This is already the fourth edition of the Botconf security conference, fully dedicated to fighting malware and botnets. Since the first edition, the event location changed every year and it allowed me to visit nice cities in France. After Nantes, Nancy and Paris, the conference invaded Lyon. I arrived yesterday in the evening and missed the workshop (four of them were organised the day before the conference). The first started smoothly with coffee and pastries. What about this edition? Tickets were sold out for a while (300 people registered) and the organisation remains top. Eric Freysinnet did the open session with the classic information about the event. About the content, there is something important at Botconf: some talks contains touchy information and cannot be disclosed publicly. The organisers take the TLP protocol seriously. Each speaker is free to refuse to be recorded and his/her presentation to be covered on Twitter or blog (this is part of their social media policy. Of course, I’ll respect this. Last Eric’s remark: “No bad stuff on the wifi, there are some people from French LE in the room!” 😉
After Eric’s introduction, the first slot was assigned to Jean-Michel Picot from Google (with the collaboration of many others Googlers) who presented “Locky, Dridex, Recurs: the Evil Triadâ€. He presentation how those malicious codes are seen from a Gmail perspective. As said above, I respect the speaker’s choice: this talk was flagged as TLP:RED. It was interesting but (too?) short and some questions from the audience remained unanswered by the speaker/Google. More information could be found about their research here. For me, nothing was really TLP:RED, nothing touchy was disclosed.
The next talk was called “Visiting the Bear’s Den†by Jean-Ian Boutin, Joan Calvet and Jessy Campos (the only speaker present on stage). The “Sednit” group (also known as APT28, Fancy Bear or Sofacy) has been active since 2004. It is very active and famous.The analysis of Sednit started with a mistake from the developers: they forgot to set the “forgot” field on bit.ly. The URL shortener service was indeed used to propagate their malicious links. Basically, Sednit uses an ecosystem based on tens of software components like RAT’s, backdoor, keyloggers, etc). To explain how Sednit works, Jessy had a good idea to tell the story of a regular user called Serge. Serge is working for a juicy company and could be a nice target.
09:30 AM, Monday morning, Serge arrives at the office and reads his emails. In one of them, there is a link with a typo error and an ID to identify the target. Serge meets then SEDKIT (the exploit kit). On the landing page, his browser details are disclosed to select the best exploit to infect him. Serge’s computer is vulnerable and he visits the SEDNIT Exploit Factory. The exploit downloads a payload and Serge meets now the SEDUPLOADER. The dropper uses anti-analysis techniques, drops the payload, performs privilege escalation and implements persistence.
10:00 AM: Serge is a victim. SEDRECO deployment.
02:00 PM: Serge meets XAGENT (the modular backdoor). At this step, Jessi explained how communications are performed with the C&C. It works via SMTP. Messages are sent to created or stolen mailboxes and the C&C retrieves the messages:
Victim > SMTPS > Gmail.com < POP3S < C&C > SMTPS > Gmail.com < POP3S < Victim
What’s happening during the next three days? Modules are executed to steal credentials (via Mimikatz!), registry hives are collected. Note that multiple backdoors can be installed for redundancy purposes. Finally, lateral movement occurs (pivoting)
Friday, 11:00AM, long term persistence is implemented via a rogue DLL called msi.dd which is used by Microsoft Office. When an Office component is started, the rogue DLL is loaded then loads the original one (they offer the same functions). Finally, the DOWNDELPH bootkit was explained. This was a very interesting talk with many information. For more information, two links: the research paper and a link to Sednit IOC‘s if you are interested in hunting.
After the lunch break (which was very good as usual at Botconf), Vladimir Kropotov and Fyodor Yarochkin presented “LURK – The Story about Five Years of Activityâ€. Sednit was covered in the morning and this talk was almost the same but about “LURK“. It is a banking trojan targeting mainly Russia and the group behind it is active for a few years. The research was based on the analyse of proxy logs. It was first detected in 2011 and was the first to have a payload residing in memory (no traces, no persistence). It is easy to identify because malicious URLs contains the following strings:
- /GLMF (text/html)
- /0GLMF (application/3dr)
- /1GLMF (application/octet-stream)
Those can be easily detected via a simple regular expression. Vladimir & Fyodor reviewed the different waves of attacks and how they infected victims from 2012 to 2014. A specific mention for the “ADDPERIOD” abuse which is a flag set to a domain during registration. When the owner would like to cancel the DNS, the price can be refunded. Web sites are infected via memcache cache poisoning or an extra module added to the Apache web server.How to infect websites? Note that, in 2012, No antivirus on VT was able to flag LURK samples as malicious (score: 0). The talk ended with a video recorded by the Russian police when the LURK owners were arrested.
