One of my sources of threat intelligence is a bunch of honeypots that I’m operating here and there. They are facing the wild Internet and, as you can imagine, they get hit by many “attackers”. But are they really bad people? Of course, the Internet is full of bots tracking vulnerabilities 24 hours a day and 7 days a week. But many IP addresses that hit my honeypots are servers or devices that have just been compromised.
To get an idea of whose behind these IP addresses, why not try to get a screenshot of available web services running on common ports? (mainly 80,81,8080,8088,443,8443,8844, etc). Based on a list of 60K+ IP addresses, I used Nmap to collect screenshots of detected web services. Nmap has a nice script to automate this task.
Once the huge amount of screenshots generated, I searched for an idea to display them in a nice way: a big “patchwork” of all images. Here is the resulting image:
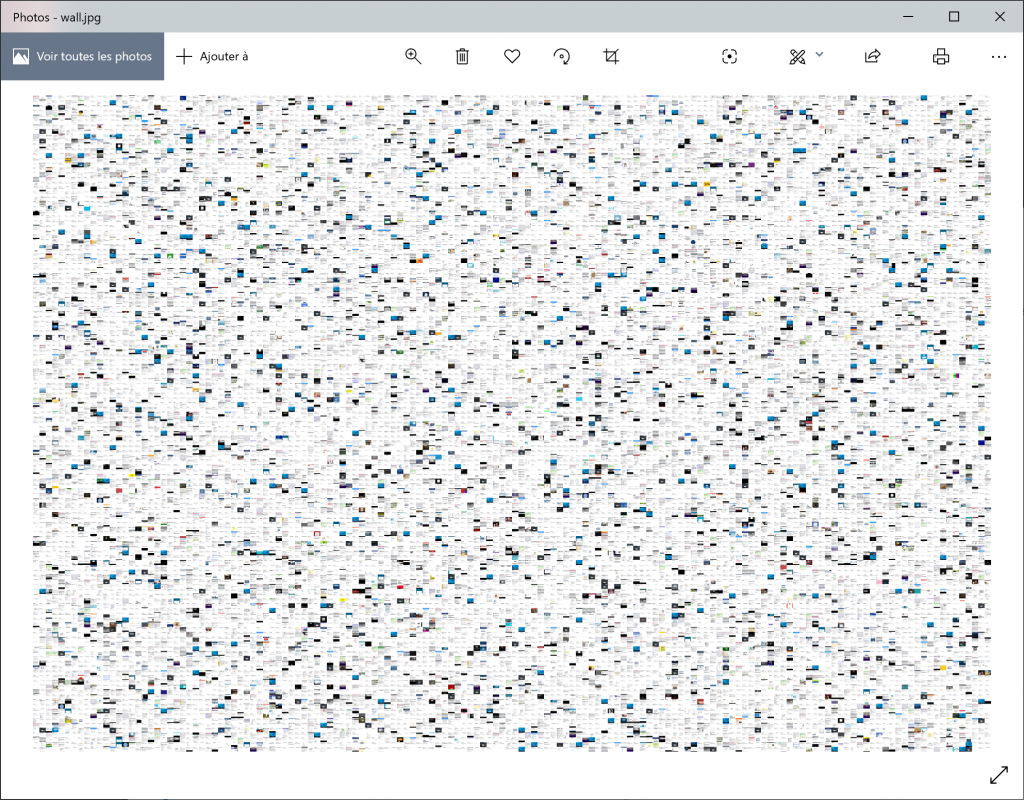
The final picture is quite big:
- Contains 20599 screenshots
- 223MB
- 60000 x 41100
It can be zoomed in and out to browse the screenshots for fun:
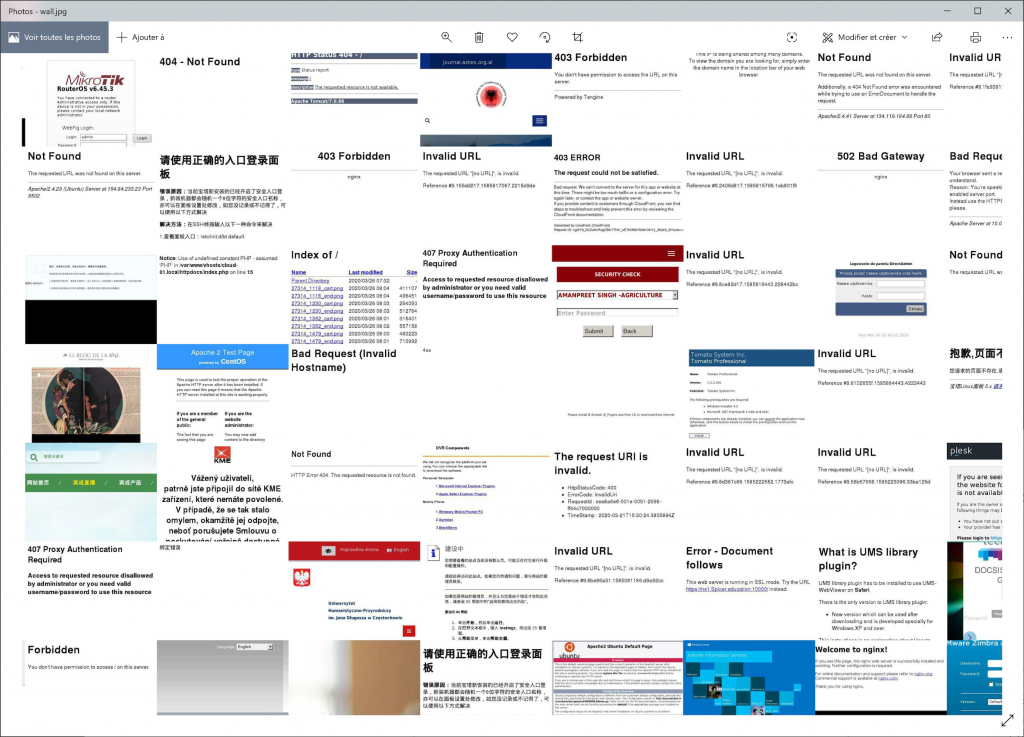
To generate this patchwork image, I used a few lines of Python code together with the Pillow library. Images have been resized and “white” images removed (because the Nmap script does not work well with technologies like Flash).
