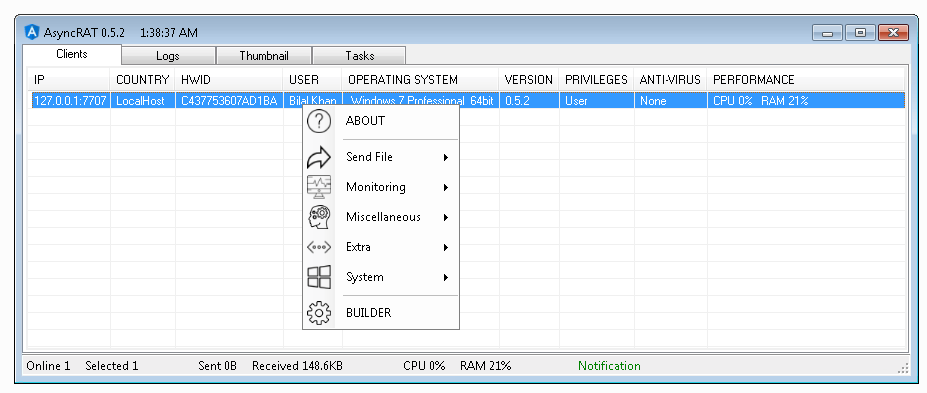
I published the following diary on isc.sans.edu: “From VBS, PowerShell, C Sharp, Process Hollowing to RAT“:
VBS files are interesting to deliver malicious content to a victim’s computer because they look like simple text files. I found an interesting sample that behaves like a dropper. But it looks also like Russian dolls seeing all the techniques used to drop a RAT at the end. The file hash is 8697dc74d7c07583f24488926fc6e117975f8a9f014972073d19a5e62d248ead and has a VT score of 12/59. It was delivered by email under the name “Procurement – Attached RFQ 202102.vbs”. If you filter attachments based on the MIME type, this file won’t be detected as suspicious… [Read more]