume in a few words: Internet will not exist without BGP! When you want to visit a web site, BGP decides through which pipes send your data. Its current version is 4 (since 2006) and it is documented in RFC4271. BGP is used to exchange groups of routes (or IP addresses prefixes) via autonomous systems (“AS“).
A report written by a commission on United States – Chinese relation has been released to the U.S. Congress a few days ago. The document reports an incident detected in April. During a few (18!) minutes, some Chinese ISP’s hijacked Internet traffic from the Internet. The consequences were lot of unreachable sites and services and (worse!) big security consequences in terms of confidentiality. But wait… Internet has though been designed to resist to attacks… Did I miss something?
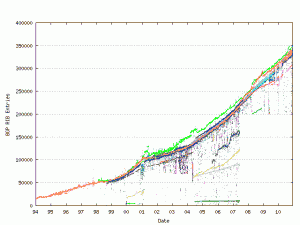
In fact, BGP is just a protocol and potentially vulnerable to attacks. Counter-measures exists but are not always used by network administrators. The purpose of BGP is to exchange messages between “peers” (routers). Very simply, messages can be of types “Please note that to reach the network 1.2.3.4, you need to pass by me!” or “How do I reach network 6.7.8.9?“. All those peers are building a unique routing table which contains the complete Internet address space. For your information, the table size is constantly growing:
Two Internet providers which decide to establish a BGP session set up a “peering agreement”. The peers are supposed to be trusted. A minimal configuration looks like:
# ISP1 router bgp 1 neighbor 10.20.30.40 remote-as 2 # ISP2 router bgp 2 neighbor 6.7.8.9 remote-as 1
But, we are not in 2006 anymore, can we trust our peers? All BGP sessions are established between peers via a TCP session (on port 179). This is a first issue: all known attacks available at the layer 4 can be used against BGP: Sessions reset, flood (DDoS), MitM, etc. But more attacks can be conducted at the upper layers: injection of malicious prefixes is a common issue. The goals can be multiple:
- Blackholing – the victim is “disconnected” from the Internet.
- Redirection – the victim’s traffic is redirected to a malicious network.
- Routing instability (or “dampening“) – BGP has mechanism to detect unstable routes and can results in network outages (like blackholing).
By default, BGP does not take care of integrity and origin of the received messages. It does not validate the routing announces made by AS nor the AS path. Except the “Chinese” issue reported a few days ago, such attacks are rare! But mis-configurations occur and have exactly the same impact. Often they have as origin small Internet providers which don’t have lot of experience (human errors). A well-known example is the one of the Pakistani ISP which hijacked Youtube in 2008!
How to avoid those problems? Well, there are interesting projects like Secure BGP (or “S-BGP“). S-BGP increase the lack of security by implementing new controls:
- The BGP components (IP prefixes, AS, routers and owners) are linked to a PKI infrastructure to authenticate them.
- Digital signatures are exchanged during BGP updates.
- IPsec is used between peers.
It looks nice but not easy to implement. Do the smallest ISP’s have time and internal resources to implement this? There are two others proposals: Secure Origin BGP (“soBGP“), based on public/private keys infrastructure, and Pretty Secure BGP (“psBGP”).
And don’t forget the core routers security. Routers are like any computer: they run an operating system, they are managed remotely by network teams and contain sensitive data. They must be properly protected. Even in a secure BGP deployment, if your router is pwned, it could be used to send bogus BGP announces to your peers!
If you’re interested in following BGP networks and issues, I recommend you the site bgpmon.net. Very useful if you maintain your own AS or if you’d like to follow the one of your Internet provider (always useful). BGP mis-configurations are a common issue today. To give you an idea, check out the bogon prefixes announced on the Internet! (bogon prefixes – like RFC1918 – must never be announced on the Internet).
Related sources:
- The BGP incident overview on bgpmon.net.
- Documentation about BGP security.
Hello Gary,
Thank you for the clarifications!
I hate to point out some incorrect data here but BGP version 4 which was written by Yakov Rekhter a fellow work mate of mine at Juniper Networks version 4 was created and identified in 1992 in RFC 1771. The current RFC you listed is the latest superseding RFC to the Original one. BGP v1 was created in 1989, v2 in 1990, V3 in 1991 and a complete rewrite and design to the TLV extensible version BGPv4 as i said earlier can out in 1992. I have used BGP since 1991 during my time at SURAnet AS1
Cheers,
Gary