 Today, the second edition of “Security Friday” was held in Brussels. As mentioned on the website, the goal is “a gathering of people in the IT security field. Getting together for a drink on the last Friday of the month in a bar near you we talk amongst peers about IT security, non-tech hobbies, favorite beers, and much more“. I like such initiatives because sharing is the key of information security. Maintaining your social network is mandatory! And yes, IT people are social, not always hidden in dark rooms just illuminated by screens! 😉 So, I went to the chosen pub to have some interesting chats and drinks with some Belgian infosec folks (know faces of course). If you’re interested, keep in mind: the last Friday every month!
Today, the second edition of “Security Friday” was held in Brussels. As mentioned on the website, the goal is “a gathering of people in the IT security field. Getting together for a drink on the last Friday of the month in a bar near you we talk amongst peers about IT security, non-tech hobbies, favorite beers, and much more“. I like such initiatives because sharing is the key of information security. Maintaining your social network is mandatory! And yes, IT people are social, not always hidden in dark rooms just illuminated by screens! 😉 So, I went to the chosen pub to have some interesting chats and drinks with some Belgian infosec folks (know faces of course). If you’re interested, keep in mind: the last Friday every month!
Amongst the multiple topics that were discussed, one of them was the risk associated with VPNs. This is what I call the “VPN Grey Zone“. Let me explain the problem: My beloved Macbook follows me almost everywhere and, when connected to untrusted network – read: almost everywhere – I’m using a VPN to phone home. But when you wake up your Macbook, you already have plenty of applications running and they are just waiting for some network connectivity. Once you open the Macbook, traffic is generated before your VPN session is established. And during this short period of time, very sensitive information could be sent to the untrusted network. This is what I call the “VPN grey zone“. You don’t know exactly what’s sent in the wild!
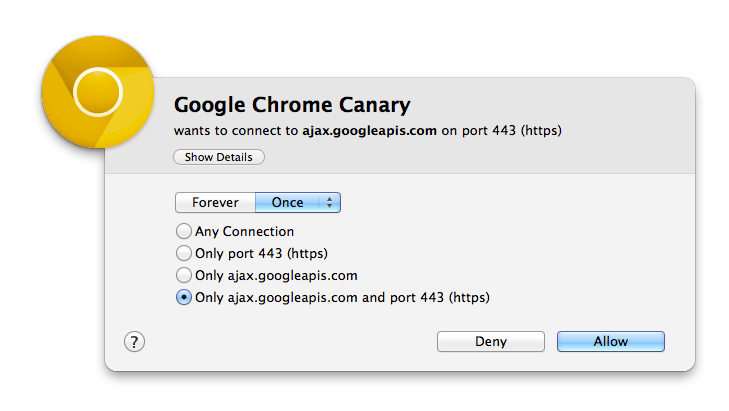
To prevent this problem, I’m using intensively a nice feature provided by Little Snitch. If you have an Apple computer, this is a must have tool! Little Snitch is a firewall dedicated to outgoing traffic. Every time an application tries to open a network connection, a pop-up is displayed asking you to allow or deny this connection:
Since the version 3.1, Little Snitch introduced a very nice feature called “Automatic Profile Switching“. Its goal is to automatically assign network to certain profiles. Networks are, by example, unknown Wi-Fi networks, your home or corporate LANs, etc. But wait, OS X has also a notion of “network profiles”. You can assign a specific configuration (DHCP, fixed IP, DNS, …) to networks. Nice but the Little Snitch profiles allow you to specifiy which traffic will be autorized or not. Example: at home, you will allow your Dropbox client to connect but, when connected to your corporate network, it will be silently blocked to not alert the firewall guys!
In the Little Snitch terminology, what is a network and a profile? A profile is a set of rules which define which process may (or not) connect to an IP and/or this port. A network is identified by:
- The type (Ethernet, Wireless)
- The router IP address
- The router MAC address
- Geolocalisation (optional)
To come back to our “VPN grey zone“, let’s fix the issue by creating two profiles:
- Trusted
- Untrusted
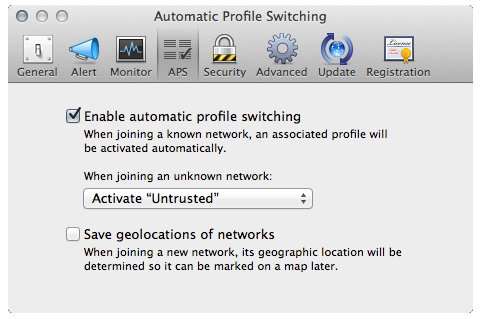
The profile “Untrusted” will contain no rules and will be assigned by default when joining unknown networks as seen in the screenshot below:
The profile “Trusted” will contain your rules to allow applications to use network resources and will be assigned to your VPN connection. No more traffic sent in the wild a few second before the VPN session is established (or re-established if dropped). Later, create new profiles for locations that you visit on a regularly basis!
Little Snitch is not a free software but it’s worth the price, definitively! If you’re using similar tools & configurations with other operating systems, please share!
What if Little Snitch starts running *after* you have started network connections? Like on system boot maybe ?
RT @xme: [/dev/random] OS X: How to Avoid the VPN “Grey Zone”? http://t.co/8deifnM6Ng