Then Andrey Kovalev and Evgeny Sidorov presented “Browser-based Malware: Evolution and Preventionâ€. This is not a new type of attack. MitB (“Man in the Browser“) is an attack where hooked interaction changes the information on the rendered page like adding some Javascript code). Targets are banking sites, mail providers or social networks. In 2013, there was already a talk proposed by Thomas Siebert from GData about this topic). There are many drawbacks with this kind of attack:
- Browser upgrades may break the hook
- App containers make the injection more difficult
- A web injector process has to be in the target system
- They are evidences (IOC’s)
- AV software are getting better to detect them.
So, can we speak about MitB-NG or MitB 2.0? They are performed via malware or adware browser extensions, WFP or remote proxies. Don’t forget VPN end-point or Tor exit-nodes that can inject code! The next part of the talk was dedicated to the Eko backdoor and SmartBrowse. So, what about dDetection and prevention? CSP (“Content Security Policy“) usually used to make XSS harder can be useful. JavaScript validation can be implemented in code. The JS checks the page integrity (like file hashes). Conclusions: there are new challenges ahead and the extension stores should implement more checks. Finally, browser developers should pay more attention to mechanisms to protect users from rogue extensions (with signatures), AV should give more focus on extension and not only droppers.
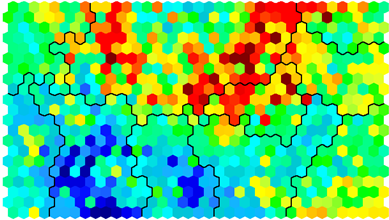
The next talk was titled “Language Agnostic Botnet Detection Based on ESOM and DNS†and is the result of the research performed by a team: Urs Enliser, Christian Dietz, Gabi Drei and Rocco Mäandrisch. The talk started with the motivations to perform such research. Most malware uses DGA or “Domain Generation Algorithm”. If this algorithm can be reversed (sometimes it is), we are able to generate the list of all domains and build useful lists of IOC’s. The approach presented here was different. Why not use ESOM (“Emergent Self-Organising Maps“) to try to detect malicious domains amongst all the DNS traffic? The analysis was based on the following steps:
- Extract language features from domain names in data samples
- Run ESOM training
- Categorise domain names from real live traffic with ESOM map
Here is an example of ESOM output:
The magic behing ESOM was explained but, for newbies like me, it was difficult to follow. I’d like to get a deeper introduction about this topic. The research is still ongoing but it looks promising.
The afternoon coffee break was welcome before the last set of presentations.  Victor Acin and  Raashid Bhat came on stage to present “Vawtrak Banking Trojan : A Threat to the Banking Ecosystemâ€. Vawtrak is in the wild for a while. It is performing MitB (see above) and is very modular & decentralised. Know before as Neverquest. The malware internals were reviewed (LZMAT compression, 32 & 64 bits versions, XOR encoding, etc) as well as the configuration containing C&C servers, botnet configuration, version, sign keys). By default, it injects itself into explorer.exe and iexplore.exe then in the child processes. After a review of the infection processes and all techniques used, the speakers reviewed the communications with the C&C. Vawtrak is a modular trojan. Multiple plugins provide opcode / API interface. Some statistics were disclosed and look very impressive:
- Used by 2 groups
- 85k botnet infections
- Top-5: US, Canada, UK, India, France
- 2.5M credentials exfiltrated
- 82% of infection are in USA
- 4000 identified IOC’s
- Win7 is the most affected OS
- 2058 infections on windows server 2008
Then, Wayne Crowder presented “Snoring Is Optional: The Metrics and Economics of Cyber Insurance for Malware Related Claimsâ€. Not a technical talk at all but very interesting! Wayne’s exercise was to try to talk about botnets not from a technical point of view but from a cyber-insurance point of view. An interesting statistics reported by Wayne:If
If cybercrime had been a US company in 2014 it would have been the 2nd largest…
From an insurance perspective, more  malware samples mean more risks of data leak and more costs for the company. Insurance drives safety & security in many domains and it will follow this trend in cyber security for sure. What’s covered? Data theft (PII, cards, health data,), malwares, DDOS, hacking, business interruption, phishing, extortions, mistakes. What must cover a good policy?
- Legal damages
- Crisis
- PCI (or similar) fines
- Availability
- Extortion
- “cyber related perils†(who said “IoT”?)
The talk was clearly based on the US market and Wayne gave a lot of statistics. But, keep in mind that this could change in the EU zone with the new notification law coming in 2018 (GDPR) . Wayne also reviewed several cases where cyber insurance was involved (with nice names like Sony, Target, hospital ransomware, …). Not that not everything is covered (brand, reputation, state sponsored hacking). Very interesting and I’m curious to see how the cyber-insurance market will evolve in the (near) future.
The last talk was “Hunting Droids from the Inside†by Lukas Siewierski, also from Google. This was given again under TLP:RED.
That’s all for the first day and stay tuned for a new wrap-up. Don’t forget that some talks are streaming live via Youtube.


RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6
RT @xme: [/dev/random] #Botconf 2016 Wrap-Up Day #1 https://t.co/4OhEhaRTm6