I won’t share the full picture because it contains sensitive information like files listing, admin interfaces and much more. Based on screenshots, many IP addresses run open interfaces, interfaces with default credentials or unconfigured applications (like CMS). Some screenshots reveal corporate organizations. This is probably due to NAT in place for egress traffic generated by compromised internal hosts. As you can imagine, some interfaces reveal critical services. Some examples?
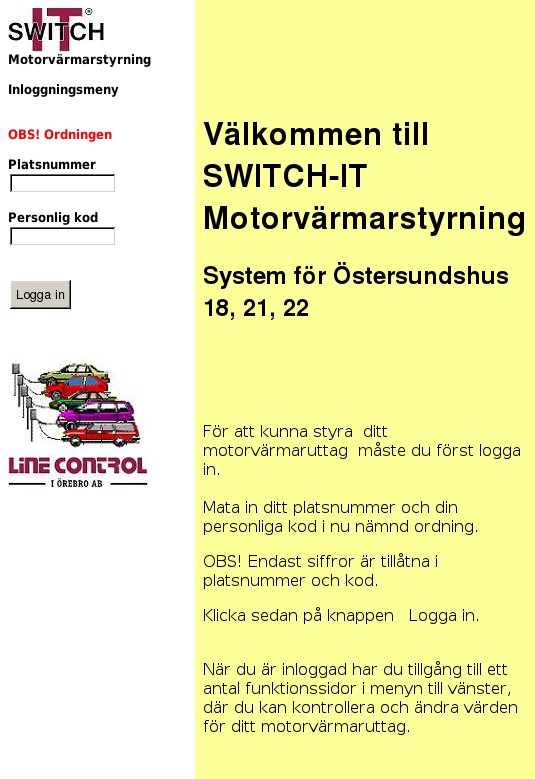
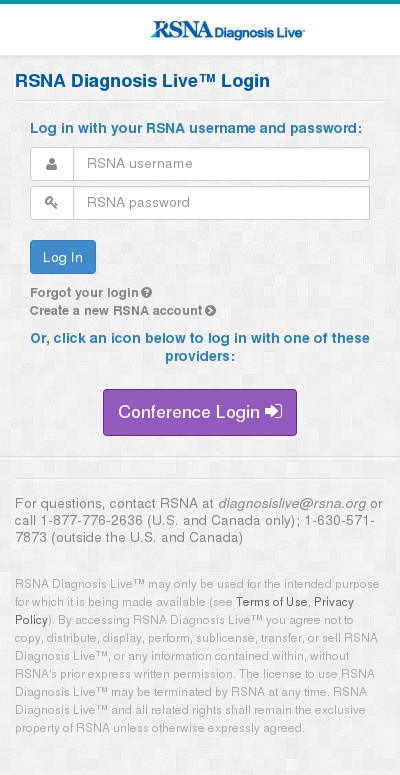
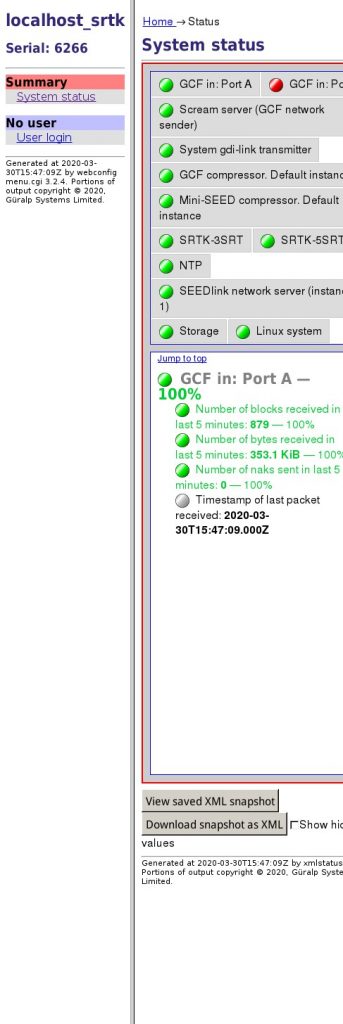
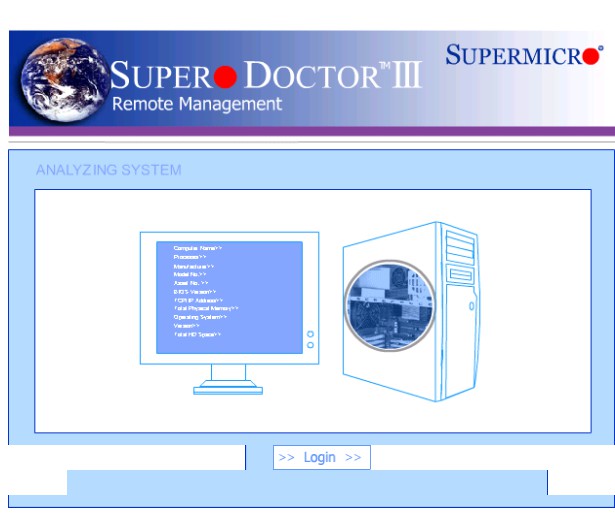
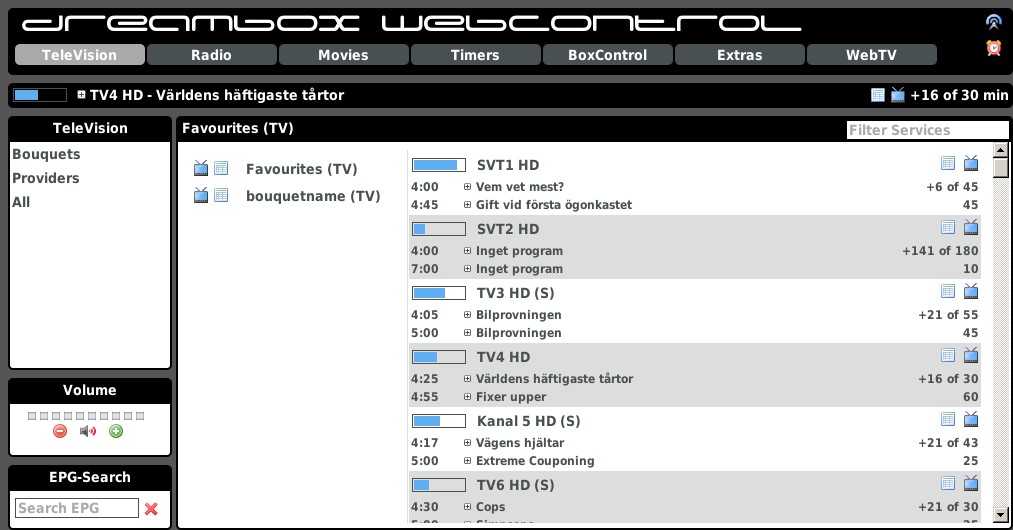
If you’re interested to generate such kind of big images, the script I write is available on my GitHub repo. Don’t blame me for the quality of the code 😉