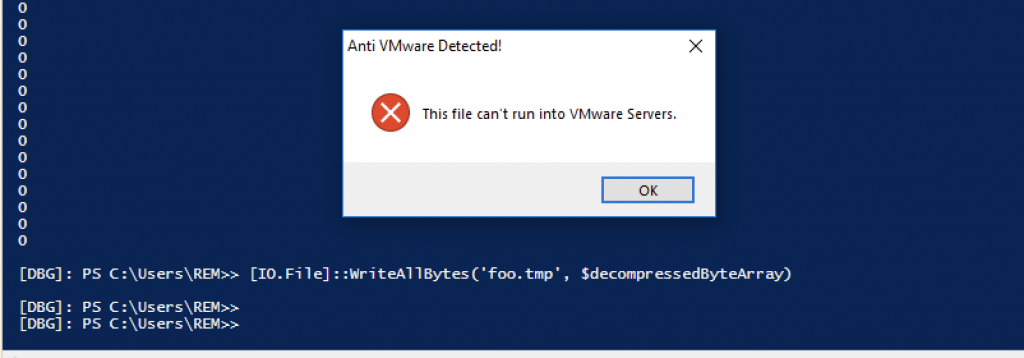
I published the following diary on isc.sans.edu: “PowerShell Dropper Delivering Formbook“:
Here is an interesting PowerShell dropper that is nicely obfuscated and has anti-VM detection. I spotted this file yesterday, called ‘ad.jpg’ (SHA256:b243e807ed22359a3940ab16539ba59910714f051034a8a155cc2aff28a85088). Of course, it’s not a picture but a huge text file with Base64-encoded data. The VT score is therefore interesting: 0/61. Once decoded, we discover the obfuscated PowerShell code. Let’s review the techniques implemented by the attacker… [Read more]