 In a previous post, I explained how I was happy to have been targeted by Indian phishers who called me to report an issue with my Windows computer. Last Saturday they called back. This time, my VM was ready but I had no time for them. I asked if it was possible to call me back later and they approved! This morning, they called back as promised!
In a previous post, I explained how I was happy to have been targeted by Indian phishers who called me to report an issue with my Windows computer. Last Saturday they called back. This time, my VM was ready but I had no time for them. I asked if it was possible to call me back later and they approved! This morning, they called back as promised!
[Note to some operators and manufacturers, they provide better support then you because they really take care of their “customers” ;-)]
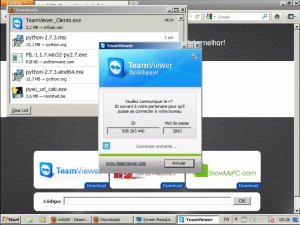
When the phone rang, I was not ready but they called again five minutes later. VM? Check! Recording? Check! The scenario is always the same: The “operator” presents himself and asks you if you are in front of your computer. The guy on the line was speaking a very bad english. Impossible to understand the URL he spelled. He forwarded me to a colleague. Let’s go! He asks you first some basic questions to ensure that you’re in front of your computers (and do this all the time during the conversation). Then he asked me to press “Windows-R” and to type an URL: hxxp://www.supportbe.webs.com. It did not work, no problem: he had plenty of alternatives. The second URL was ok ( hxxp://www.infosis.net). From this site, he asked me to download a TeamViewer client and to execute it. It took a long time because my VM did not had a direct access to the web, I had to change the proxy settings live. Once started, the client was unable to contact the Team Viewer servers due to the firewall. Again, I changed this on the fly. Honestly, those guys are really patient! Once the ID and password communicated, the fun began!
First remark, they are keyboard masters! The mouse did not move and they handled the Windows interfaces very quickly. He started a command line and the first command executed was “netstat“. According to the operator, all the “ESTABLISHED” lines were connections back to the hackers, booooh! The next one was “tree” which is used to display the content of the system disk in a directory tree. While the system tree was display, he simple typed (or pasted) a nice string which was display after the command completion:
Windows Software Warranty Expired!!!!!........
His comments: “You see Sir, your computer is not protected anymore by Microsoft“. And we went further with another command. The operator started a “certmsg.msc” and he showed me that the “Microsoft Authenticode(tm) Root Authority” was expired since 2000! Too bad!;-) Same dialog again, the operator tried to convice me that it is very bad for my computer and my security. Next step: he proposed to download and use Chrome only. While the download and installation of the browser, he told me that it will cost me $20 to clean up my computer. I agreed, of course 😉 The next question which immediately came was: “Do you use e-banking applications? Could you log on to pay the $20?“. I explained that it was not possible right not arguing that my wife left the home with my Digipass to sign the transaction. My goal was to try to gain some time to prepare a scenario. While discussing, he started the “syskey” tool then… hanged up the line!
Here is a recording of my virtual machine. The interesting stuff starts at 08:15. Enjoy!
I was also called, I panicked after I downloaded there app from infosis.net and saw they were putting in passwords, I’m not that advanced and just switched off the PC, and they hung up, then I phoned the bank and stopped all transactions, my big question is, how did they get my land line no and why can no authorities, use this info to trace them and prosecute, criminals , if I did not stop all my acc would they have been able to get old history of my internet banking info and use that to clean out my acc? What now, I’m scared to go back on the internet as I don’t know how to remover their software?
Damn. we’re naturally protected – no one here would beleive the helpline to answer back.
@xme unbelieveable they continued despite the amount of red flags: windows classic theme, empty desktop, resolution, your download history..