I’m in Luxembourg for a full week of infosec events. It started today with the MISP summit. It was already the fifth edition and, based on the number of attendees, the tool is getting more and more popularity. The event started with a recap of what happened since the last edition. It was a pretty busy year with many improvements, add-ons. More and more people contribute to the project.
MISP is not only a tool but other parallel projects try to improve the sharing of information. There is a project to become the European sharing standard. Another evidence that the product is really used and alive: Nine CVE’s were disclosed in 2019. On the Github repository, 331 people contributed to the MISP project:

I liked the way it was organized: The schedule was based on small talks (20 minutes max) with straight to the point content: improvements, integration or specific use-cases.
The first one was a review of the MISP users’ feelings about the platform. Based on a survey, statistics were generated. Not many people replied to the survey but results look interesting. The conclusions are that MISP is used by skilled people but they consider the tool complex to use. The survey was provided to people who attended a MISP training organized in Luxembourg. It could be a good idea to collect data from more people.
There were two presentations about performance improvements. People dived into the code to find how to optimize the sharing process or to optimize the comparison of IOC’s (mainly malware samples). Other presentations covered ways to improve some features like Sightings.
New releases of MISP introduce new features. The decaying of IOC’s was introduced one month ago and looks very interesting. There was a presentation from the team about this feature but there was also another one from a CERT that implemented its own model to expire IOC’s.
MISP is a nice tool but it must be interconnected to your existing toolbox. One of the presentations covered the integration of MISP with Maltego to build powerful investigation graphs.
Integration with WHIDS (Windows Host IDS). It relies on Sysmon. It correlates events, detects and reacts (dump file, dump process or dump registry). Gene is the detection engine behind WHIDS. It can be seen as a YARA tool for Windows events. MISP support was recently added with some challenges like performance (huge number of IOC’s).
EclecticIQ presented how their platform can be used with MISP. They created a MISP extension to perform enrichment.
TICK – Threat Intelligence Contextualization Knowledgebase by the KPN SRT. The KPN guys explained how they enrich SOC incidents with some context. I liked the use of Certificate Transparency Monitoring. The goal is to use MISP as a central repository to distribute their IOC’s to 3rd parties.
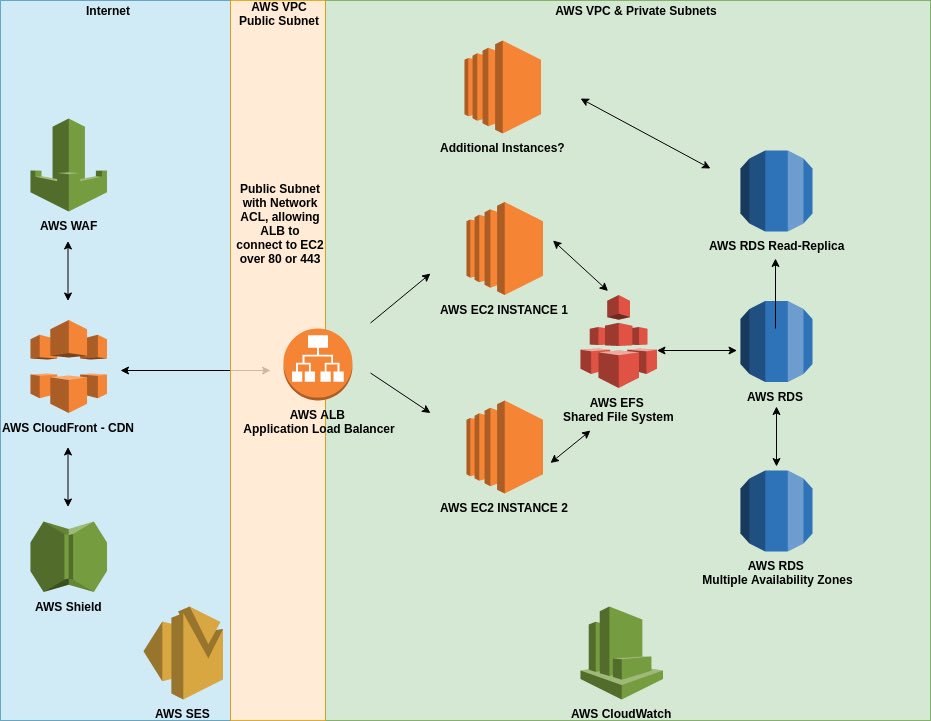
Another presentation that got my attention was about deploying MISP in the cloud. At first, this looks tricky but the way it was implemented is nice. The presentation was based on AWS but any cloud provider could be used. Fully automatic, with load-balancers, self-provisioning. Great project!
Finally, the day ended with some changes that are in the pipe for upcoming MISP releases. Some old code will be dropped, revamping of the web UI, migration to most recent versions of PHP, Python & more!
Thanks to an event like this one, you quickly realize that the MISP project became mature and that many organizations are using it on a daily basis (like I do).
[Update] Talks have been recorded. I presume that they will be online soon with presentations as well. Check the website.
